This is the first in a series of articles aimed at helping organisations understand how to protect their business and their brand from phishing and fraud attacks. Many protocols and tools—some new, some old—exist that can help combat this omnipresent threat, yet many are not widely deployed. For those who aren’t familiar with these tools, this article provides an introduction to help organisations begin to build a robust phishing and fraud mitigation strategy.
The F5 Labs 2018 Phishing and Fraud Report shows that phishing attacks jump 50% over the average in October to December. And while phishing is a year-round activity for attackers, the number and types of targets vary from country to country and month to month. For example, the year-end holiday season sees a jump in phishing emails that target customers of retailers and shipping services while income tax season sees the focus shift to government websites. Her Majesty's Revenue and Customs (HMRC), the UK government agency responsible for collecting income tax, is the most phished brand in the country. Fake emails purporting to be from HMRC ramp up in January, right before the self-assessment deadline.
According to the Censys.io database, the name “paypal” appears somewhere in the common name field of over 26,000 digital certificates. Digital (SSL/TLS) certificates are essentially designed to assure site visitors that the site they’re connecting to is legitimately who they claim to be. Of course, not all of these 26,000 certificates are malicious, but it's obvious to most of us that www-paypal-com.k1zj5qwnrdp.tk is not one of the genuine ones! The certificate for this domain was created to ensure the victim saw a friendly looking padlock in their browser, but that’s no guarantee the site is legitimate or safe. According to the F5 Labs report, Apple is one of the top ten phished (impersonated) sites by attackers. Not surprisingly, the Centsys.io database lists 107,505 certificates that contain the word “apple,” 45% of which were created by users of the free and automated Let's Encrypt. Further, 28,071 certificates contain the name “appleid”, an astounding 85% of which also come from Let's Encrypt.
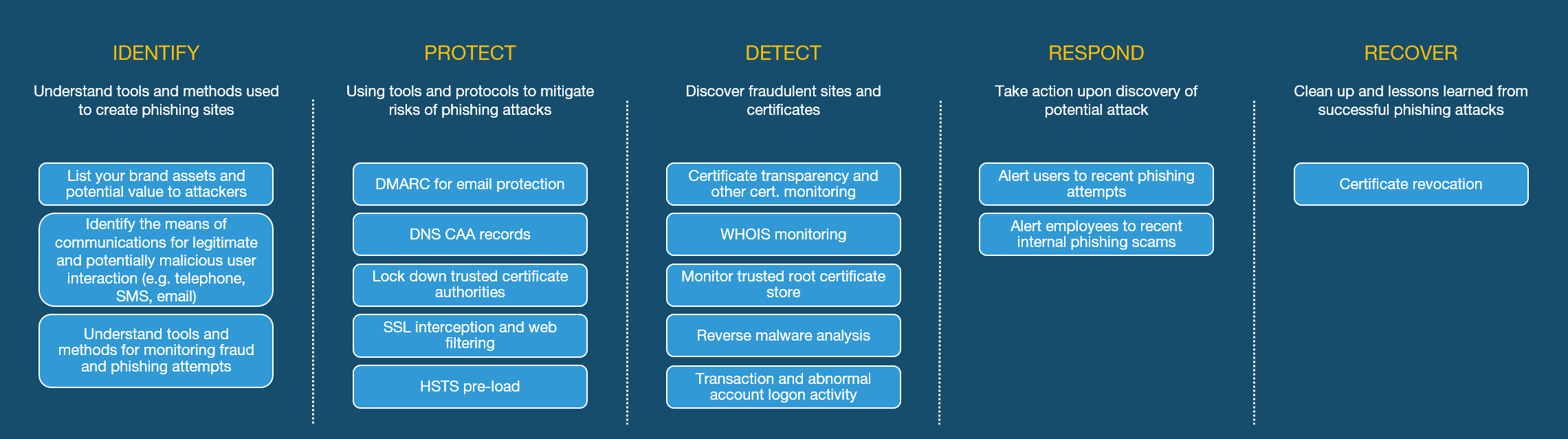
While the F5 Labs Phishing and Fraud Report lists a wide range of recommendations for both consumers and organisations, this series of articles delves deeper into some simple protocols that can help with the detection, protection, and prevention of phishing attacks. As with any aspect of information security, no single tool or method is perfect. But used in combination, some of the following tools, protocols, and actions (see also Figure 1) can significantly raise the level of complexity attackers face when attacking your brand:1
- Monitoring the creation of certificates and domain names
- Performing malware reverse analysis
- Using email and web filtering
- Controlling which certificate authorities may create certificates on your behalf
The most common initial vector for phishing attacks is the fraudulent email. A well-crafted phishing email entices the victim to click on a malicious link that then takes them to an attacker’s site. Once that happens, that site must appear to be as authentic as possible. Images, fonts, layout, styles, and even the URL will be identical or as closely matched as possible to the genuine site.
When a victim falls for the trap and clicks on the malicious link, the format of the website address to which they’re taken generally follows one of these forms:
- A simple IP address. This will look immediately suspicious to the more IT-literate web user; to many average consumers, it is simply another complicated looking website address to which they pay little attention. The attacker may use a valid looking brand name or domain name in the uniform resource identifier (URI) after the domain.
https://1.2.3.4/yourbank.com
A common misconception is that SSL certificates must contain only domain names and not IPv4 or IPv6 addresses. This is not true, however, but while SSL certificates for public IP addresses are indeed allowed, Let’s Encrypt does not currently permit this through their API. Therefore, for short-lived phishing sites, it is likely that attackers will not rely on IP addresses only and will be forced to register a domain name for which they can request a digital certificate.
- An obfuscated domain. This method is increasingly common, particularly in light of free and automated certificates from the likes of LetsEncrypt.org. Similar to Method 1, attackers hope to draw the victim’s eye to a valid looking part of the address.
https://yourbank.com-attacker.com
https://attacker-yourbank.com
Domains and certificates for these addresses are rarely blocked by registrars, even when global top-level domains (gTLDs) such as .com and .net appear in the middle of the address.
- Internationalized domain name. By making use of non-ASCII character sets and the fact that some alphabets have similar looking characters, an attacker can register a domain that looks like a publicly recognized brand but is actually totally unique.
https://yourḅank.com (note the non-ASCII “b” character)
- A subdomain of a legitimate site. If an attacker is able to access your registrar, they will be able to create a subdomain. Since this subdomain is under their control, they can easily create fraudulent SSL certificates.
https://attacker.yourbank.com
While dictionary words are often used to create obfuscated domains, we see increasing use of domain generation algorithms (DGAs). DGAs are used to create unique domains and subdomain with the benefit that a new [sub]domain will likely not exist in any denylist.
https://ei19vgsn1dh.yourbank.com-attacker.com
In addition to compromising your registrar, attackers will monitor the use of subdomains. Often a subdomain will be used to point to a third-party site such as GitHub or WordPress. If the relevant GitHub or WordPress subscription lapses, then it may be possible for an attacker to assume control of it.
- Valid domains through CA misuse. If an attacker can breach the security of a certificate authority or simply has a poor process for validating ownership of a domain, then the attacker can create genuine certificates for your site.
https://yourbank.com
It was due to poor security practises and the creation of certificates without proper authorisation that led the Certificate Authority and Browser (CAB) forum to eject WoSign and Symantec as trusted CAs.1
What is consistent among these methods is that, with the increasing use of SSL across the web, attackers are pushed to present a valid certificate in order to appear genuine.
Other methods to direct victims to attacker-controlled sites also exist. In some cases, a vulnerability of the target organisations website, such as an open redirect2 can allow the attacker to create malicious links that actually make use of legitimate domains. In the following example, a vulnerability on a banking website allows redirections to external domains. The advantage to the attacker is that the initial portion of the website is genuine, so it will not raise immediate concerns:
https://yourbank.com/?red=attacker.example.com
International Domain Names (IDN) allow the use of non-Unicode characters in domains. This allows non-English speaking countries the ability to use their native character sets. However, since some non-English characters look identical to English letters, they can be used to create a domain that looks entirely genuine but actually sends the victim to a site that is anything but. Phishing sites making use of IDNs are largely mitigated by browsers that prevent the use of mixed character sets in the address bar.3
Conclusion
While some attackers use arbitrary domain names and hope that the victim does not inspect the address bar (that is, methods 1 and 2), many will register a domain or subdomain that includes the domain name or brand name of the targeted organisation (methods 3, 4 and 5). It is for this attack vector that Certificate Transparency (CT) comes in useful.
In our next blog, we’ll look at CT in more detail, explain how it works, and how you can use it to protect your organisation and your brand's reputation.






