F5 Labs and the Security Operations Center (SOC) for WebSafe analyzed Panda banking Trojan configurations active in February and March 2019. They discovered Panda has expanded its scope beyond cryptocurrencies to include online advertisers and digital analytics.
- Although only U.S.-based companies were targeted by this configuration of Panda, a large majority of those companies also serve international customers.
- In the March 2019 configuration Panda specifically targeted three scripts and one link, which activates a zero-byte download. None of these links or scripts have been reported as malware.
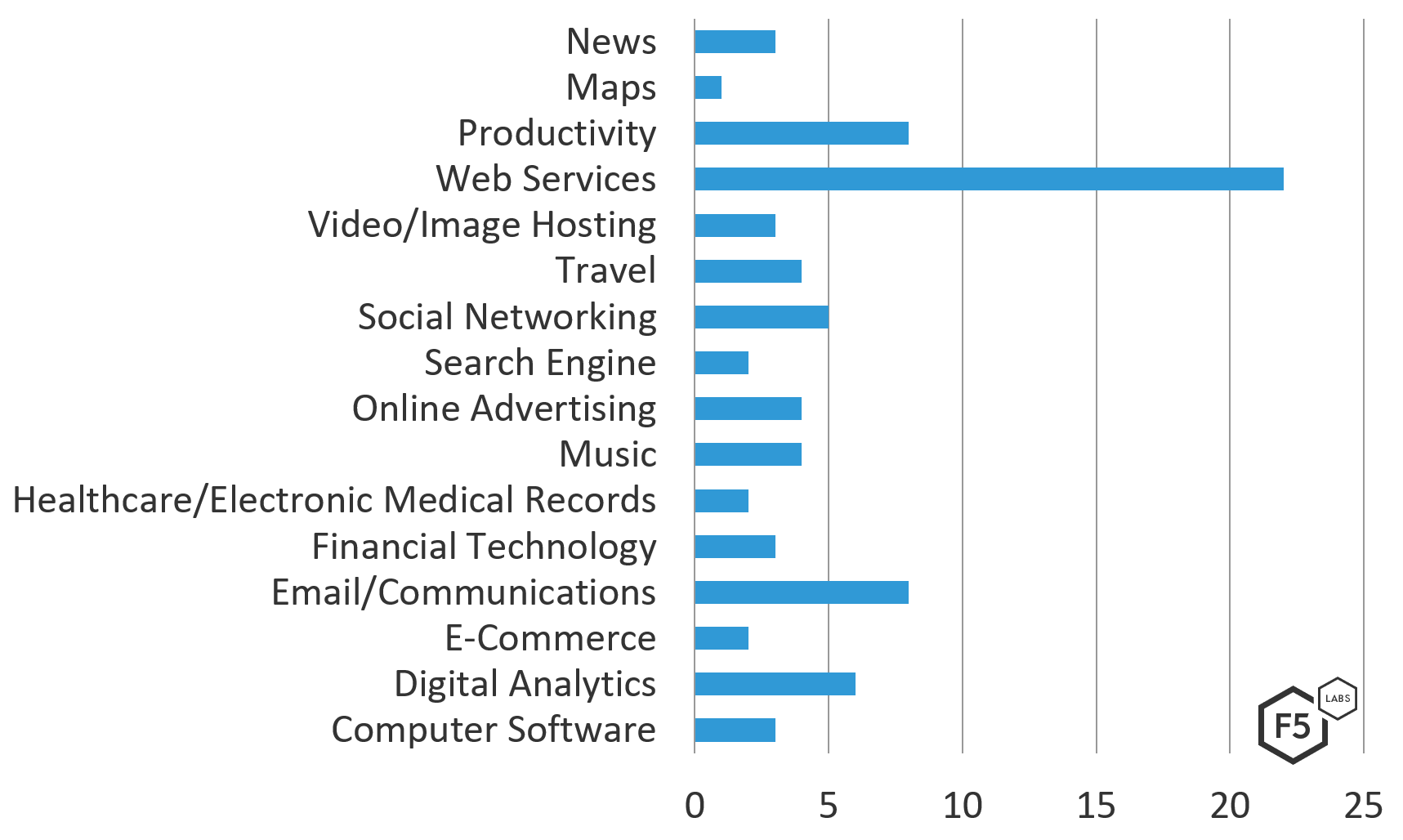
- This configuration of Panda did not focus on the financial services industry. Instead, the web services industry dominated this configuration’s target list.
- Two of the Panda targets were specific JavaScript Ajax links. This may be significant because Ajax has some security issues, including the possibility of exposing the internal functions of a web application.
March Panda Targets
In March 2019, the Panda banking Trojan expanded its scope across many different industries to include productivity, digital analytics companies, online advertising, social media, and healthcare/electronic medical records. It is notable that apart from web services, there is no single industry that Panda specifically targets. The target list did not include any cryptocurrencies as it has in the past, but instead focused on web services and communication mechanisms.
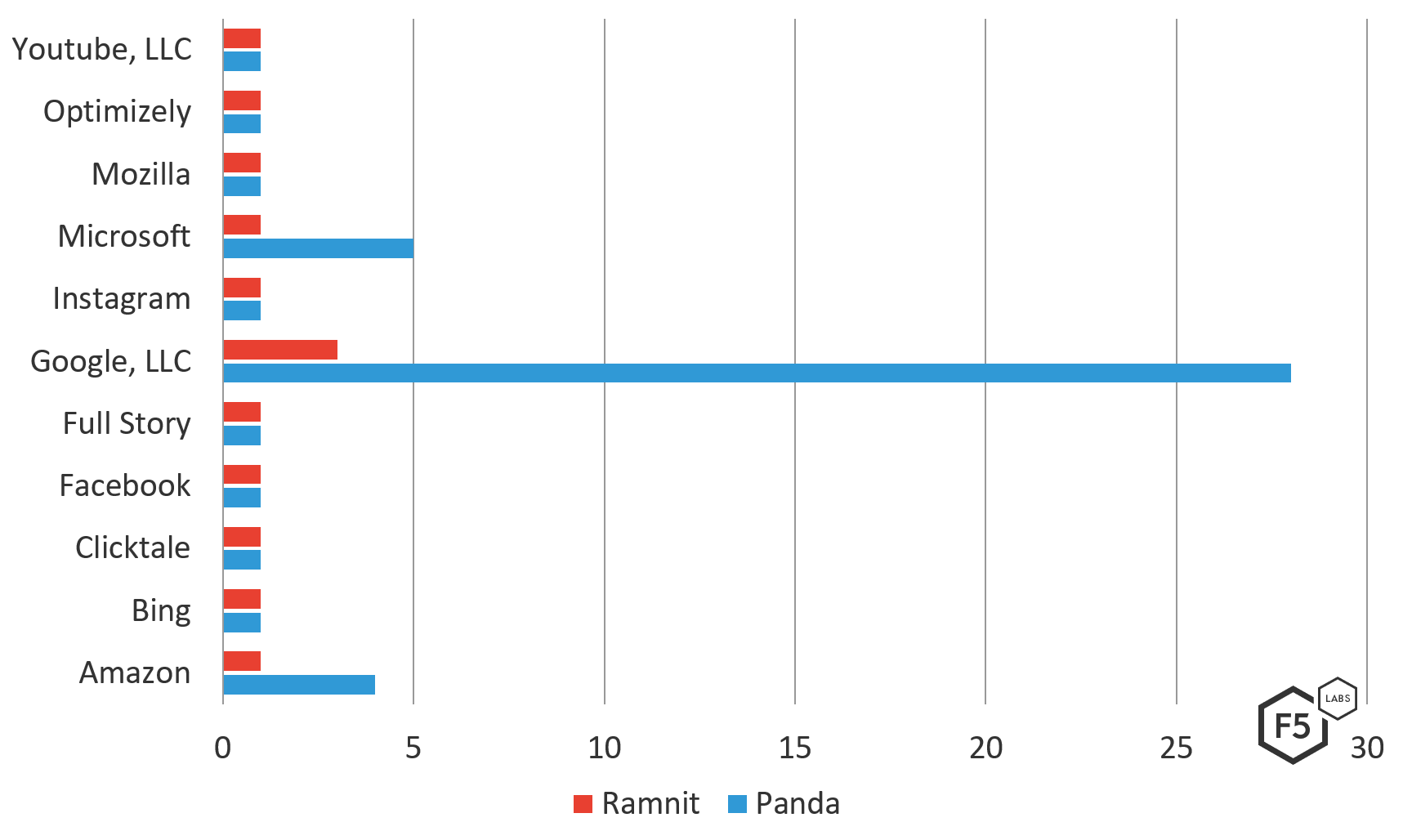
Panda’s expansion beyond traditional banking targets continues a trend F5 Labs first noticed in 2018. Although we noted that this Panda configuration shared a number of target companies/organizations with the Ramnit campaigns during the same time period, Ramnit’s configuration was much more varied with more than 100 targets in its configuration. In contrast, Panda zeroed in on approximately 80 targets. Panda mainly focused on Google, targeting a variety of the web giant’s platforms across industries to include the Google Play Store, Google APIs, and Google Analytics.
Panda is a notable spinoff of the Zeus Trojan horse malware, as it employs stealth capabilities which make detecting and analyzing the malware difficult. When the F5 team analyzed the malware from the March 2019 campaign, they found a custom layer of protection which Panda uses to evade antivirus software. First Panda tries to determine if the function GetWindowsDirectoryA is currently being debugged. After the unpacking procedures, Panda allocates and decrypts itself to a specific address that depends on the GetProcessHeap function.
Panda’s target list includes two productivity web applications that use Ajax. This is notable because unlike web applications that execute completely on a server, Ajax applications utilize functions across both the client and the server. This extends the possible attack surface, and allows for more opportunities to potentially inject malicious code, steal sessions/authentication tokens, or start a browser-based attack. Although security around Ajax has been tightened since the mid-2000s, the possibility for an attack vector remains.
In order to propagate more quickly the latest Panda attacks are utilizing BlackHat SEO injection techniques. Link spam (posting out of context links on forums) is used to increase the number of external links to a specific website. Increasing this number can improve a website’s position in search engines result, resulting in a higher number of clicks. Link spam is highly discouraged, however, Google applies penalties on websites which utilize low-quality link building. Sites that partake in this are subject to punitive action and often see their ranking go down overnight. Panda’s authors are getting more thoughtful with their techniques to spread the malware and are attempting to bypass Google’s punishments.
Conclusion
Panda is an example of a classic banking Trojan that has evolved in technique, sophistication, and industry scope. Panda has expanded well beyond its original purpose of sealing sensitive information and manipulating online transactions. Today’s most sophisticated malware authors are demonstrating their knowledge and experience by using techniques that circumvent a target’s defense mechanisms to evade detection. We’re seeing this trend in almost every piece of code that descends from banking malware.
All industries impacted by Panda malware (such as ecommerce, social media, video/media hosting providers, online advertisers, and others) need to be aware of the increasingly clever techniques being used so they can take precautions. It’s critical for all organizations to provide security awareness training to employees and clients to help them avoid falling victim to phishing attacks or drive by downloads as this is how Trojan attack malware is typically installed.
Panda is just one of many types of malware we follow at F5. Check back with us for updates to this article as future campaigns materialize, and targeted industries expand.
The target list for this version of Panda includes:
| Target Name | Target Domain | Country | Industry |
| http://* | |||
| Bing | https://www.bing.com/fd/ls/lsp.aspx | USA | Search Engine |
| WebPT | https://app.webpt.com/ping.php* | USA | Healthcare/Electronic Medical Records |
| New Relic Browser | https://*bam.nr-data.net* | USA | Web Services |
| Google, LLC | https://googleads.g.doubleclick.net/pagead/ads | USA | Online Advertising |
| Cure MD | https://cloud8.curemd.com* | USA | Healthcare/Electronic Medical Records |
| Microsoft | https://word-view.officeapps.live.com* | USA | Productivity |
| TrackJS | https://capture.trackjs.com* | USA | Web Services |
| AirBnB | https://www.airbnb.com* | USA | Travel |
| SoundCloud | https://*soundcloud.com* | USA | Music |
| Tyler Technologies | https://*tylertech.com* | USA | Computer Software |
| Microsoft | https://outlook.live.com/owa/service.svc* | USA | Email/Communications |
| Expedia | https://oms.expedia.com* | USA | Travel |
| Yahoo | https://mg.mail.yahoo.com* | USA | Email/Communications |
| Google, LLC | https://mail.google.com/mail/* | USA | Email/Communications |
| Clicktale | https://*clicktale.net* | USA | Digital Analytics |
| Yahoo | https://geo.query.yahoo.com* | USA | Maps |
| Yahoo | https://finance.yahoo.com* | USA | News |
| Go daddy | https://email12.godaddy.com* | USA | Email/Communications |
| tSheets | https://ilweb15.tsheets.com/ajax | USA | Productivity |
| Amazon | https://music-xray-service.amazon.com/ | USA | Music |
| SpotX | https://*spotxchange.com* | USA | Online Advertising |
| Dropbox | https://*dropbox.com* | USA | Web Services |
| Amazon | https://fls-na.amazon.com/1/bit-reporter/1/OE | USA | Web Services |
| Microsoft | https://t.urs.microsoft.com/urstelemetry.asmx* | USA | Web Services |
| Google, LLC | https://photos.google.com* | USA | Video/Image Hosting |
| Google, LLC | https://mail.google.com/cloudsearch* | USA | Email/Communications |
| Google, LLC | https://hangouts.google.com/webchat/* | USA | Email/Communications |
| https://*facebook* | USA | Social networking | |
| Youtube , LLC | https://*youtube* | USA | Video/Image Hosting |
| https://*twitter* | USA | Social networking | |
| https://*instagram* | USA | Social networking | |
| Flickr | https://*flickr.com* | USA | Video/Image Hosting |
| https://*linkedin.com* | USA | Social networking | |
| Conviva | https://*conviva.com* | USA | Digital Analytics |
| Google, LLC | https://www.google-analytics.com* | USA | Digital Analytics |
| Google, LLC | https://safebrowsing.google.com/* | USA | Web Services |
| Google, LLC | https://translate.google.com/* | USA | Email/Communications |
| Google, LLC | https://*clients1.google.com* | USA | Web Services |
| Google, LLC | https://*clients2.google.com* | USA | Web Services |
| Google, LLC | https://*clients4.google.com* | USA | Web Services |
| Google, LLC | https://*clients5.google.com* | USA | Web Services |
| Google, LLC | https://*clients6.google.com* | USA | Web Services |
| Google, LLC | https://ogs.google.com/u/0/_/notifications/count | USA | Web Services |
| Google, LLC | https://*googleapis.com* | USA | Web Services |
| Google, LLC | https://*talkgadget.google.com* | USA | Email/Communications |
| Google, LLC | https://0.client-channel.google.com* | USA | Web Services |
| Google, LLC | https://plus.google.com/u/* | USA | Social networking |
| Google, LLC | https://play.google.com/* | USA | Computer Software |
| Google, LLC | https://drive.google.com/* | USA | Productivity |
| Google, LLC | https://docs.google.com/* | USA | Productivity |
| Google, LLC | https://notifications.google.com/u* | USA | Productivity |
| Google, LLC | https://*client-channel.google.com* | USA | Web Services |
| Google, LLC | https://apis.google.com* | USA | Web Services |
| Google, LLC | https://calendar.google.com* | USA | Productivity |
| Etsy | https://*etsy.com* | USA | E-Commerce |
| Issu | https://*issuu.com* | USA | News |
| Amazon | https://music.amazon.com* | USA | Music |
| Yahoo | https://comet.yahoo.com/comet | USA | Online Advertising |
| Yahoo | https://pr.comet.yahoo.com/comet | USA | Online Advertising |
| Apple | https://p54-bookmarks.icloud.com* | USA | Web Storage |
| Grendel CRM | https://www.grendelonline.com* | USA | Financial Technology |
| Yelp | https://www.yelp.com* | USA | Travel |
| LiveVol | https://secure.livevol.com* | USA | Financial Technology |
| Google, LLC | https://www.google-analytics.com/collect | USA | Digital Analytics |
| Amazon | https://fls-na.amazon.com/1/batch/1/OE/ | USA | Web Services |
| Toys"R"Us | https://edq.toysrus.com/* | USA | E-Commerce |
| tSheets | https://azweb16.tsheets.com/ajax* | USA | Productivity |
| Google, LLC | https://beacons.gvt2.com/domainreliability/upload* | USA | Web Services |
| Pandora Radio | https://www.pandora.com* | USA | Music |
| Google, LLC | https://www.google.com* | USA | Search Engine |
| Microsoft | https://urs.microsoft.com/urs.asmx* | USA | Web Services |
| Yahoo | https://udc.yahoo.com/v2/public* | USA | Web Services |
| Full Story | https://r.fullstory.com/rec/* | USA | Digital Analytics |
| Mozilla | https://incoming.telemetry.mozilla.org* | USA | Web services |
| Microsoft | https://msub03.manage.microsoft.com/ AdminAPIWebService/adminapi.svc/silverlightXml | USA | Web Services |
| Full Slate | https://app.fullslate.com/admin/journal/commit?poll | USA | Productivity |
| Optimizely | https://logx.optimizely.com/log/event | USA | Digital Analytics |
| Expedia | https://www.expedia.com/api/datacapture/track | USA | Travel |
| https://s.acexedge.com* | |||
| Scanmarket | https://*scanmarket.com* | USA | Computer Software |
| Intuit Inc. | https://*intuit.com* | USA | Financial Technology |
| https://*crdui.com* | |||
| Yahoo | https://www.yahoo.com* | USA | News |
- Change email addresses of targeted employees
- Administrative/Corrective: Review access controls
- Notify your clients of the malware you detected on their system while logging into your application (why they are blocked from transacting), so they can take steps to clean their systems