F5 and Robust Intelligence Partner for Leading-Edge AI Application Security
In the vanguard of technological evolution, artificial intelligence (AI) is revolutionizing business operations and customer interactions across every industry. Yet, as organizations integrate AI deeper into their core processes, the specter of AI-specific security vulnerabilities looms large. New safety and security risks have and will continue to surface.
To address this emerging threat landscape, F5, the leader in multicloud application security and networking services, has joined forces with Robust Intelligence, an AI security pioneer, to forge a path toward a secure AI-enabled future. This partnership equips customers with the tools necessary to confidently deploy AI applications and ensure security without sacrificing innovation, speed, or performance.
Understanding the AI Security Conundrum
The proliferation of AI has brought with it a new genre of threats that conventional security frameworks struggle to manage. AI applications are susceptible to novel forms of AI threat exploitation, such as adversarial attacks that manipulate machine learning models, or subtle prompt injections that can skew AI outputs. It’s no longer an expected input with a programmed output on a webpage; users can ask any question or request any tasks to be executed.
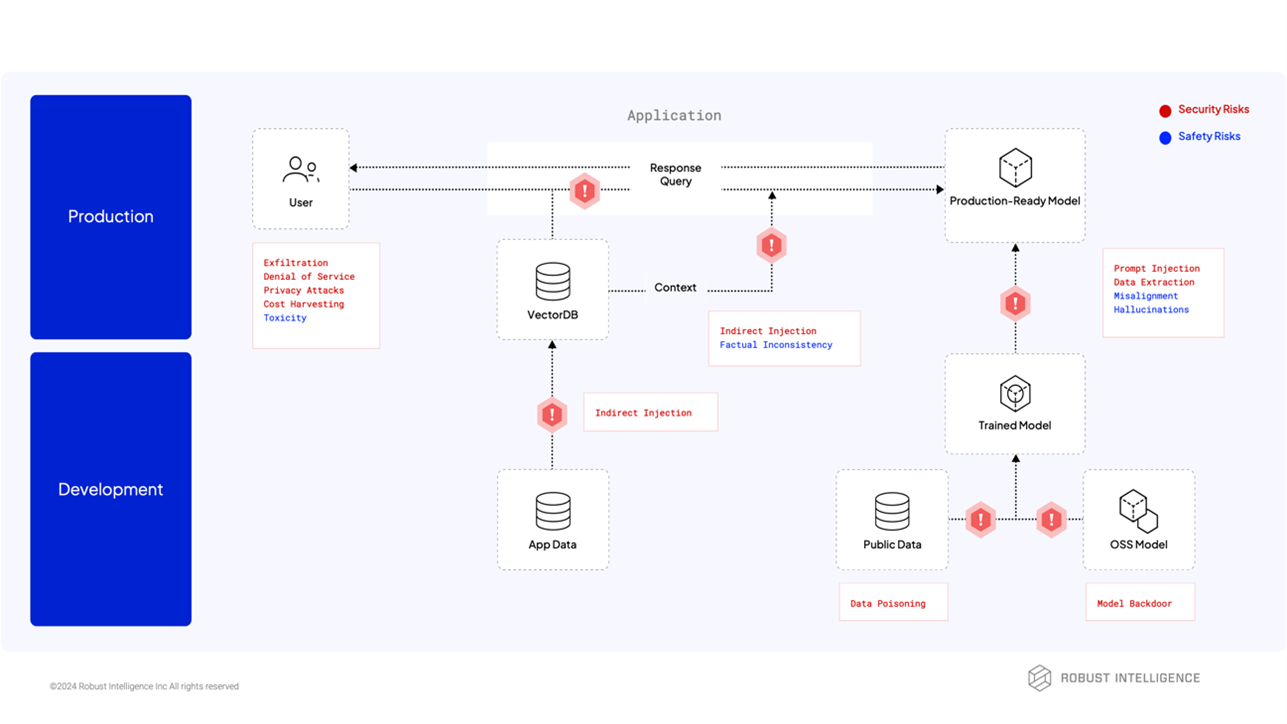
At a high level, AI applications are susceptible to two categories of risk: safety risk and security risk.
Safety risks are typically unintended outcomes or abuse of an AI application. These include repurposing an AI application for malicious purposes, alignment issues, biased or toxic outputs, and hallucination.
Security risks are those that jeopardize an organization's sensitive data and computing resources. Mirroring the three principles of cybersecurity, AI security risks may violate confidentiality (resources only available to authorized parties), integrity (resources remain consistent and accurate), and availability (resources remain accessible to authorized parties).
The consequences of unmanaged AI risks can lead to significant financial and reputational damages, litigation, non-compliance, IP leakage, and more. The need for specialized security measures becomes imperative as AI applications become more integral to business functions.
A Synergistic Approach to AI Application Security
As trusted leaders in each respective field, F5 and Robust Intelligence are partnering to address the unique safety and security challenges posed by AI. The integration of F5’s AI security suite and Robust Intelligence’s cutting-edge AI Firewall provides businesses with a comprehensive security solution designed to protect both traditional and AI applications from an array of risks while maintaining efficiency and agility.
F5 Distributed Cloud Web Application and API Protection (WAAP) encompasses a broad spectrum of security solutions, including Web Application Firewall (WAF), Bot Defense, DDoS Mitigation, and API Discovery/Security. These solutions thrive at safeguarding digital assets across any environment, from data centers and clouds to the edge.
The integration of Robust Intelligence's AI Firewall into the F5 Distributed Cloud Services ecosystem strengthens this security posture even further and provides real-time coverage to AI enterprise applications. The AI Firewall scrutinizes the inputs and outputs of AI applications instantly to determine the legitimacy of interactions. It identifies and blocks potential threats, ensuring that AI models operate within safe parameters and are not manipulated by malicious actors.
The benefits include:
- Mitigating attacks targeting AI systems.
- Ensuring the safety of model outputs.
- Maintaining compliance with leading standards such as MITRE, NIST, and OWASP Top 10 (web apps, APIs, and LLMs)
- Integration with existing security and monitoring tools (for example, SIEM).
For customers that choose to also use Robust Intelligence’s AI Validation for algorithmic red teaming, AI Firewall protection is enhanced by the ability to automatically generate guardrails specific to the security and safety vulnerabilities inherent in each model—thereby extending security coverage from development through production.
Conclusion
As AI reshapes the digital world and the way we do business, security leaders must proactively reimagine their organizational strategies to accommodate a new paradigm of risk. Security is no longer just about keeping up.
Through our collaboration, F5 and Robust Intelligence offer not only immediate protection but also the capacity to evolve with the AI threat landscape. Together, we are empowering organizations to harness the transformative potential of AI while having the peace of mind that their innovative technologies are safe and secure.
To get started, please email robustintelligence@f5.com.
To read Robust Intelligence’s press release, please visit here.
To see a demo of Robust Intelligence + F5 Distributed Cloud Services, please watch https://www.youtube.com/watch?v=nLt1uMz41AQ.
To better understand how F5 Distributed Cloud Services can help organizations build infrastructure for any application anywhere, please visit https://www.f5.com/cloud.