F5 Labs and the F5 Security Operations Center (SOC) for WebSafe analyzed Ramnit banking Trojan Malware configurations active in February and March 2019. They discovered that Ramnit authors were—once again—largely targeting financial services websites, specifically in Italy.
- Financial services and financial technology industries make up the largest part of Ramnit targets. However, like many other “banking” Trojans, Ramnit has expanded its targets over the years to include industries beyond banking, including online advertising, web services, and ecommerce sites.
- Although social networking sites made up a smaller portion of targets seen in February and March, the target list included some of the biggest social networking and sharing platforms in the world, including Twitter, Facebook, Tumblr, and YouTube.
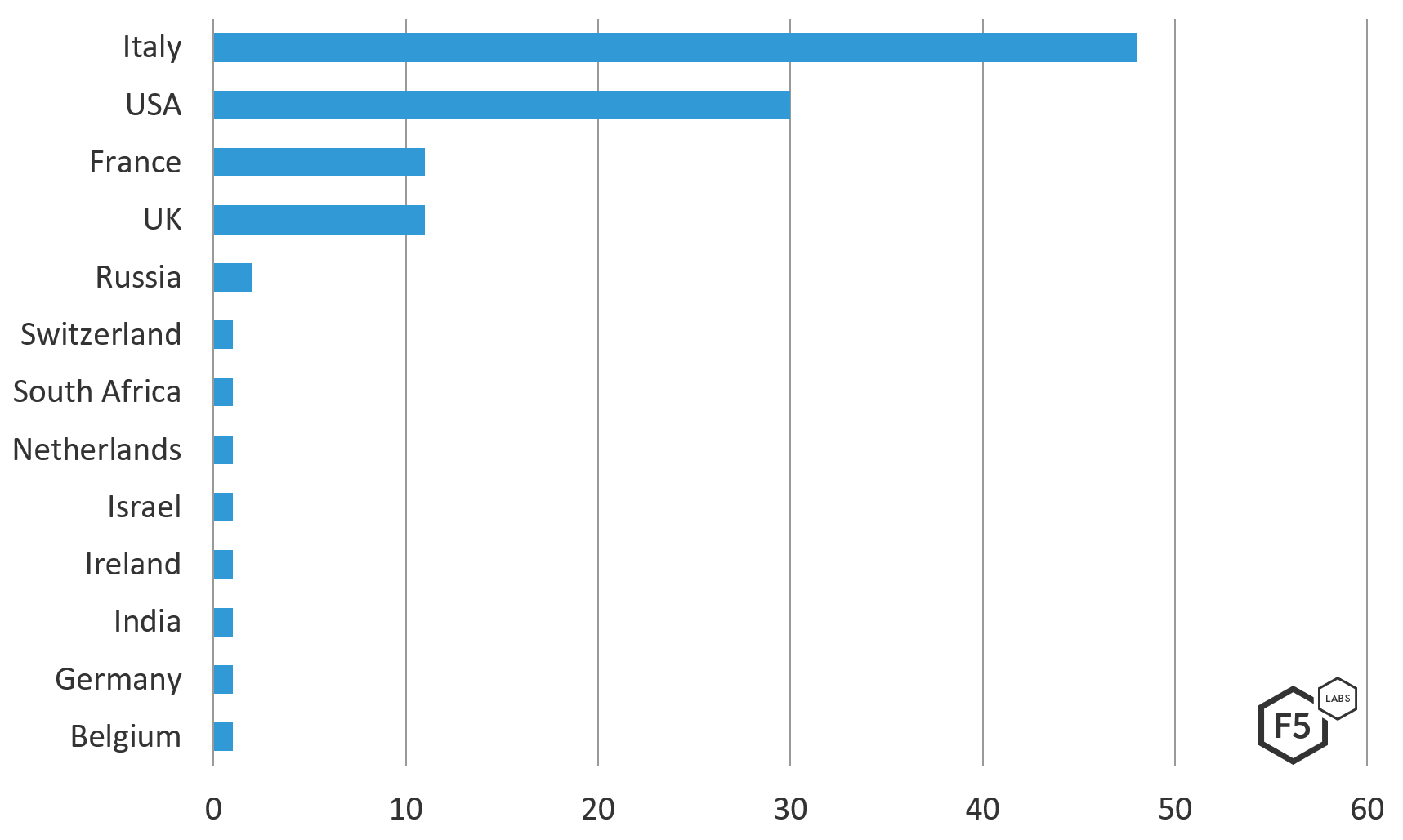
- Italian banks made up a large portion of targets of this configuration. France and the UK (specifically banks based out of Scotland) were also popular targets.
In a recent Ramnit sample that was active in March 2019, Ramnit authors primarily targeted banks in Italy and the UK. See Figure 1 for a more detailed breakdown of which countries were highly targeted.
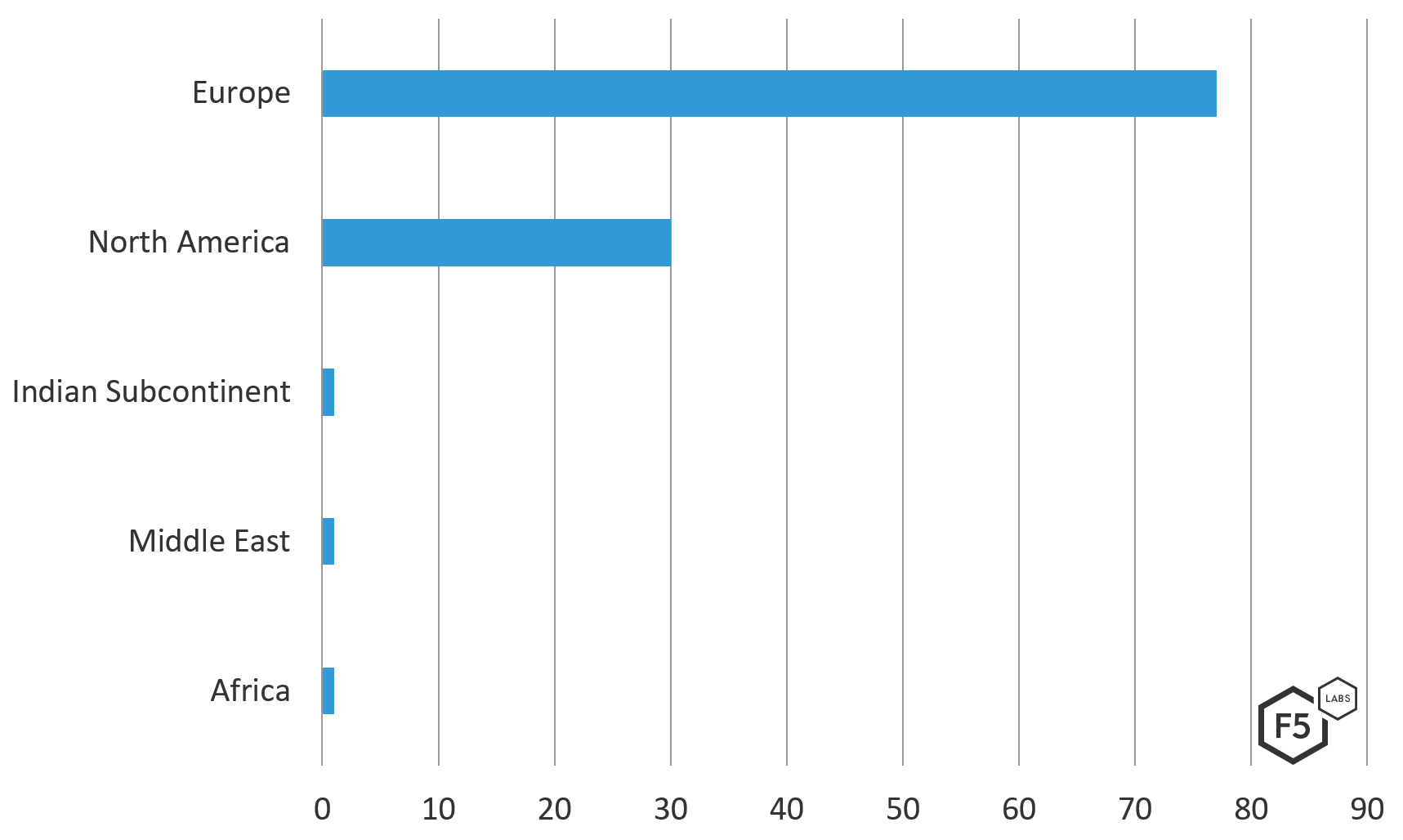
At a global level, 70% of all targets in this Ramnit configuration were European. North American (USA) targets followed with 27% of the list, and the rest of the world made up the final 3%. See the frequency chart in Figure 2 for a more detailed breakout.
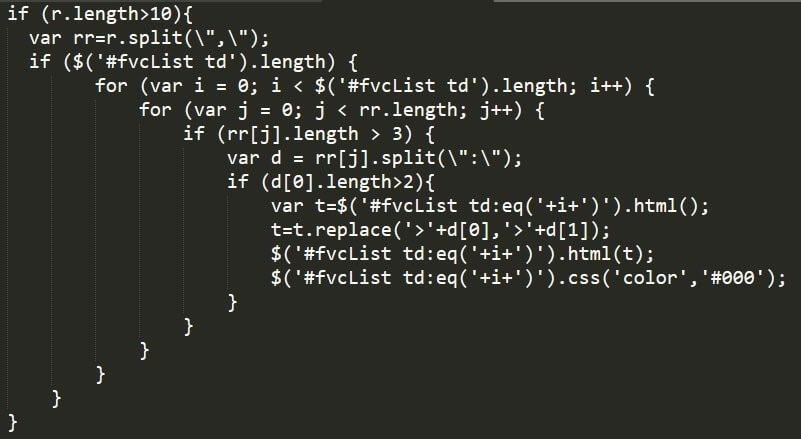
In Figure 3 we can see Ramnit’s web injection manipulating the HTML. This type of web injection enables a malicious actor to capture credentials or sensitive account information, further allowing for funds to be stolen.
In the Ramnit configuration, there were a number of targets that didn’t belong to a particular company or website: Instead, there were several words in French, Italian, and English. This is an innovation we have not seen in previous Ramnit configurations. It appears as though the Ramnit authors cast a wider net in hopes of catching random websites. Along with the simple word targets, Ramnit also included the name of an Italian Opera and a few misspelled domain names. Non-domain targets from this configuration include:
| !*-sys.com* | !*ocsp.* | *control* |
| !*ads.* | !*office* | *corp* |
| !*analytic* | !*outlook* | *Customer* |
| !*api.* | !*stream* | *Dashboard* |
| !*bam.nr-data.net* | !*track* | *identity* |
| !*chat* | !*trouter.io* | *importo* |
| !*cloud* | !*update* | *login* |
| !*download* | !*upload* | *Main* |
| !*events* | !*video* | *manager* |
| !*game* | !http://* | *panel* |
| !*gigaup13b.allegati.tim.it* | *access* | *payment* |
| !*gstatic.* | *account* | *register* |
| !*hub* | *admin* | *secure* |
| !*iltrovatore.it* | *Authenticate* | *sepa* |
| !*iolam.it* | *authentipec* | *sign* |
| !*lampoilbro* | *bank* | *trade* |
| !*messenger* | *basic* | *virement* |
| !*metric* | *bonifico* |
Companies and websites targeted from this configuration include:
| Target Name | Target Domain | Country | Industry |
| http://* | |||
| Bing | https://www.bing.com/fd/ls/lsp.aspx | USA | Search Engine |
| WebPT | https://app.webpt.com/ping.php* | USA | Healthcare/Electronic Medical Records |
| New Relic Browser | https://*bam.nr-data.net* | USA | Web Services |
| Google, LLC | https://googleads.g.doubleclick.net/pagead/ads | USA | Online Advertising |
| Cure MD | https://cloud8.curemd.com* | USA | Healthcare/Electronic Medical Records |
| Microsoft | https://word-view.officeapps.live.com* | USA | Productvity |
| TrackJS | https://capture.trackjs.com* | USA | Web Services |
| AirBnB | https://www.airbnb.com* | USA | Travel |
| SoundCloud | https://*soundcloud.com* | USA | Music |
| Tyler Technologies | https://*tylertech.com* | USA | Computer Software |
| Microsoft | https://outlook.live.com/owa/service.svc* | USA | Email/Communications |
| Expedia | https://oms.expedia.com* | USA | Travel |
| Yahoo | https://mg.mail.yahoo.com* | USA | Email/Communications |
| Google, LLC | https://mail.google.com/mail/* | USA | Email/Communications |
| Clicktale | https://*clicktale.net* | USA | Digital Analytics |
| Yahoo | https://geo.query.yahoo.com* | USA | Maps |
| Yahoo | https://finance.yahoo.com* | USA | News |
| Go daddy | https://email12.godaddy.com* | USA | Email/Communications |
| tSheets | https://ilweb15.tsheets.com/ajax | USA | Productvity |
| Amazon | https://music-xray-service.amazon.com/ | USA | Music |
| SpotX | https://*spotxchange.com* | USA | Online Advertising |
| Dropbox | https://*dropbox.com* | USA | Web Services |
| Amazon | https://fls-na.amazon.com/1/bit-reporter/1/OE | USA | Web Services |
| Microsoft | https://t.urs.microsoft.com/urstelemetry.asmx* | USA | Web Services |
| Google, LLC | https://photos.google.com* | USA | Video/Image Hosting |
| Google, LLC | https://mail.google.com/cloudsearch* | USA | Email/Communications |
| Google, LLC | https://hangouts.google.com/webchat/* | USA | Email/Communications |
| https://*facebook* | USA | Social networking | |
| Youtube , LLC | https://*youtube* | USA | Video/Image Hosting |
| https://*twitter* | USA | Social networking | |
| https://*instagram* | USA | Social networking | |
| Flickr | https://*flickr.com* | USA | Video/Image Hosting |
| https://*linkedin.com* | USA | Social networking | |
| Conviva | https://*conviva.com* | USA | Digital Analytics |
| Google, LLC | https://www.google-analytics.com* | USA | Digital Analytics |
| Google, LLC | https://safebrowsing.google.com/* | USA | Web Services |
| Google, LLC | https://translate.google.com/* | USA | Email/Communications |
| Google, LLC | https://*clients1.google.com* | USA | Web Services |
| Google, LLC | https://*clients2.google.com* | USA | Web Services |
| Google, LLC | https://*clients4.google.com* | USA | Web Services |
| Google, LLC | https://*clients5.google.com* | USA | Web Services |
| Google, LLC | https://*clients6.google.com* | USA | Web Services |
| Google, LLC | https://ogs.google.com/u/0/_/notifications/count | USA | Web Services |
| Google, LLC | https://*googleapis.com* | USA | Web Services |
| Google, LLC | https://*talkgadget.google.com* | USA | Email/Communications |
| Google, LLC | https://0.client-channel.google.com* | USA | Web Services |
| Google, LLC | https://plus.google.com/u/* | USA | Social networking |
| Google, LLC | https://play.google.com/* | USA | Computer Software |
| Google, LLC | https://drive.google.com/* | USA | Productvity |
| Google, LLC | https://docs.google.com/* | USA | Productvity |
| Google, LLC | https://notifications.google.com/u* | USA | Productvity |
| Google, LLC | https://*client-channel.google.com* | USA | Web Services |
| Google, LLC | https://apis.google.com* | USA | Web Services |
| Google, LLC | https://calendar.google.com* | USA | Productvity |
| Etsy | https://*etsy.com* | USA | E-Commerce |
| Issu | https://*issuu.com* | USA | News |
| Amazon | https://music.amazon.com* | USA | Music |
| Yahoo | https://comet.yahoo.com/comet | USA | Online Advertising |
| Yahoo | https://pr.comet.yahoo.com/comet | USA | Online Advertising |
| Apple | https://p54-bookmarks.icloud.com* | USA | Web Storage |
| Grendel CRM | https://www.grendelonline.com* | USA | Financial Technology |
| Yelp | https://www.yelp.com* | USA | Travel |
| LiveVol | https://secure.livevol.com* | USA | Financial Technology |
| Google, LLC | https://www.google-analytics.com/collect | USA | Digital Analytics |
| Amazon | https://fls-na.amazon.com/1/batch/1/OE/ | USA | Web Services |
| Toys"R"Us | https://edq.toysrus.com/* | USA | E-Commerce |
| tSheets | https://azweb16.tsheets.com/ajax* | USA | Productvity |
| Google, LLC | https://beacons.gvt2.com/domainreliability/upload* | USA | Web Services |
| Pandora Radio | https://www.pandora.com* | USA | Music |
| Google, LLC | https://www.google.com* | USA | Search Engine |
| Microsoft | https://urs.microsoft.com/urs.asmx* | USA | Web Services |
| Yahoo | https://udc.yahoo.com/v2/public* | USA | Web Services |
| Full Story | https://r.fullstory.com/rec/* | USA | Digital Analytics |
| Mozilla | https://incoming.telemetry.mozilla.org* | USA | Web services |
| Microsoft | https://msub03.manage.microsoft.com/ AdminAPIWebService/adminapi.svc/silverlightXml | USA | Web Services |
| Full Slate | https://app.fullslate.com/admin/journal/commit?poll | USA | Productvity |
| Optimizely | https://logx.optimizely.com/log/event | USA | Digital Analytics |
| Expedia | https://www.expedia.com/api/datacapture/track | USA | Travel |
| https://s.acexedge.com* | |||
| Scanmarket | https://*scanmarket.com* | USA | Computer Software |
| Intuit Inc. | https://*intuit.com* | USA | Financial Technology |
| https://*crdui.com* | |||
| Yahoo | https://www.yahoo.com* | USA | News |
Conclusion
Trojan malware designed to attack the online customers of banks and financial institutions has been around for over a decade, but it continues to evolve in technique and sophistication. Ramnit is a persistent banking Trojan that first emerged in 2010 as a less sophisticated form of a self-replicating worm. Today, both its tactics and targets have evolved to include many other industries. It’s no longer enough for banking Trojans to just steal sensitive information or manipulate an online transaction—Ramnit in particular was designed to manipulate online banking sessions in order to steal credentials and funds from customers via wire transfer. Over the 2017 holiday season, however, F5 Labs reported that Ramnit’s targets turned from banks to retail, in anticipation of the busy shopping season. Today’s most sophisticated malware authors evade detection and demonstrate their knowledge of the targets by using new techniques to circumvent a target’s defense mechanisms. We’re seeing this trend in almost every piece of code that descends from banking malware.
It’s critically important for banks and financial institutions to implement web fraud protection solutions to protect their customers and to help ease the burden of fraud expenses—especially banks that are actively being targeted. Because we’re seeing traditional banking Trojans expand their targets, other industries outside of banking (such as online advertising, ecommerce, social media, crypto currency exchanges, and others) need to be aware of attackers’ increasingly clever techniques so they can take equal precautions. Because Trojan malware is typically installed through phishing or malicious advertising, it’s also becoming more critical for all organizations to provide security awareness training to employees and clients to help them avoid falling victim.
Ramnit is just one of many types of malware we follow at F5 Labs. Check back for updates to this article as future campaigns materialize and targeted industries expand.
IOCs
Malware hashes seen in this configuration:
| SHA 1 hash: | 1acc71bd6f830061ed8f1d9446f439e019063656 |
| SHA 256 Hash: | 746bd60108cb3af40b98346f467c9fd9a3db216 f80e8677ad50aaf814999e68c |
| MD5 Hash: | ace9bd5b0a7e0d50e31eeec00970bf6f |
| Config first seen: | 3/21/19 13:26 |
| Config last seen: | 3/21/19 13:26 |
- Change email addresses of targeted employees
- Administrative/Corrective: Review access controls
- Notify your clients of the malware you detected on their system while logging into your application (why they are blocked from transacting), so they can take steps to clean their systems