There is no perfect defense. Even cutting the network cables between systems isn’t enough to stop attackers from getting in. Cybersecurity is a never-ending game of snakes and ladders; what worked today may fail tomorrow. Attackers are strongly motivated to invent new ways to sneak or smash their way into our networks and steal our stuff. As we’ve talked about before, we need to assume breach and realize that any control can be overcome.
If an attack can bypass a control, then we need to have secondary and tertiary controls in place to catch what we missed. Those controls should also work differently than each other, so the same attacker trick won’t work twice. The good news is that a set of diverse controls placed in-line against a threat can be highly effective, even if each single control is weak.
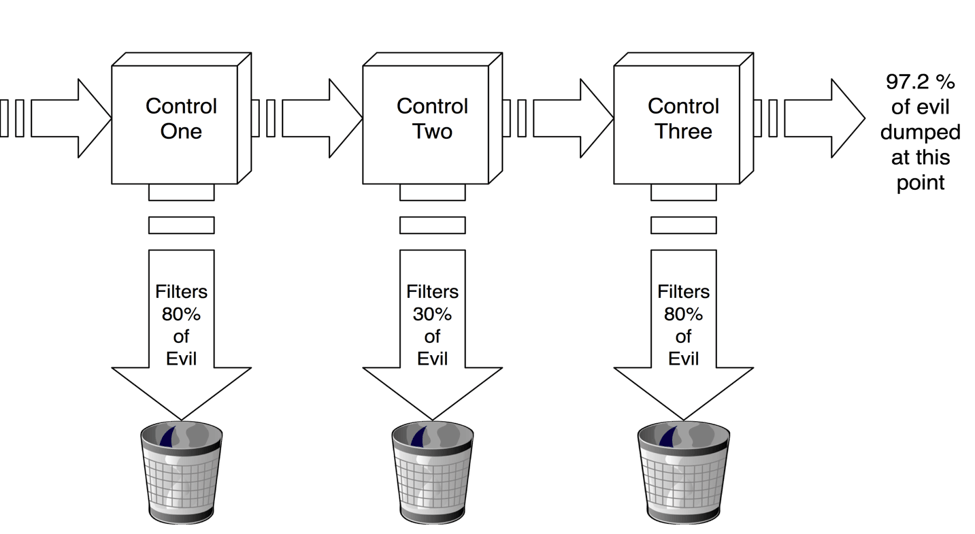
Consider the following diagram:
Say you’ve got a hundred attacks coming into your organization at a given moment. Control Number One filters out 80% of threats to give us only 20 attacks to worry about. Not bad. And then Control Number Two whacks nearly a third of those. Now the total has dropped to 13. Not a great control, but it still reduced things a bit. Finally, Control Number Three takes another 80% off that, dropping the number of attacks to just 3. By overlapping these three limited controls, you’ve created a single control that’s 97% effective.
So how does this work?
To begin at the beginning, you need to have a strong awareness of what assets need protecting and the primary threats to those assets. From here, you need to know what your highest risk items are. What threats poses the highest potential impact to the things you care about? Remember, this is a pragmatic approach—don’t waste energy defending things that don’t matter to you or against the threats that won’t do any actual harm.
Don’t get too caught up trying to demystify sophisticated attack campaigns. Instead, focus on what the potential goals of attackers could be and study their common tactics. For example, threat intelligence tells us there is a lot of business email compromise going on. A common tactic to do this is spear phishing, which is a tool of choice for both the basic scammer and sophisticated state actor. This gives us a clearly defined risk against which we can build defenses—and we know that these defenses will have a meaningful, positive impact on our security posture.
After identifying potential attack goals and tactics, you need to take stock of the controls and defenses you already have in place. Keep a careful eye on how a control works and what it specifically stops. Having three kinds of anti-virus endpoint software is different from having an anti-malware network filter, a software allowlisting solution, and an email attachment scanner. All of these are anti-malware controls, but only the latter list represents dissimilar controls that function differently. This diversity of control defense is what buys you the true defense in depth. An attacker may use a zero-day malware that no anti-virus software can detect, however an attachment blocker or allowlisting solution—which use different technologies—might find it. Or perhaps the malware will exhibit anomalous behavior that a network filter could detect. The idea is to try to solve the same problem multiple ways, hoping that at least one of the ways will trip up the attacker. It also raises the cost of attack, as the attacker will need to discover ways around three different methods, instead of just one.
It’s best to get creative when thinking about defense in depth. For spear phishing attacks, you could look at a wide range of stop-gaps such as email filters, user education, segregation of privilege, and multi-factor authentication. You may have noticed that against a spear phishing attack each of these controls has less-than-ideal stopping power by themselves, but the controls are also useful in blocking other kinds of attacks. This is where the efficiency of defense in depth really comes to bear. A good set of varied and flexible controls can curtail many different threats. When put all together, you’ve got an aggregation of smaller hurdles acting as a powerful barricade against many attacks.
Another analogy used to describe this defensive thinking is the “Swiss cheese model.”1 Imagine placing various slices of Swiss cheese in a line to block a ray of light passing through. Each barrier has holes, like Swiss cheese, but hopefully enough of them in aggregate will stop most attacks. Like our calculation above, the Swiss cheese model also warns that sometimes the holes of the slices will align for a particular threat and thusly, a few things will slip through every barrier. As in the calculation above, 97% effective still means 3% of attacks get through. No defense is perfect. That is why you need to include some detective and restorative controls as part of defense in depth.
Remember, you need to assume breach. If an attack succeeds, you need to be able to contain the damage and recover from the attack. You need to avoid cascade failures, where a single attack—such as a spear phish—captures a user’s credentials. You don’t want that attacker to use those credentials to escalate those privileges to a system administrator and then gain unfettered access to key data stores and systems. If the first set of controls can’t stop the attack, then maybe a secondary control can sound the alarm. Another secondary control in this scenario could be network segregation that requires additional authentication to bypass—as a firebreak—to keep the phished user from going too deep.
There is no cut-and-dried checklist on what controls and defenses to leverage. It’s going to vary based on your organization’s business, technological infrastructure, culture, and relevant threats. The key is analyzing and understanding the threats you face and the assets you care about, and then applying divergent but overlapping controls to remediate as much risk as you can. The good news is that a coordinated collection of useful but imperfect defenses is not only more effective than a single bulletproof control, it’s a lot more attainable.