What Is MITRE ATT&CK®?
MITRE ATT&CK is a documented collection of information about the malicious behaviors advanced persistent threat (APT) groups have used at various stages in real-world cyberattacks. ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, includes detailed descriptions of these groups’ observed tactics (the technical objectives they’re trying to achieve), techniques (the methods they use), and procedures (specific implementations of techniques), commonly called TTPs.
Although MITRE ATT&CK is not a threat model per se (it doesn’t compare in a traditional sense to models like PASTA,1 STRIDE2 or OCTAVE3), it is often used as the foundation for organizations developing their own customized threat models. Think of it as an encyclopedic reference that describes TTPs adversaries use, provides suggestions for detection and common mitigations for specific techniques, and profiles APT groups’ known practices, characteristics, and specific attack attributions. ATT&CK also provides an extensive list of software used in attacks (both malware and commercially available and open-source code that can be used legitimately or maliciously). All information captured in ATT&CK comes from publicly available data and reports as well as from the community—threat researchers and security teams in the trenches experiencing or analyzing attacks daily.
Who Uses MITRE ATT&CK and Why
ATT&CK is a free tool that private and public sector organizations of all sizes and industries have widely adopted. Users include security defenders, penetration testers, red teams, and cyberthreat intelligence teams as well as any internal teams interested in building secure systems, applications, and services. The wealth of attack (and attacker) information it contains can help organizations determine whether they’re collecting the right data to effectively detect attacks and evaluate how well their current defenses are working.
Unlike other models written from a defender’s perspective, ATT&CK intentionally takes an attacker’s point of view to help organizations understand how adversaries approach, prepare for, and successfully execute attacks. This also makes ATT&CK an excellent resource and teaching tool for individuals interested in entering the field of cybersecurity or threat intelligence and those who simply want to understand more about attacker behavior.
Although the information captured in ATT&CK reflects known APT behaviors, it would be a mistake to assume those behaviors are the exclusive territory of APTs. As Ray Pompon, former CISO and current Director of F5 Labs warns, “What APTs are doing today, script kiddies will be doing tomorrow.” If you think your organization can’t benefit from ATT&CK because it’s not the target of APTs and will never experience APT-like attack behavior, think again. The TTPs outlined in ATT&CK happen every day in organizations of all sizes and significance. It’s not necessary to be the target of an APT to experience the same kinds of attacks or to use the ATT&CK tool to improve your defenses.
An Overview of the ATT&CK Framework
Attackers operate differently depending on their attack target. For example, they use different TTPs to compromise enterprise systems than they would to attack mobile devices or industrial control systems. MITRE provides three separate “matrices” to address these distinct environments. Together, these three matrices make up what MITRE collectively refers to as the ATT&CK framework.
The Enterprise matrix addresses platforms such as Windows, macOS, Linux, and others as well as something called “PRE,” which simply indicates actions taken pre-attack or in preparation for an attack. The Mobile matrix addresses both Android and iOS, and the ICS matrix addresses industrial control systems. Although the three matrices share some common tactics (Initial Access and Persistence, for example), the specific techniques for each tactic can vary by environment.
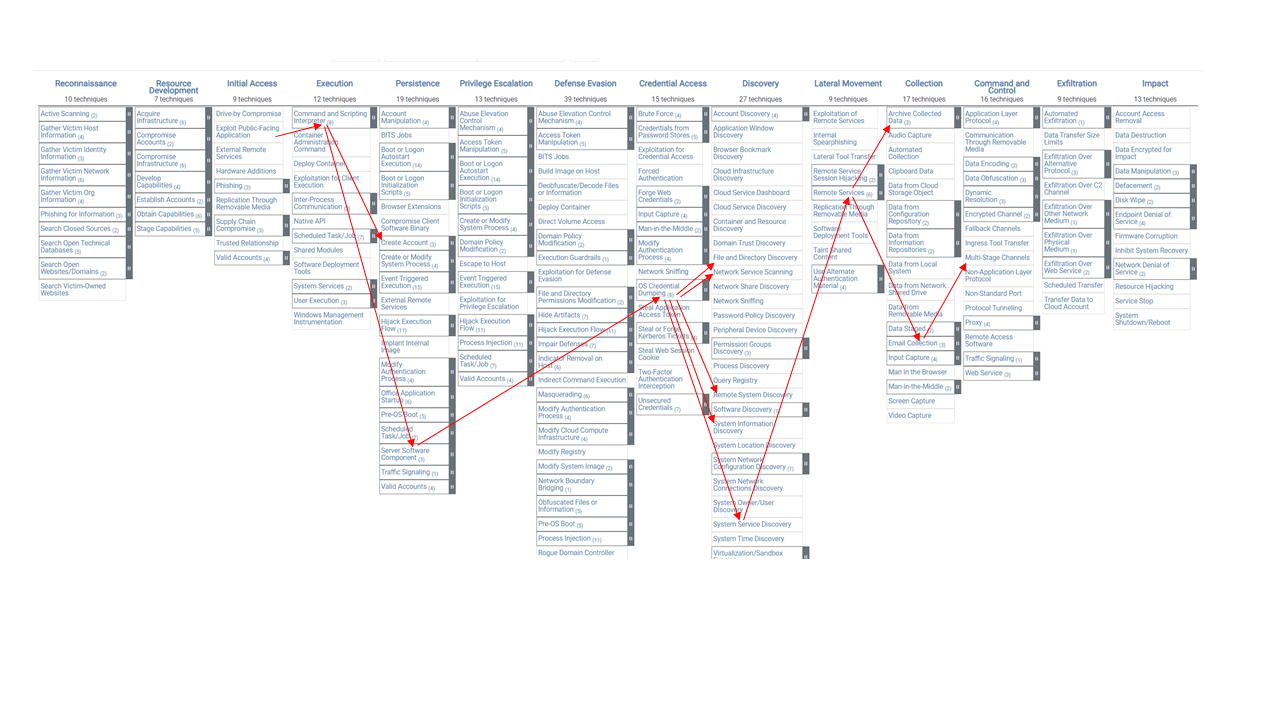
This article focuses primarily on the Enterprise matrix. At first glance, its sheer size and density can leave you wondering where to begin (see Figure 1).
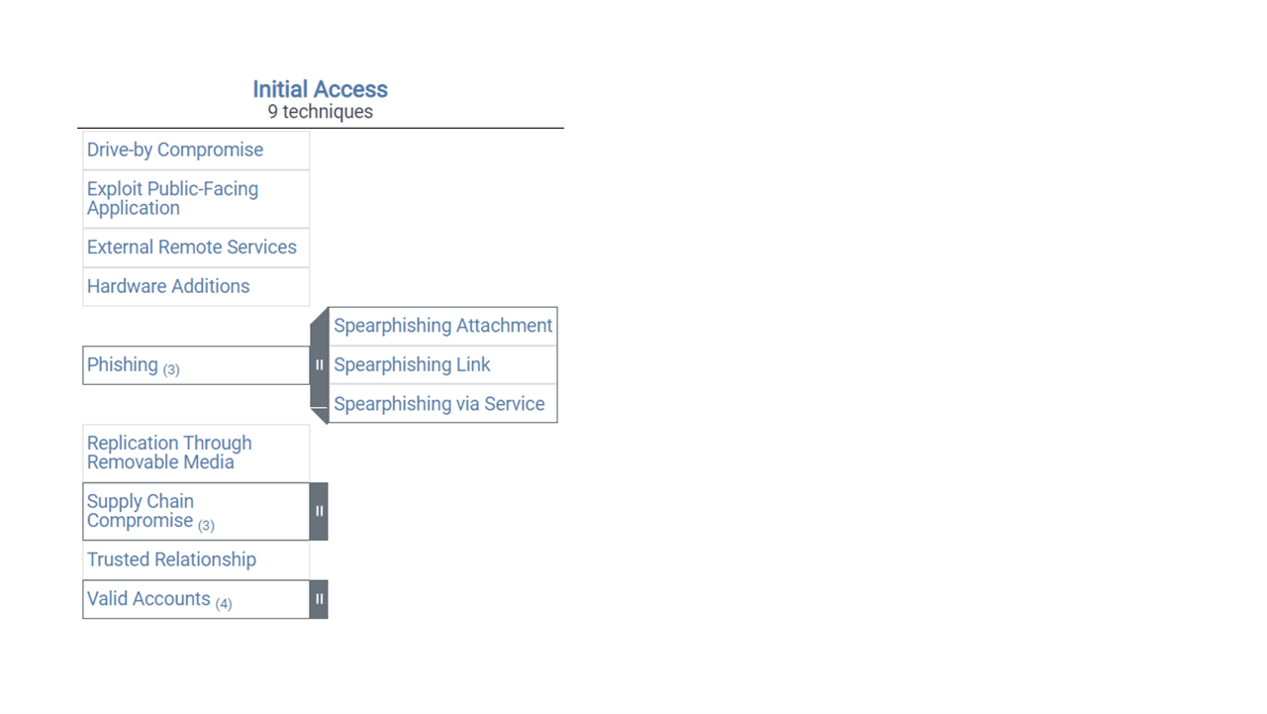
The term matrix can also be somewhat misleading if you’re expecting rows that run the width of all columns like in a spreadsheet. Once you realize the 14 independent columns are structured more like individual organization charts (see Figure 2), the full matrix becomes far less daunting. Associated techniques and sub-techniques appear beneath each tactic.