In this series, we examine how the reality of a security program differs from the perception some security practioners hold. To do this, we’re focusing on four specific gaps that can weaken security defenses and instigate security incidents. For example, consider the rising number of cloud breaches caused by engineers disabling basic access control, either by accident or by intention. Why does this happen? More specifically, what perceptions and work routines could enable these kinds of things to happen?
In part 1, we examined three key gaps previously discussed by F5 Labs research in the past year: how incomplete inventory practices lead to weaken risk management, how risk appraisal can become biased, and how risk mitigation can get misaligned from top threats. In part 2, we will explore a new, previously unreported mismatch in cyber security practices.
The CISO and SecOps
As security grows in importance within an organization, security leaders find their reach and governance responsibilities have grown. Two years ago, we published a research report on research report on how CISO’s work with the organization. It showed a growing trend of CISOs moving out from under IT umbrella and into general business risk positions. Overall, we feel this is a natural and an effective evolution of the CISO role—but it is not without complications.
As part of the F5 Labs 2018 Application Protection Report, we commissioned the Ponemon institute to survey thousands of security professionals across the world from all security-related roles within the enterprise. For most of the report, we used either survey answers from security leadership (where leadership questions would apply) or in aggregate between the high-level roles and the technician roles. But this is the first time we have disclosed findings on the gap between how security leaders answered and how technicians answered.
First, however, let’s talk about the survey itself. We asked about individual roles within the organization and used those answers to build a profile showing whether they were a leader, a technician, or both. Table 1 breaks down how this looked.
| Which of the following best describes your role in the IT security function within your organization? Check all that apply. | Overall answers | Role type | Respondents classified “Leader” who picked this role | Respondents classified “Technician” who picked this role |
| Setting IT security priorities | 50% | Leader | 60% | 33% |
| Determining IT security strategy | 40% | Leader | 53% | 17% |
| Assessing IT security risks | 60% | Both | 65% | 52% |
| Developing software applications | 28% | Tech | 21% | 40% |
| Implementing enabling security technologies | 52% | Tech | 45% | 63% |
| Managing IT security spending | 35% | Leader | 46% | 16% |
| Evaluating vendors and contractors | 47% | Leader | 56% | 31% |
| Selecting vendors and contractors | 39% | Leader | 47% | 26% |
Our overall survey was aimed at security leaders, but we did get a considerable number of technicians answering. Overall, out of 3,135 final acceptable surveys, we classified 2,001 as security leaders (63.87%) and 1,134 as technicians (36.2%).
When we crunched all the data and looked for answers where there was statistical significance between how the two role types answered the survey, we saw a divergence in certain areas between leadership’s perspective on security and the technicians’ perspective. Most of the answers aligned across all roles or at least were very close. This made the answers with a gap really stand out. Some of the gap responses were present in inconsequential areas, such as stack-ranking app threats.
Storage Encryption for Data and Applications at Rest
The first gap we found had to do with a critical control for leakage of data: storage encryption for data and applications at rest. This is an interesting set of responses, because when we asked about transmission encryption there was only a 2% margin of difference between the answers given by leadership and technicians. However, we found that CISOs were 9% more certain about their storage encryption coverage than technicians.
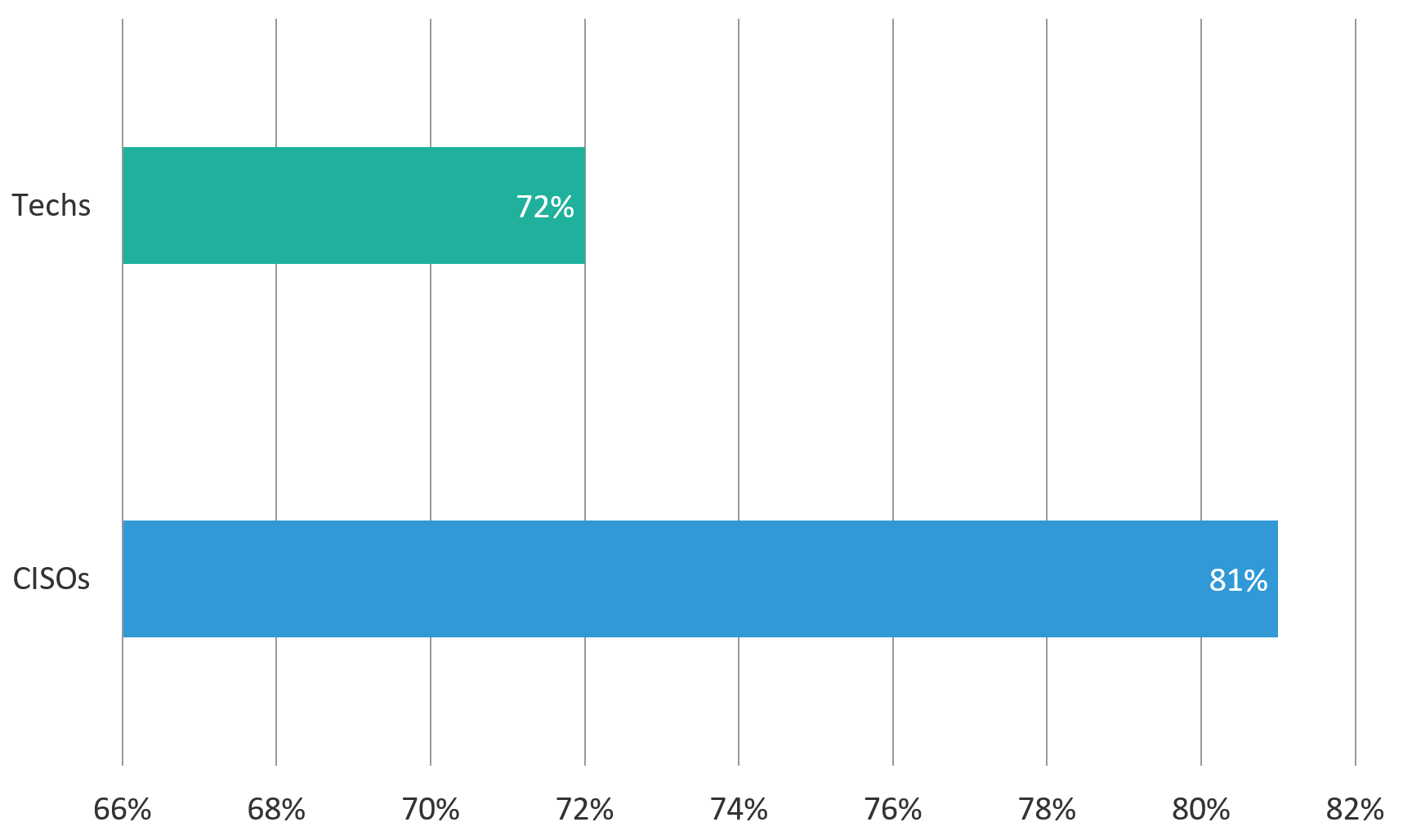
This disparity is a little worrying because the importance of this control to reduce confidentiality breaches is quite high. Storage encryption is sometimes the first and last line of defense against common threats such as lost laptops, a pwned databases, or rogue internal employees. Also, it raises the question of who in the organization is more likely to truly understand if critical this control is in place: the CISO who (probably) owns the risk? Or the security technician, who may work directly with these systems on a day-to-day basis?
Where Applications Reside
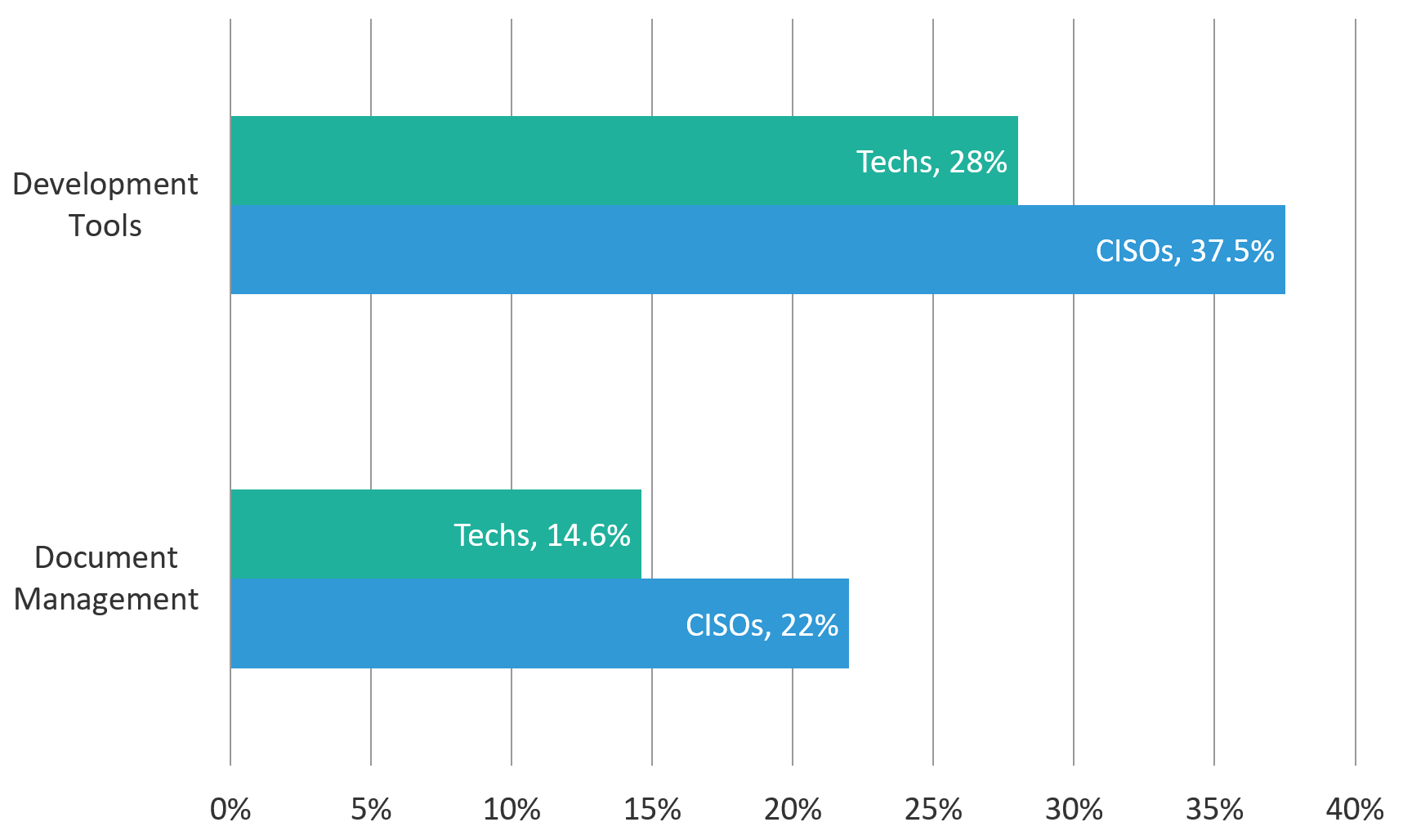
Our second gap ties back to another critical control: inventory and app visibility. In part one, we talked about how knowing the nature and the location of your applications is a linchpin for understanding and managing application risk. However, when we asked where various types of application were hosted, we saw a gap in answers for two kinds of applications: document management and development tools. In both cases, CISOs reported much lower percentages of apps hosted in a mixture of internal and external environments than technicians. The same doubts arise as to which role would have a better understanding of the true answer.
Biggest Barrier to Security
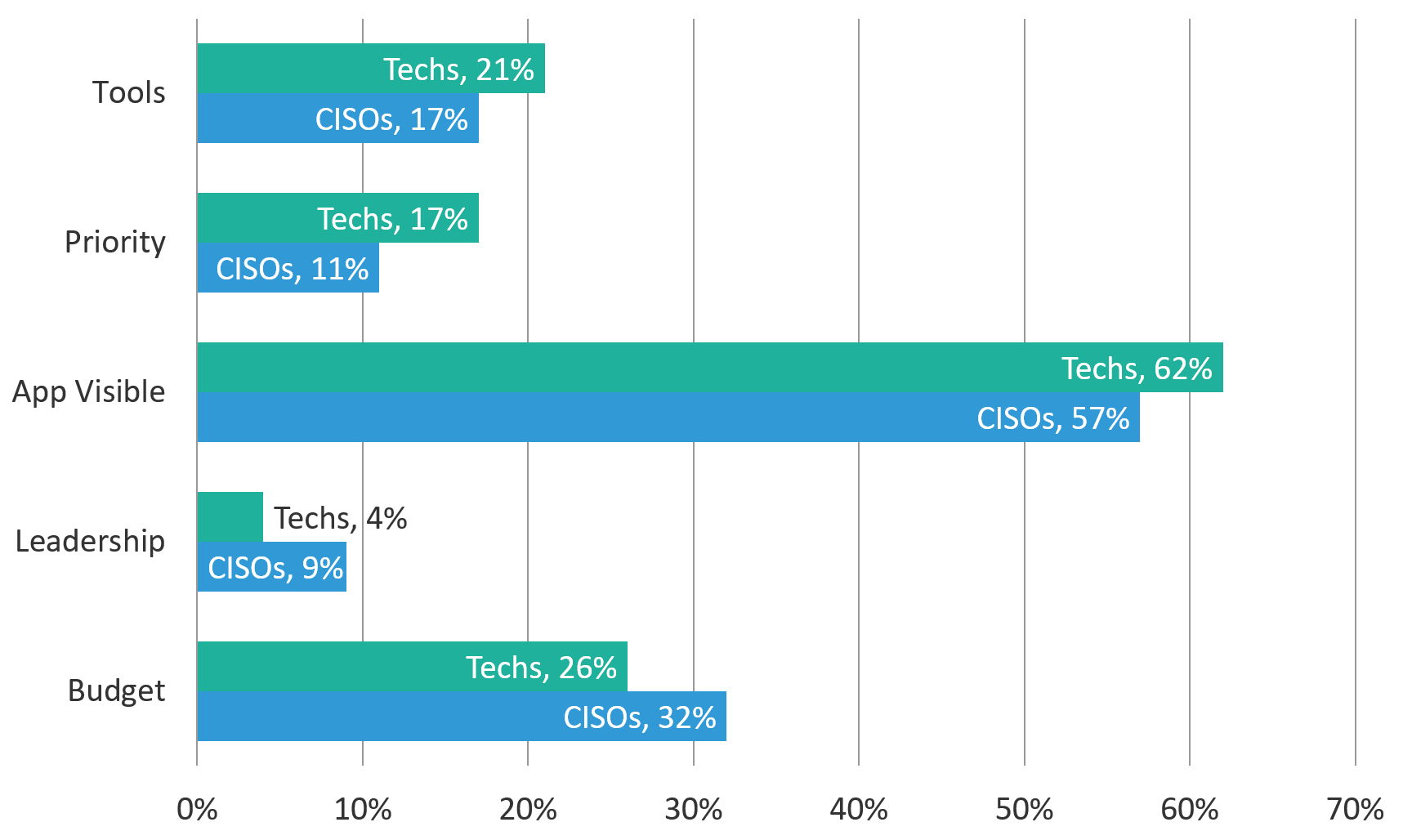
When we asked survey respondents to identify their biggest barrier in their security roadmap, we got a wide range of answers. In general, most people identified the lack of visibility in the app layers as the primary problem. However, there are some divergences between CISOs and technicians in the other answers. Figure 3 breaks out the specific answers by role. One interesting comparison is how CISOs see a lack of leadership as a bigger problem, whereas technicians are more concerned about a lack of priority. In some ways, these may be different interpretations of the same issue. Also, technicians want more security tools where CISOs want more budget—which may again be the same issue, interpreted differently by the two roles.
This Gap is a Danger Zone
A potential side-effect of this gap is blame being cast unnecessarily in both directions when security incidents happen, or audit findings are reported. If the leadership and those they lead are operating based on different understandings of reality, things will most certainly go wrong. And if each side assumes they have the correct point of view, it is natural for blame and mistrust to creep into the security organization. If the blame isn’t aimed at the roles or specific personnel, it could also be aimed at security processes or even tools.
What’s most likely, however, is that these gaps stem from badly-fitting processes or deficient information flows. Whatever the cause, they can be insidious as a poison to a security program.
Who Owns App Risk Governance?
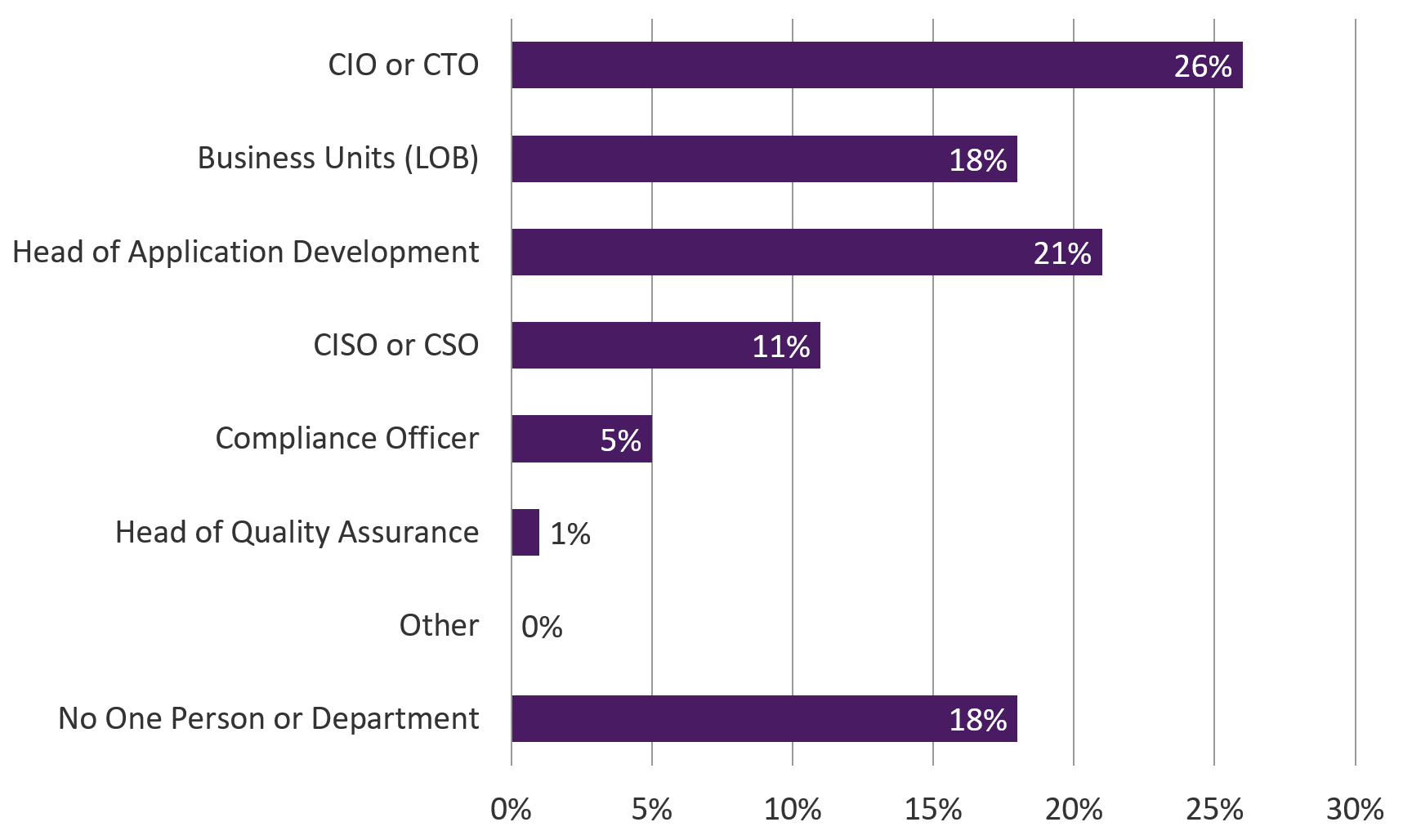
A possible source for conflicting information within a security program can be seen by examining the governance of the organization’s application security risk management process. One of our last questions in the survey was for respondents to identify the owners of that process. As shown in Figure 4, there was no consensus answer across any region, industry, and role.
As security guru Dan Geer has said, “There is nothing but ambiguity about who owns what risk.” Ownership is clearer when it comes to the traditional areas of cyber-risk such as endpoint protection, network security, and facility security. However, as applications become more and more central to critical business operations, ownership crosses more and more internal departmental lines. To defend these apps, decisions must be made to spend money, or to patch things—which gets difficult if no one knows who is responsible. Application security responsibility that is diffused and ambiguous will only aggravate these gaps in understanding. We’ve written more about this subject in our article Who Owns Application Security?
Stay Tuned
We’ve touched four in perceptions of cyber security practices and their real-world effectiveness. In our final installment, we’ll go deeper into the causes of these mental blind spots and offer actionable and practical solutions to prevent them.