The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Welcome to the February 2023 installment of the Sensor Intelligence Series. This series offers web application vulnerability targeting intelligence. We produce this intelligence by analyzing scanning and exploit attempts logged by sensors run by our data partners, Efflux. As always, our analysis is limited to traffic on ports 80 and 443.
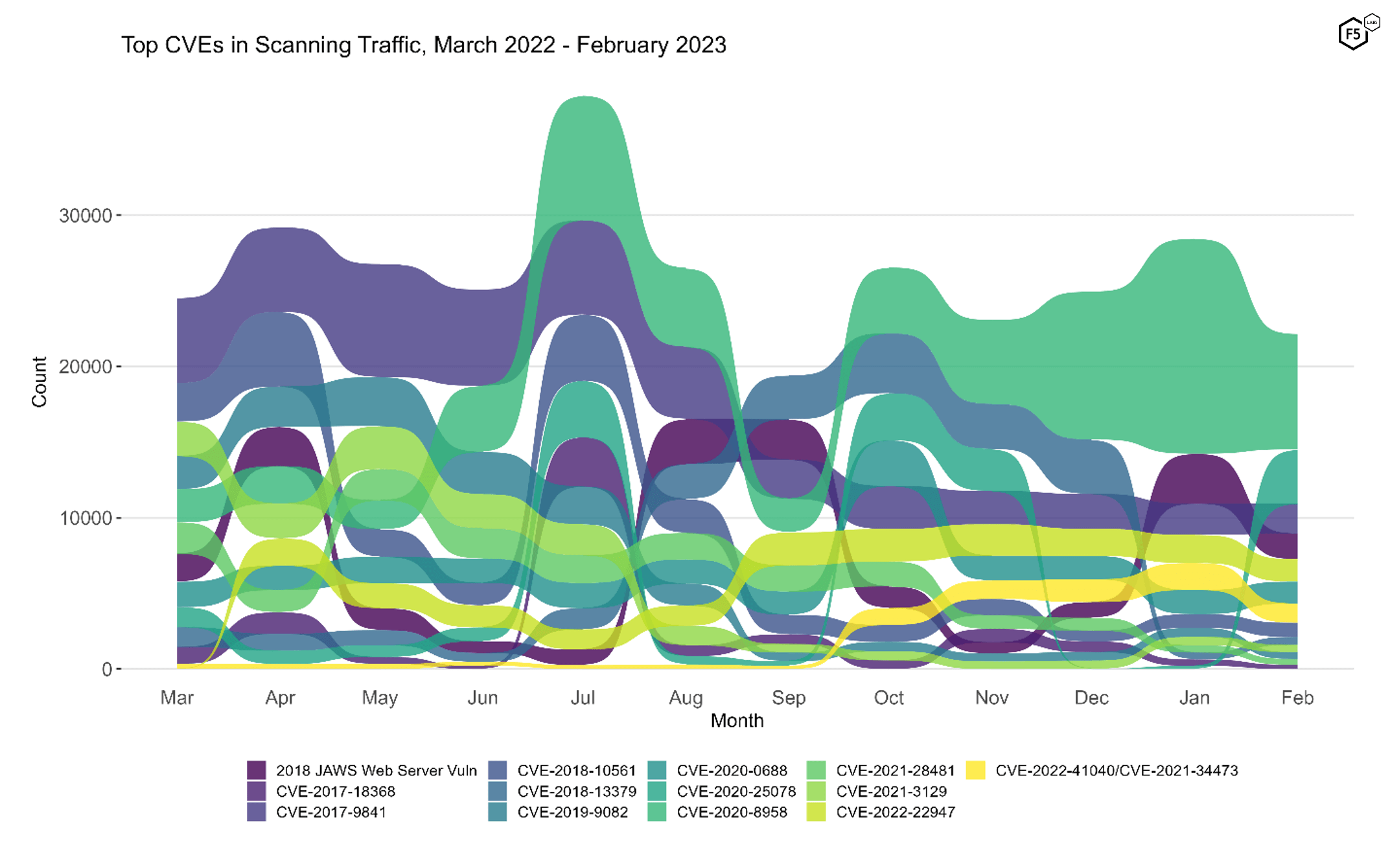
CVE-2020-8958, an IoT vulnerability in several Guangzhou/VSOL routers, has been the top-targeted vulnerability we track for six of the last seven months, and it retains its top spot in February as well. However, its traffic declined 47% compared with January, making its recent volume closer to what we observed in November. Perhaps this spells the beginning of its decline, although as you’ll see below in Figure 2, we’ve seen CVEs in general and this one in particular seem to fall off of a cliff, only to rebound the following month.