Executive Summary
In this fifth volume of F5 Labs’ The Hunt for IoT report series, we examine the data on global attacks against Internet of Things (IoT) devices from January through June 2018. In early 2017, Gartner—one of the most conservative analyst firms when it comes to IoT projections—expected IoT devices to surpass 8.4 billion in 2017 and grow to over 20.4 billion by 2020.1 That’s a staggering 143% growth rate over three years. The current global population is 7.6 billion and growing at a comparatively miniscule rate of about 1% per year.2
With IoT devices already outnumbering people, and a projected IoT growth rate that far outpaces global population growth, the Internet is running us now, not the other way around. These devices are being used everywhere for everything—controlling virtually every aspect of our lives. Most of us are so bought into the idea of constant and pervasive “connectedness” that we are becoming the “things” of the Internet, which leads us to the following startling conclusions:
Insecure IoT affects everyone. You don’t have to be able to afford a smart home or own a smartphone to be impacted by compromised IoT devices. The moment you step outside, you can be watched. The CIA spoke about this problem recently, saying compromised wearables and IP cameras were enabling their agents’ locations to be tracked.3 F5 Labs published stories about attacks against IoT devices within the vicinity of President Trump during his meetings with Kim Jung-Un in Singapore and with Putin in Finland. These attacks were likely efforts by both adversaries and friendly nations trying to gain access to those meetings through IP cameras, VoIP phones, or video systems within proximity of the targets of interest. Governments can target anyone from a regular Joe all the way up to a President, Chairman, or Prime Minister. With help from Dutch intelligence services, the UK was able to attribute attacks against its own television stations to Russian operatives by hacking into CCTV cameras, watching the accused Russian operatives’ activities and collecting their keystrokes.4,5
You want privacy? Get off the grid. Governments are deploying IP cameras in major cities for surveillance, allegedly to improve public safety, but many believe they’re there just to spy on civilians. The entire city of Camden, New Jersey has been under surveillance since 2013.6 In the UK, widely regarded as one of the most surveilled countries in the world, Londoners can expect to be monitored through CCTV cameras. In 2012, 300 CCTV cameras were deployed,7 however, the number is probably much higher now. In China, surveillance is welcomed. Citizens like the convenience of purchasing products based on facial recognition and are proud of having a “good citizen” score.8 China also deployed flocks of “doves”—drones in the shape of doves—to spy on its citizens.9 In April 2018, the US Cert issued a warning that Russia was compromising Small Office Home Office (SOHO) routers inside US homes and businesses to spy on civilians, collect data, and use it to inform their social media propaganda.
Human life is at stake. So far, our research in the Hunt for IoT report series has focused on WiFi-connected IoT devices, but there are also cellular-connected IoT devices. These are often gateways into critical infrastructure and equipment that supports human life like police cars, fire trucks, and ambulances; critical Industrial Control Systems (ICSs), and other critical systems that need stable, long-range connectivity. These cellular devices have the same weak access control problems traditional IoT devices have (open to the entire Internet and “protected” with vendor default credentials), and many also provide GPS tracking as they are typically used in fleet vehicles. These devices give away GPS coordinates without authentication. At Black Hat 2018, F5 Labs released this research, which included a video of a police car’s route as the officer drove around throughout the day. Simple pattern recognition can identify a police car and where the officer lives in less than six minutes.
Our homes have been weaponized against us. Outside of the routine use of SOHO routers, DVRs, and IP cameras, things like your TV, oven, refrigerator, Amazon Alexa, Siri and Google Assistant10, Keurig coffee maker (yes, we have attack traffic coming from a Kuerig), and toys11 have been breached and are used to spy, collect data, or launch attacks.
IoT is beating people in the “weakest link” contest. It’s easier to compromise an IoT device exposed to the public Internet and “protected” with (known) vendor default credentials than it is to trick an individual into clicking on a link in a phishing email. Businesses are getting compromised through the unassuming IoT devices they’re using in their networks because the devices are often considered “facilities” devices and are managed by third parties who are not concerned with security, rather than by the organization’s internal corporate IT and security teams. A casino in Europe was breached through the thermostat in its fish tank.12 US retailer Target was breached through its HVAC system.13 A university in the US lost its Internet service after an attack that involved 5,000 devices on its IoT network.14
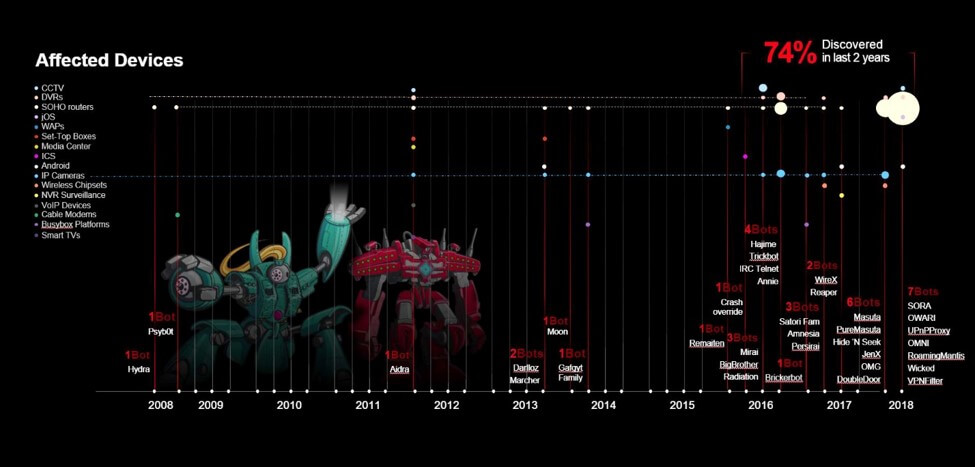
Building multi-purpose attack bots from “things” is popular in the attacker community now. Script kiddies are learning to build bots from YouTube videos and launching damaging DDoS attacks. Seventy-four percent of the thingbots we know about were developed in the last two years. Thirteen thingbots have been discovered in 2018 alone, and they are no longer single- or dual-purpose bots. There has been a shift to multi-purpose attack bots for hire that deploy proxy servers. You can launch any attack of your choice or install other bots using multiple attack options.
The need for secure IoT has never been more critical. We publish where the attacks are coming from (source countries, ASNs, industries, and IP addresses), where the attacks are headed (destination country or region), and the top 50 attacked admin credentials—the credentials attackers use first in brute force attacks—in hopes that the owning entities (primarily telecom companies and hosting providers), will do something about the malicious traffic. We also publish this information so that defenders can use it defensively within their own networks and look for indicators of compromise.
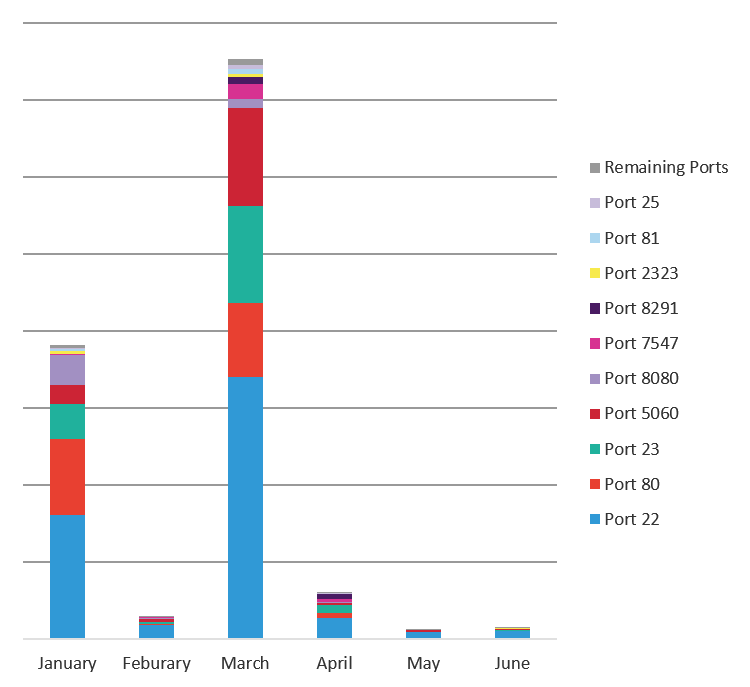
As promised in The Hunt for IoT: The Growth and Evolution of Thingbots (volume 4), we have broadened the scope of attack data collected to include services routinely used by IoT devices (beyond telnet). Twenty of the top ports commonly used by IoT devices are profiled in this report. Here are the key findings from attack data collected from January 1 through June 30, 2018:
- IoT devices are now the number one attack target on the Internet, surpassing web and application servers, email servers, and databases (that shouldn’t be accessible on the Internet).
- As expected, telnet attacks are in decline as we think most of the IoT devices listening on port 23 have already been swept up in existing thingbots.
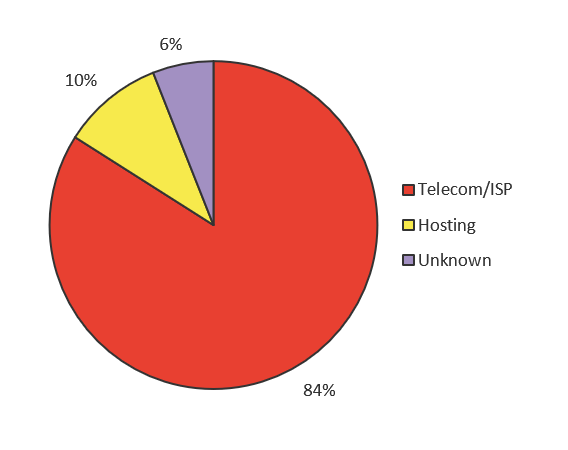
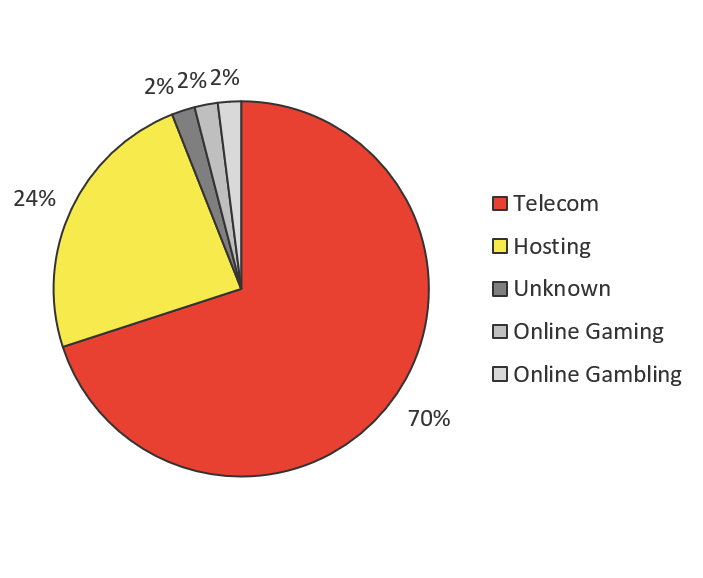
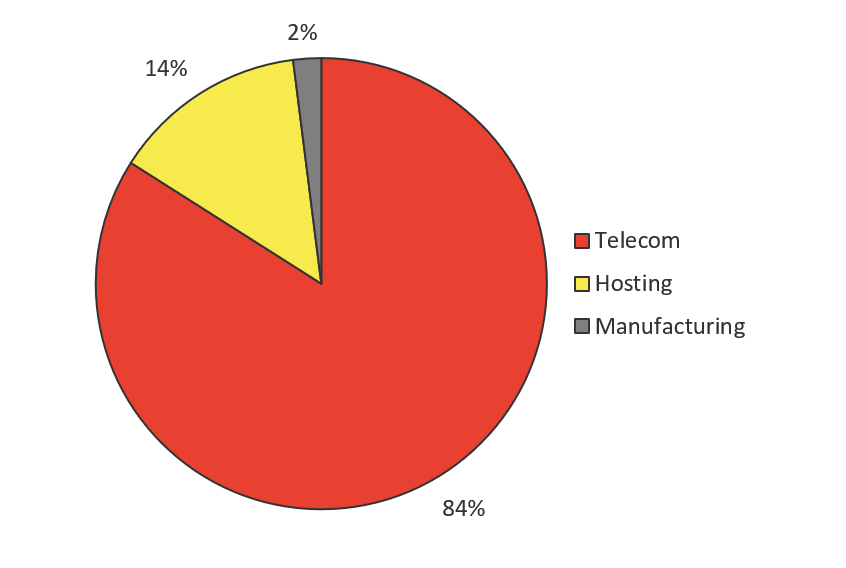
- March saw a large spike in attack traffic that targeted every port we are now tracking related to IoT. Given the industry breakdown of source traffic, 84% of which came from telecom companies, it’s likely this traffic is growth of existing thingbots running off of IoT devices inside telecom networks.
- SSH brute force is the number one attack type targeting IoT devices, followed by telnet.
- IP addresses in Iran and Iraq that we haven’t previously seen attacking jumped into the Top 50 attacking IP addresses list.
- All (100%) of the top 50 attacking IP addresses were new in this period (five ASNs on the top 50 list have had offending IP addresses previously on the top 50 list; the IP addresses used in their networks for this period are new). In The Hunt for IoT, volume 4, we reported that 74% of the top attacking IP addresses were repeat offenders. (Did those infected systems finally get cleaned up, we wonder?)
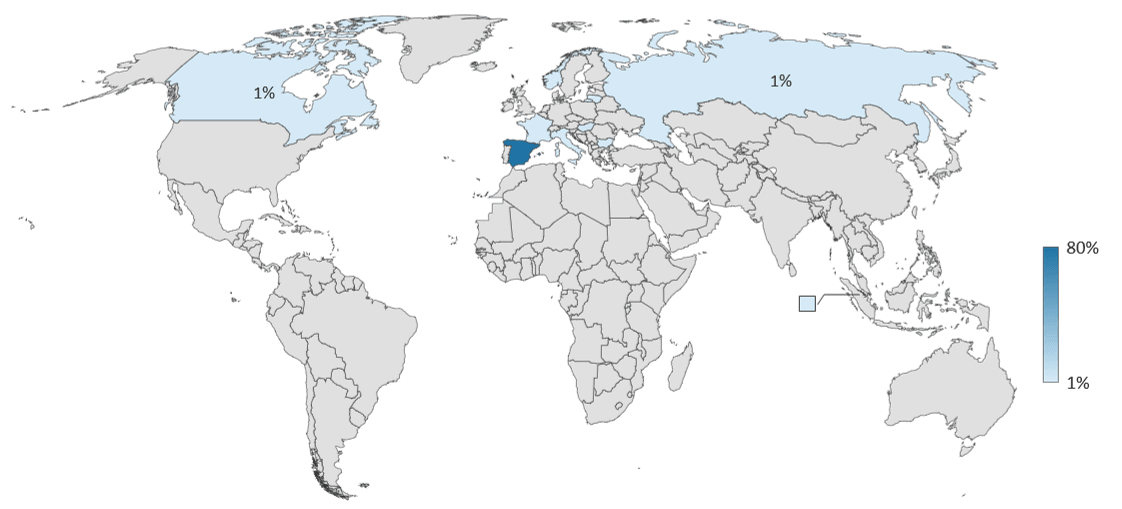
- Spain was the top attacked (destination) country, receiving 80% of the period’s attacks. Spain has been the #1 attacked country for the past year and a half. Clearly, Spain has an IoT security problem.
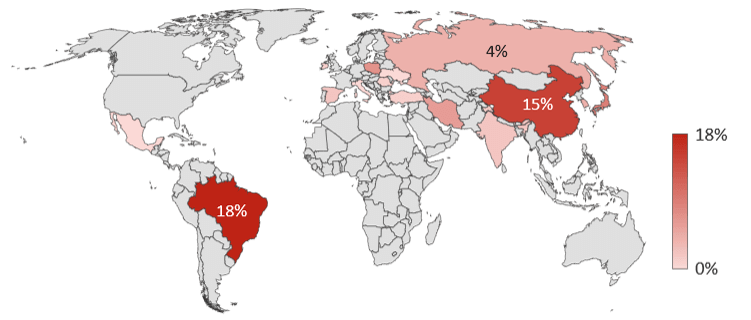
- Brazil was the top attacking (source) country followed by China, Japan, Poland, and the US.
Introduction
Twelve billion new IoT devices are expected to be deployed by 2020. That is an astonishing number. What will these devices be doing? Roughly half of the world’s population has Internet access,15 so there is a lot of room to grow, which means we will continue to see more homes, businesses, and cities lit up with connectivity. We already have Internet-enabled dishwashers, ovens, toasters, fridges, and coffee makers. Verizon recently announced it is opening up 5G residential service that can serve speeds of up to 1 Gbps.16 That’s more than enough bandwidth to support every appliance in your kitchen; entertainment, lighting, and heating systems; smart TVs, gaming systems, DVRs, streaming TV sticks—and likely several computers. Imagine the attack size of a thingbot made from a 1 Gbps home router!
Drones will have their own air space assigned for package delivery and monitoring services. There will be more cameras watching traffic, people, buildings, and homes. Certain types of stores can become completely automated and cashier-less, like the Standard Market17 in San Francisco, which uses security cameras to watch what items customers pick up, and then charge them appropriately. The investment firm behind this operation estimates it will add this technology to 100 stores per month by 2020.
Compromising digital displays has been a popular IoT attack since Defcon in 1999 when hackers changed the hotel displays to show pornographic images. There are many cases of this same kind of hacktivism with freeway displays and digital signs on buildings. In 2016, Chinese hackers allegedly changed the digital displays in Vietnam’s two most popular airports to display propaganda about the South China Sea battle.18 The F5 Labs research project looking into cellular IoT gateways started with an infected airport display at one of the world’s busiest airports. That system had 39 threat actors actively connected who could have changed the airport displays but were instead using the system to launch other attacks. Just last month (September 14–15, 2018), cyber criminals attacked digital displays at the Bristol airport in the UK and installed ransomware. Airport officials chose to not pay the ransom and moved to manual operations for two days, which required handwritten flight schedules. Busier airports would likely not be able to function manually and would pay the ransom to get up and running faster.
Attackers have been busy discovering and infecting as many of those 8.4 billion things as they can. Thirteen thingbots were discovered in the first half of 2018 in comparison to six being discovered in all of 2017, and nine in 2016. We monitor the discovery of thingbots, what types of devices they infect, how they infect the devices, and what attacks they launch to discover patterns. Below is a profile of the 13 thingbots discovered in 2018:
- VPN Filter19 collects credentials, install a network sniffer to monitor ICS protocols, and installs tor nodes.
- Wicked20 targets SOHO routers, CCTV, and DVRs, and installs SORA and OWARI, both of which are rentable bots.21 At the time of its discovery, Wicked was the tenth Mirai spinoff bot.
- Roaming Mantis22 preys on WIFI routers as well as Android and iOS phones, and conducts DNS hijacks and mines cryptocurrency on compromised devices.
- Omni23 compromises GPON home routers to use for crypto-jacking or DDoS attacks.
- UPnProxy24 is sweeping up SOHO routers and installing proxy servers on them that bypass censorship controls; launch spam and phishing campaigns; conduct click fraud, account takeovers, and credit card fraud; launch DDoS attacks; install other bots; and distribute malware.
- OWARI25 compromises SOHO routers and is available as a multi-purpose attack bot for hire.
- SORA26 compromises SOHO routers and is available as a multi-purpose attack bot for hire.
- DoubleDoor27 targets SOHO routers behind Juniper home firewalls, then installs proxy servers from which an attacker can launch any attack of choice.
- OMG28 compromises SOHO routers, wireless IP cameras, and DVRs and then installs proxy servers from which the attacker can launch any attack of choice.
- JenX29 compromises SOHO routers and wireless chipsets from which to launch DDoS attacks. JenX is a DDoS-for-Hire services offering 300Gbps attacks for $20.00.
- Hide’n Seek30 compromises IP cameras. We don’t know what attacks it launches yet.
- Pure Masuta31 compromises home routers. We don’t know what attacks it launches yet.
- Masuta32 compromises home routers and launches DDoS attacks.
The most commonly infected IoT devices, as determined by their participation in bots, are SOHO routers followed by IP cameras, DVRs, and CCTVs.
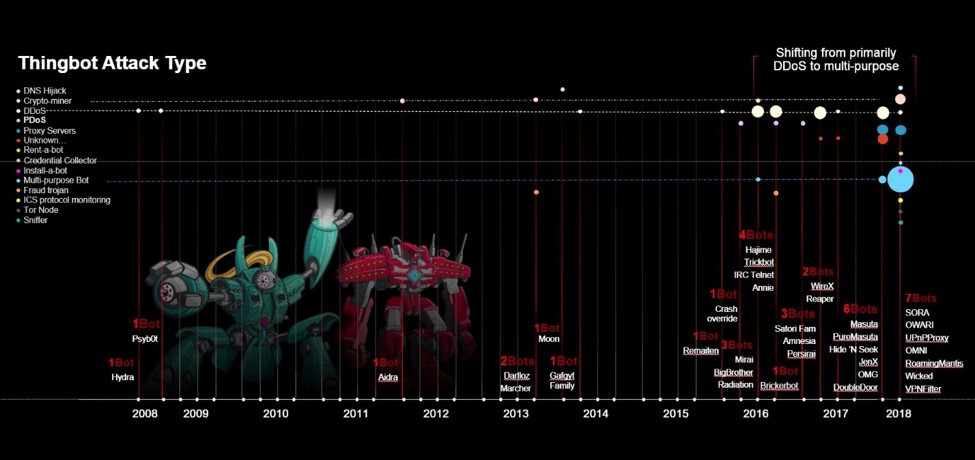
The most common attack type is DDoS, however, in 2018 attackers shifted to multi-purpose attack bots that offer DDoS, among many other attack types, including installing proxy servers to launch any attack, crypto-jacking, installing tor nodes, packet sniffers, launching PDoS attacks, DNS hijacks, credential collection, credential stuffing, and fraud trojans.
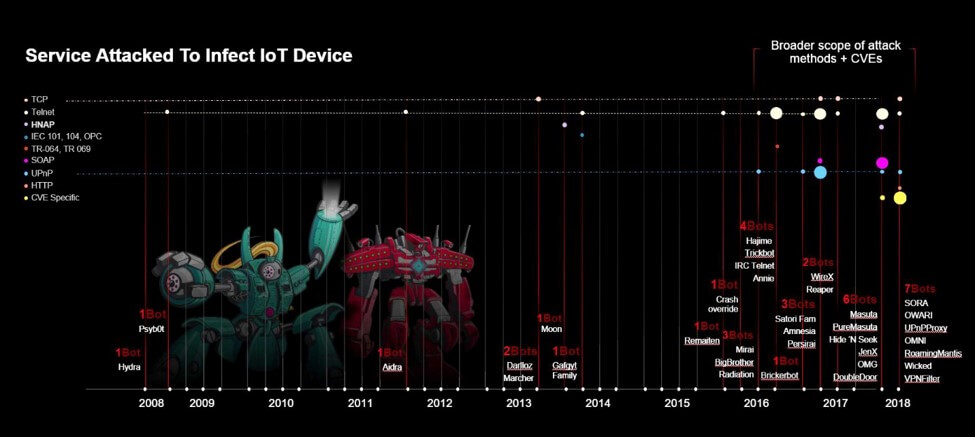
The most common way attackers discover and eventually infect IoT devices with their malware has been through global Internet scans looking for the telent service being open. HNAP, UPnP, SOAP, and CVEs specific to an IoT device manufacuturer are becoming popular, and well as some TCP ports.
Perhaps the most concerning of all is that IoT infrastructure is just as vulnerable to authentication attacks via weak credentials as the IoT devices themselves. In the latest research that investigates cellular IoT devices, F5 Labs, in conjunction with our data partner Loryka, discovered that cellular IoT gateways are just as vulnerable as traditional wired and wireless IoT devices. In fact, 62% of the devices tested were vulnerable to remote access attacks exploiting weak vendor default credentials. These devices act as out-of-band networks, creating network back doors, and have widespread use across the globe.
Loryka has been in ongoing disclosures with over 350 impacted parties, including US city networks, police departments, public utilities, emergency services, SCADA networks, car manufacturers, industrial manufacturers, and major corporations for the past two years. Most of these disclosures received no response. These devices can be exploited and used within thingbots, most specifically, they have been used in Mirai and Reaper,33 but they can also be used to spy, collect data with man-in-the-middle (MiTM) attacks, replace your DNS servers; they can be turned off or reprogramed, causing disruption to the services they are supporting; and they can be used in physical attacks consistent with warfare and terrorism.
62% of the devices tested were vulnerable to remote access attacks exploiting weak vendor default credentials.
Top 20 Attacked IoT Ports
Attacks were collected from the following top 20 services and ports commonly used by IoT devices to gain a big-picture view of IoT-targeted attacks around the world.
| Service | Port | IoT Device Type |
| SSH | Port 22 | *Includes IoT |
| HTTP | Port 80 | Mainly web apps but includes common IoT devices, ICS and gaming consoles |
| Telnet | Port 23 | ALL |
| SIP | Port 5060 | ALL VoIP phones, video conferencing |
| HTTP_Alt | Port 8080 | SOHO routers, smart sprinklers, ICS |
| TR069 | Port 7547 | SOHO routers, gateways, CCTV |
| Applications | Port 8291 | SOHO routers |
| Telnet | Port 2323 | ALL |
| HTTP | Port 81 | *Can include IoT: Wificams |
| SMTP | Port 25 | *Can include IoT: Wificams, Game consoles |
| Rockwell | Port 2222 | ICS |
| HTTP_Alt | Port 8081 | DVRs |
| WSP | Port 9200 | WAPs |
| HTTP_Alt | Port 8090 | WebCams |
| UPnP | Port 52869 | Wireless chipsets |
| Applications | Port 37777 | DVRs |
| UPnP | Port 37215 | SOHO Routers |
| Applications | Port 2332 | Cellular gateways |
| Rockwell | Port 2223 | ICS |
| Secure SIP | Port 5061 | VoIP phones, video conferencing |
Table 1: Top 20 ports used by IoT devices
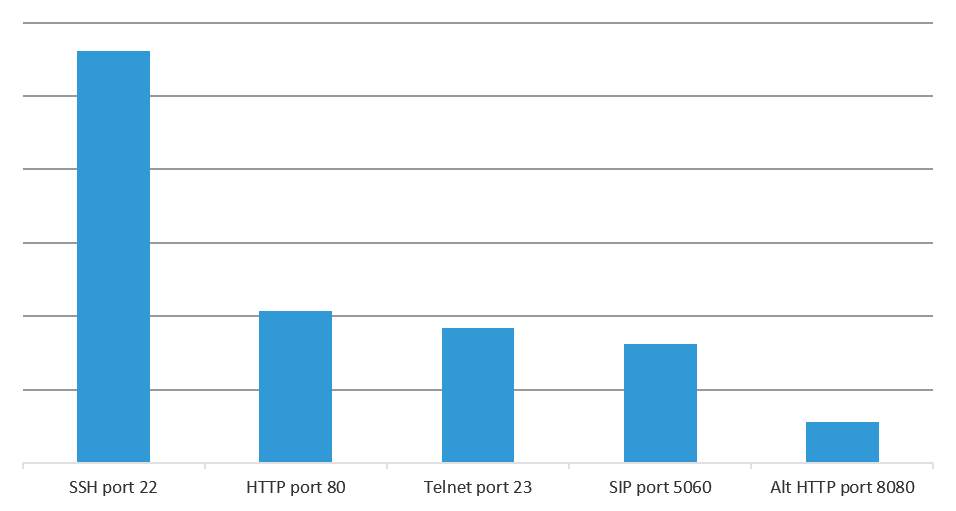
SSH port 22 brute force attacks are the #1 attack type globally, followed by port 80 http web traffic, telnet, SIP port 5060, and then the alternate http port 8080. IoT devices use all of these ports. Many IoT devices have shifted to SSH for remote administration instead of telnet. IoT devices such as SOHO routers, TVs, gaming consoles, and ICSs have been using port 80 for a while now. “Smart” TVs and gaming consoles regularly spin up web servers, which automatically open ports in SOHO routers or firewall using UPnP administration, so check yours! The thingbots Radiation,34 Reaper,35 and Wicked36 all target HTTP ports 80, 81, and 8080.
The chart in Figure 6 compares the top five attacked services: SSH port 22, HTTP port 80, Telnet port 23, SIP port 5060, and the alternate HTTP port 8080. SSH is attacked 2.7 times more often than HTTP. Telnet and SIP are attacked at close to the same rate at HTTP. The fifth most attacked port, 8080, is an alternate HTTP port that is commonly used by SOHO routers, smart sprinklers, and Industrial Control Systems (ICS).
When you combine all the attacks against ports used by IoT devices and attribute a reasonable percentage of the attacks against SSH (20%), HTTP (15%), and SMTP (10%) to IoT attacks (we have no method for determining what percentage of systems using those services are IoT devices, so we made conservative assumptions), that number is greater than 50% of the total attacks. It is reasonable to conclude that “things” are the number one attacked system type on the Internet.Given the growth rate of IoT devices, we expect this to continue to be true and will be monitoring it going forward.
Telnet Attack Trend
Since the first two years of research for our Hunt for IoT report series focused on Telnet attacks, we want to continue showing you the attack trends to give you a picture of the changes in attack sources and destinations over time. (At some point, Telnet attacks will be so small they won’t be worth looking at.)
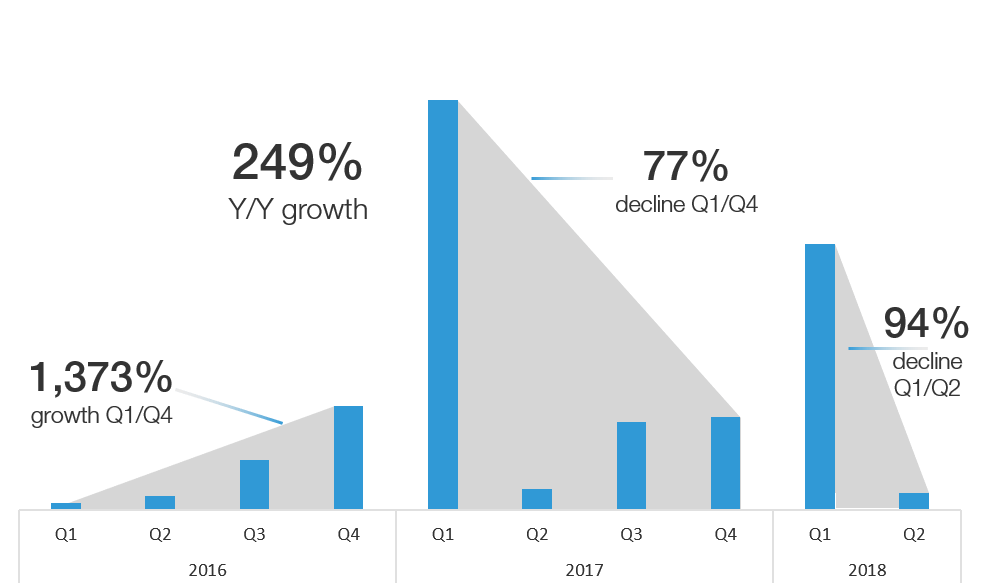
There was a large spike in attack traffic in March 2018 that drove a 94% decline in total attack volume from Q1 2018 to Q2 1018. We are still seeing more attacks against Telnet than when we started this research series in January 2016 but, as we have stated in the last two reports, we expect telnet attacks to trail off as IoT devices move to SSH for remote authentication.
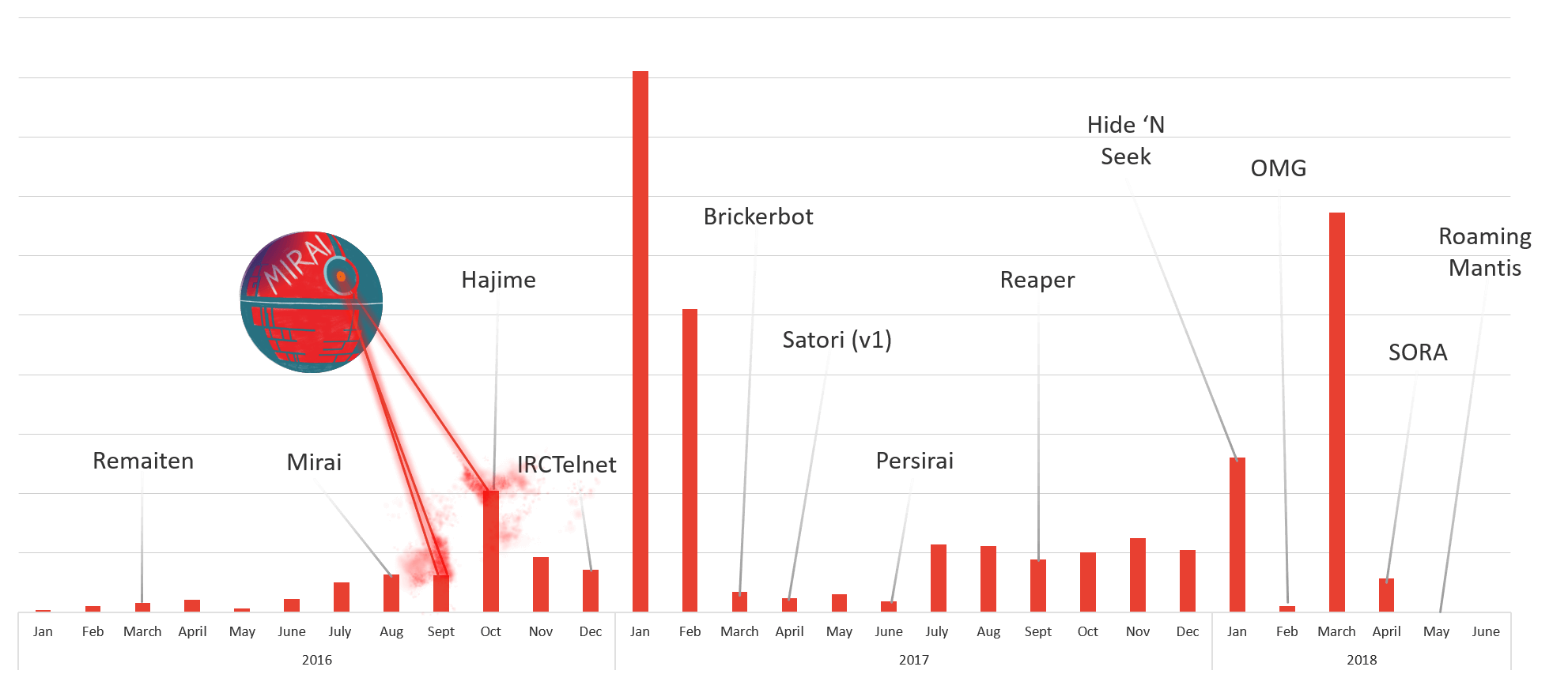
Telnet Attacks Lead to Telnet Thingbots
The chart in Figure 8 compares the telnet attack data we have been collecting with the discovery of thingbots built from initial telnet attacks. We assume the large spikes in attacks are global Internet scans looking for available devices—“recon scans”—followed by targeted attacks that “build” the thingbot. You can see this “recon and build pattern” occur many times over the past two and a half years. The result is the development of at least 12 thingbots (see Figure 8). Worth noting that two of those thingbots—Hajime and Brickerbot—were bots that permanently destroyed IoT devices with the goal of making less IoT devices available for compromise, and ultimately attacking.
Top 10 Attack Destination Countries
Spain has been the number one attacked country since Q1 2017 and received 80% of the attack traffic launched between January 1 and June 30, 2018. Prior to its year and a half long hold as the #1 attacked country, Spain was in the #2 position during Q3 and Q4 2016. We double-checked that the attacks hitting Spain were also hitting other sensors all over the world, and they were. This tells us that the attacks were global and Spain simply had a higher rate of vulnerable responding assets. Clearly, Spain has an IoT security problem, however, we have not yet dedicated cycles to discovering exactly what systems and networks are impacted. If anyone would like to partner on Spain IoT research, please reach out to us!
Hungary has maintained a spot on the top 3 most attacked countries for the past year and a half. The other countries frequently on the top 3 list are the US, Russia, and Singapore.
| Pos | Q3 & Q4 2016 | Q1 & Q2 2017 | Q3 & Q4 2017 | Q1 & Q2 2018 | ||||
| 1 | Russia | 54% | Spain | 5% | Spain | 10% | Spain | 80% |
| 2 | Spain | 29% | Russia | 3% | Hungary | 5% | Hungary | 4% |
| 3 | US | 19% | Hungary | 2% | US | 3% | Singapore | 2% |
| 4 | Turkey | 14% | US | 1% | Singapore | 3% | Bulgaria | 1% |
| 5 | Hong Kong | 8% | Canada | <1% | France | 3% | Norway | 1% |
| 6 | France | 4% | UK | <1% | Italy | 2% | Russia | 1% |
| 7 | Colombia | 4% | Finland | <1% | Canada | 2% | France | 1% |
| 8 | Egypt | 4% | Hong Kong | <1% | Norway | 2% | Italy | 1% |
| 9 | Canada | 3% | Egypt | <1% | UK | 1% | Canada | 1% |
| 10 | UK | 2% | Turkey | <1% | Bulgaria | 1% | Lithuania | <1% |
Table 2: Top 10 attack destination countries over the past two years
Top 10 Attack Source Countries
Traffic originating in Brazil was responsible for the most attacks from January 1 to June 30, 2018 accounting for 18% of the period’s total attack traffic. Brazil typically has a position on the Top 10 attacking countries list but has not been in the top 5 (let alone in the #1 position) for the last two and a half years that we’ve been tracking the Hunt for IoT. Second to Brazil was China, a country that is consistently in the top 3 attack source countries and frequently holds the #1 position.
Attack traffic from Japan made a sizable jump from 1% of the total attack traffic from Q3 and Q4 2017 to 9% of the total attack traffic in Q1 and Q2 2018. Poland’s and Iran’s participation in Q1 and Q2 2018 was also noteworthy, considering both countries have only been on the top 10 list once in the past two and half years, both of which occurred in Q1 and Q2 2017 and accounted for less than 1% of the attacks launched.
| Pos | Q3 & Q4 2016 | Q1 & Q2 2017 | Q3 & Q4 2017 | Q1 & Q2 2018 | ||||
| 1 | China | 29% | Spain | 83% | China | 44% | Brazil | 18% |
| 2 | Russia | 12% | India | <1% | US | 6% | China | 15% |
| 3 | US | 10% | Russia | <1% | Russia | 6% | Japan | 9% |
| 4 | UK | 10% | South Korea | <1% | France | 4% | Poland | 7% |
| 5 | Vietnam | 5% | Seychelles | <1% | Ukraine | 3% | US | 7% |
| 6 | France | 5% | Poland | <1% | Brazil | 3% | Iran | 6% |
| 7 | Brazil | 4% | Iran | <1% | India | 2% | South Korea | 4% |
| 8 | Germany | 4% | China | <1% | Vietnam | 2% | Russia | 4% |
| 9 | Netherlands | 3% | US | <1% | Japan | 1% | India | 2% |
| 10 | South Korea | 2% | Ukraine | <1% | Argentina | 1% | Spain | 2% |
Table 3: Top 10 attack source countries over the past two years
Top 50 Attacking IP Addresses
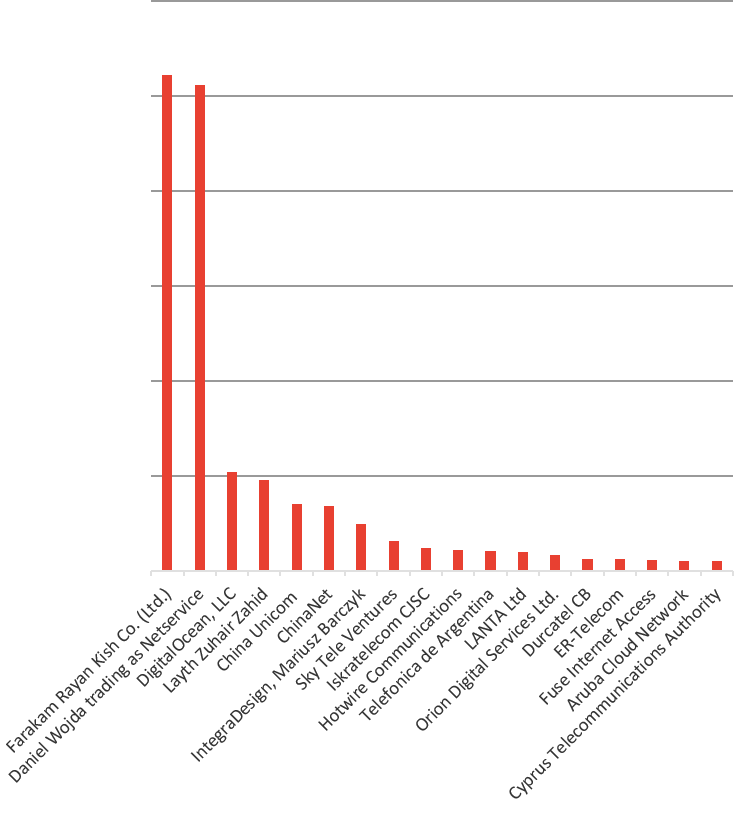
The following list of top 50 attacking IP addresses is in sequential order descending from the top attacking IP address to the least. All of the IP addresses on this list are new, meaning they have not been on the top 50 attacking list in any of our 4 prior reports going back two and a half years. This is a big change from previous reports where we consistently saw the same IP addresses over and over again in the top 50 list.
In Q3 and Q4 2017, 74% of the IP addresses were top attackers in prior reports, 66% of which had consistently been on the top attacking IP list for the two years prior. This consistency was our proof that “things” don’t get cleaned up, both because the devices typically reside in unmanaged and monitored networks, and they often can’t take firmware updates. It is encouraging that those IP addresses are not top attackers anymore! However, this new list is concerning. Either it means there are new top threat actors, or the threat actors are aware they are being watched and have moved their activities to new systems.
Other notable changes in this time period are the introduction of attacking IP addresses in Iran and Iraq.
| Pos | IP Address | IP Owner | Industry | Country | ASN |
| 1 | 185.140.242.49 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 2 | 185.140.242.96 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 3 | 185.140.242.81 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 4 | 185.140.243.12 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 5 | 185.140.100.233 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 6 | 185.140.102.190 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 7 | 185.140.243.95 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 8 | 185.140.100.120 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 9 | 185.140.101.69 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 10 | 167.99.83.206 | DigitalOcean, LLC | Hosting | UK | AS14061 |
| 11 | 185.140.100.9 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 12 | 185.140.241.64 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 13 | 163.177.152.14 | China Unicom Guangdong IP network | Telecom / ISP | China | AS136959 |
| 14 | 218.63.110.81 | ChinaNet-YN | Telecom / ISP | China | AS4134 |
| 15 | 185.140.103.228 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 16 | 185.140.192.41 | Layth Zuhair Zahid | Unknown | Iraq | AS203257 |
| 17 | 185.140.243.111 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 18 | 185.140.192.9 | Layth Zuhair Zahid | Unknown | Iraq | AS203257 |
| 19 | 103.51.35.206 | Sky Tele Ventures | Telecom / ISP | India | AS133972 |
| 20 | 185.140.101.5 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 21 | 222.73.254.215 | China Telecom | Telecom / ISP | China | AS4812 |
| 22 | 185.140.102.156 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 23 | 185.140.101.150 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 24 | 185.140.101.121 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 25 | 185.55.65.59 | IntegraDesign, Mariusz Barczyk | Hosting | Poland | AS61154 |
| 26 | 185.140.101.75 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 27 | 185.55.1.6 | Iskratelecom CJSC | Telecom / ISP | Russia | AS29124 |
| 28 | 185.55.64.183 | IntegraDesign, Mariusz Barczyk | Hosting | Poland | AS61154 |
| 29 | 185.140.101.96 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 30 | 185.140.102.164 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 31 | 174.141.164.8 | Hotwire Communications | Telecom / ISP | US | AS23089 |
| 32 | 181.20.197.168 | Telefonica de Argentina | Telecom / ISP | Argentina | AS22927 |
| 33 | 185.140.102.249 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 34 | 185.140.161.237 | LANTA Ltd | Telecom / ISP | Russia | AS41268 |
| 35 | 67.205.178.243 | DigitalOcean, LLC | Hosting | US | AS14061 |
| 36 | 185.140.194.206 | Layth Zuhair Zahid | Unknown | Iraq | AS203257 |
| 37 | 185.55.202.92 | Orion Digital Services Ltd. | Telecom / ISP | Ireland | AS60155 |
| 38 | 185.140.192.40 | Layth Zuhair Zahid | Unknown | Iraq | AS203257 |
| 39 | 121.23.244.192 | China Unicom 169 Backbone | Telecom / ISP | China | AS4837 |
| 40 | 185.140.102.168 | Daniel Wojda trading as Netservice | Telecom / ISP | Poland | AS203272 |
| 41 | 167.99.1.222 | DigitalOcean, LLC | Hosting | US | AS14061 |
| 42 | 185.140.242.100 | Farakam Rayan Kish Co. (Ltd.) | Telecom / ISP | Iran | AS56815 |
| 43 | 67.205.186.38 | DigitalOcean, LLC | Hosting | US | AS14061 |
| 44 | 185.140.215.116 | Durcatel CB | Telecom / ISP | Spain | AS60807 |
| 45 | 222.161.223.54 | China Unicom 169 Backbone | Telecom / ISP | China | AS4837 |
| 46 | 188.187.188.76 | ER-Telecom | Telecom / ISP | Russia | AS41786 |
| 47 | 50.5.135.150 | Fuse Internet Access | Telecom / ISP | US | AS6181 |
| 48 | 188.166.151.126 | DigitalOcean, LLC | Hosting | UK | AS14061 |
| 49 | 185.12.179.208 | Aruba Cloud Network | Hosting | Germany | AS200185 |
| 50 | 212.31.113.119 | Cyprus Telecommunications Authority | Telecom / ISP | Cypress | AS6866 |
Table 4: Top 50 attacking IP addresses
ASNs of the Top 50 Attacking IP Addresses
Forty of the 50 top attacking IP addresses belong to networks we have not seen attacking previously. Five ASNs on the top 50 list have had offending IP addresses previously on the top 50 list, however, not from the same IP addresses used in their networks during this period. Two networks have been consistently used for the past two and a half years: Chinanet and China Unicom.
The ASN that launched the most attacks from these top 50 IP addresses is AS56815, which belongs to Farakam Rayan Kish Co, an Iranian Telecom/ISP provider. Virtually all of the IP addresses on the list are identified in a Shodan search as MikroTik bandwidth test servers, which we believe to be a bandwidth testing app on consumer MicroTik routers. The use of MicroTik routers in the Reaper and VPNFilter thingbots has been widely reported. Attacks against these devices are covered in our top 20 attacked IoT ports, specifically 8291, shown in Figure 5.
Less is publicly available about the Iraq ASN Layth Zuhair Zahid. We believe it is an ISP, but because we cannot confirm that, we have listed its industry as unknown. Again, Shodan search results for that ASN turn up a lot of MicroTik routers, but nothing specific to the IP addresses in question.
Industries of Top 50 Attacking IP Addresses
The majority of attacks come from Telecom and ISP companies that provide Internet service to homes, small offices and building networks in which the majority of IoT devices reside. Once an IoT device is infected, it is used to scan for other IoT devices to infect—a distributed scanning model most thingbots adopt—and is also used to attack. Because of this, we expect to see Telecom/ISPs generate the majority of IoT attack traffic, and this has been consistently true for the past two and half years.
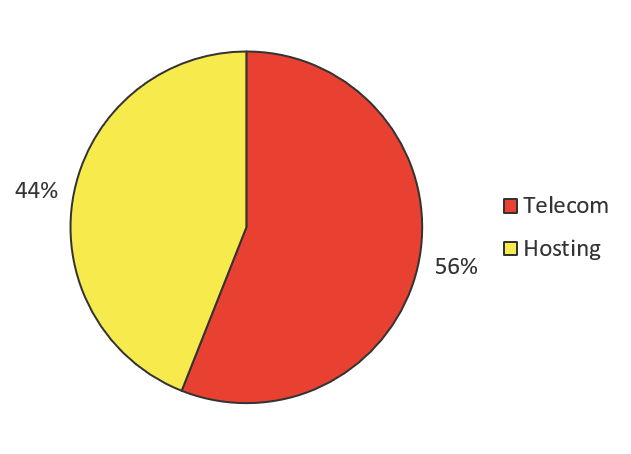
We believe anytime there is a noticeable increase in attack traffic coming from hosting providers, it indicates that attackers are developing new botnets. Attackers rent systems in bulletproof hosting centers to initiate the building of a botnet, and the build efforts are eventually taken over by the infected IoT devices in the Telecom networks. We saw sizeable attack traffic coming from hosting providers in Q3 and Q4 2016 (see Figure 13), and Q1 and Q2 2017 (see Figure 14).
Q3 and Q4 2017 (shown in Figure 15) was not a big period for hosting provider traffic, and neither was the most recent period of Q1 through Q2 2018 (refer to Figure 12). That could mean a few things. One hunch could be that new thingbot development targeting Telnet has slowed down, but it could also mean that new thingbot development is being initiated against other services commonly used by IoT, such as SSH or any of the other ports we listed previously. Given the spike in traffic across all ports (refer to Figure 5), we think the latter hunch is more likely what’s going on.
Global Mirai Infections
Despite Mirai’s infamous reputation as the most powerful thingbot to have launched an attack (as opposed to Reaper, which is more powerful but has not attacked), little has been accomplished to decrease its global footprint. The challenge with dismantling a thingbot is that many infected IoT devices are (1) not capable of taking firmware updates, (2) are owned or operated by people without the technical skills to secure them, or (3) exist within telecom companies that have little incentive to replace them or cut connectivity to infected devices as that would simultaneously terminate their services.
Since the Mirai source code became public, it has been forked at least 10 times in the form of Annie, Satori/Okiru, Persirai, Masuta, Pure Masuta, OMG, SORA, OWARI, Omni, and Wicked. Not only is the threat of the original bot still imminent, but there are at least 10 Mirai stepbrothers and stepsisters to worry about that do more than just launch DDoS attacks. Mirai stepsiblings also deploy proxy servers, mine crypto-currency, install other bots, and are available for rent.
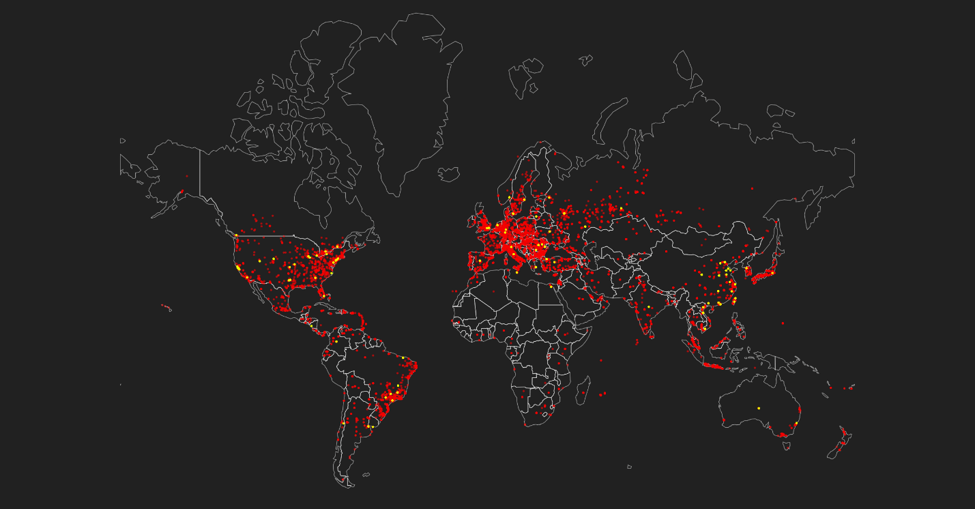
Each dot on the map in Figure 16 represents the latitude and longitude coordinates of a Mirai-infected device. The red dots represent “scanner” nodes that search for other vulnerable IoT devices in which to infect and grow the bot. The yellow dots represent the “malware” hosting systems where the latest updates can be fetched.
The number of Mirai scanner systems across the world decreased slightly from December 2017 to June 2018. There is less concentration of scanner systems in North America, South America, and Asia in June 2018 versus December 2017. Europe is the only region where Mirai scanner infections remained relatively the same from December 2017 to June 2018.
There was a noticeable growth of Mirai malware systems (yellow dots) across the world since our last report covering Mirai growth through December 30, 2017. In December 2017, there were no Mirai malware systems in South America; now there are many. Several new malware systems have popped up across North America and Europe. There were only three Mirai malware systems in southeast Asia in December 2017; now there are at least two dozen. This growth in Mirai malware systems makes sense given the number of Mirai variants in the wild now.
Top 50 Attacked SSH Admin Credentials
We know IoT devices are exploited remotely through weak administrative credentials—typically, vendor defaults. These systems are also susceptible to brute force attacks. Because of this, we started publishing the list of top 50 attacked admin credentials in The Hunt for IoT: The Rise of Thingbots (volume 3) so everyone could ensure these credentials do not exist in their environments. For this report, we are expanding the list to top 100 attacked admin username and password combinations.
Not changing vendor default credentials is a critical mistake when deploying any system. Perhaps just as bad is vendors implementing simple default credentials in the first place. We are making attackers’ jobs too easy. “root:root”, “admin:admin”, “user:user”, “test:test” and “ubuntu:ubutu”—the top 5 most attacked admin credentials—should never be default credentials to begin with. Vendors should expect customers to deploy their products without changing these defaults and start off with something more complex. At a minimum, usernames and passwords should not be identical. Eighty-eight percent of the credentials in the top 50 most attacked list from January 1, 2018 through June 30, 2018 have the same username as the password as compared to 87% in the prior six-month period, and 96% in the six-month period before that.
| 1 - 50 | User Name | Password | 51 - 100 | User Name | Password |
| 1 | root | root | 51 | manager | manager123 |
| 2 | admin | admin | 52 | teamspeak3 | teamspeak3 |
| 3 | user | user | 53 | nobody | nobody |
| 4 | test | test | 54 | csgoserver | csgoserver |
| 5 | ubuntu | ubuntu | 55 | test2 | test2 |
| 6 | ubnt | ubnt | 56 | demo | demo |
| 7 | support | support | 57 | 0 | |
| 8 | oracle | oracle | 58 | a | a |
| 9 | pi | raspberry | 59 | minecraft | minecraft |
| 10 | Guest | guest | 60 | alex | q1w2e3r4t5 |
| 11 | postgres | postgres | 61 | postfix | postfix |
| 12 | ftpuser | asteriskftp | 62 | glassfish | glassfish |
| 13 | usuario | usuario | 63 | jboss | jboss |
| 14 | nagios | nagios | 64 | master | master |
| 15 | 1234 | 1234 | 65 | ghost | ghost |
| 16 | ftp | ftp | 66 | vnc | vnc |
| 17 | operator | operator | 67 | info | info |
| 18 | git | git | 68 | 111111 | 856149100 |
| 19 | hadoop | hadoop | 69 | debian | debian |
| 20 | ts3 | ts3 | 70 | centos | centos |
| 21 | teamspeak | teamspeak | 71 | testuser | testuser |
| 22 | mysql | mysql | 72 | system | sytem |
| 23 | tomcat | tomcat | 73 | www-data | www-data |
| 24 | service | service | 74 | test1 | test1 |
| 25 | butter | xuelp123 | 75 | upload | upload |
| 26 | ts | ts | 76 | plcmspip | plcmspip |
| 27 | bot | bot | 77 | weblogic | weblogic |
| 28 | deploy | deploy | 78 | redhat | redhat123456 |
| 29 | monitor | monitor | 79 | developer | developer |
| 30 | administrator | administrator | 80 | public | public |
| 31 | bin | bin | 81 | student | student |
| 32 | default | nopass | 82 | webmaster | webmaster |
| 33 | adm | adm | 83 | osmc | osmc |
| 34 | vagrant | vagrant | 84 | c | c |
| 35 | anonymous | any@ | 85 | server | server |
| 36 | uucp | uucp | 86 | supervisor | supervisor |
| 37 | www | www | 87 | 22 | backup |
| 38 | jenkins | jenkins | 88 | hdfs | hdfs |
| 39 | apache | apache | 89 | linux | linux |
| 40 | sshd | sshd | 90 | postmaster | postmaster |
| 41 | PlcmSpIp | PlcmSpIp | 91 | csserver | csserver |
| 42 | cisco | cisco | 92 | prueba | prueba |
| 43 | sinusbot | sinusbot | 93 | matt | matt |
| 44 | user1 | user1 | 94 | vyatta | vyatta |
| 45 | backup | backup | 95 | hduser | hduser |
| 46 | Management | TestingR2 | 96 | nexus | nexus |
| 47 | steam | steam | 97 | ethos | live |
| 48 | mother | f0cker | 98 | Admin | Admin |
| 49 | dev | dev | 99 | mc | mc |
| 50 | zabbix | zabbix | 100 | telnet | telnet |
Figure 18: Top 100 attacked admin credentials
Just for Fun: Keurig Attacks!
To prove that IoT security is abysmal and that attackers will find a way to use any “thing” (and because there is a Hyper Text Coffee Pot Control Protocol RFC232437—yes, really!), here are some attack logs from a Keurig coffee maker.
{ "_id" : { "protocol" : "http", "timestamp" : { "$date" : "2018-07-19T20:31:04.000-0700" }, "source_ip" : "185.112.249.24", "session_http" : { "request" : { "body" : "", "header" : [ [ "accept", "*/*" ], [ "user-agent", "Keurig K575 Coffee Maker" ] ], "verb" : "GET", "path" : "/" } }, "source_port" : 56946, "destination_port" : 80, }
{ "_id" : { "protocol" : "http", "timestamp" : { "$date" : "2018-07-23T12:16:41.000-0700" }, "source_ip" : "185.112.249.24", "session_http" : { "request" : { "body" : "", "header" : [ [ "accept", "*/*" ], [ "user-agent", "Keurig K575 Coffee Maker" ] ], "verb" : "GET", "path" : "/" } }, "source_port" : 49180, "destination_port" : 80, }
{ "_id" : { "protocol" : "http", "timestamp" : { "$date" : "2018-07-25T10:04:52.000-0700" }, "source_ip" : "185.112.249.24", "session_http" : { "request" : { "body" : "", "header" : [ [ "accept", "*/*" ], [ "user-agent", "Keurig K575 Coffee Maker" ] ], "verb" : "GET", "path" : "/" } }, "source_port" : 40755, "destination_port" : 80, }
{ "_id" : { "protocol" : "http", "timestamp" : { "$date" : "2018-07-25T10:14:46.000-0700" }, "source_ip" : "185.112.249.24", "session_http" : { "request" : { "body" : "", "header" : [ [ "accept", "*/*" ], [ "user-agent", "Keurig K575 Coffee Maker" ] ], "verb" : "GET", "path" : "/" } }, "source_port" : 40755, "destination_port" : 80, }
{ "_id" : {"protocol" : "http", "timestamp" : { "$date" : "2018-07-28T06:29:53.000-0700" }, "source_ip" : "185.112.249.28", "session_http" : { "request" : { "body" : "", "header" : [ [ "accept", "*/*" ], [ "user-agent", "Keurig K575 Coffee Maker" ] ], "verb" : "GET", "path" : "/" } }, "source_port" : 50225, "destination_port" : 80, }
Conclusion
We have reached a point of no return when it comes to deployed IoT devices, their existing security standards (or lack thereof), and the inability to do anything about their security worldwide. We are stuck with the over 8 billion deployed devices around the world that, for the most part, prioritize access convenience over security. We don’t know what percentage of the 8+ billion IoT devices are vulnerable, but the percentage of vulnerable of cellular gateways—62%—“protecting” critical systems like police cars, firetrucks, and airport operations is a good metric to start with. Theoretically, security increases with the criticality of the system, and you could assume that more attention would have been paid to securing critical cellular gateways than home routers, IP cameras, and TVs. But 62% of the total IoT population is 5 billion devices. The additional 12 billion IoT devices that will be going live by 2020 were likely developed over the past few years with the same absence of security standards:
- Remote administration is open to the entire Internet (IP tables, ACLs, firewall rules not in place).
- Whether it’s SSH or Telnet, the administrator username and password is typically left as vendor default, which all attackers know (see Figure 18).
- Account lockouts after a certain number of failed login attempts is not set, so admin accounts can be brute-forced.
- Rate limiting, which could prevent DDoS attacks, is not in place.
Twelve billion new devices can’t go live on IPv4; there just simply isn’t enough IPv4 space left. Implementors will be forced to use NAT (which is a good thing), move to cellular and the further adoption of 5G, and move to IPv6, which will introduce additional complexity and security issues.
Organizations need to brace themselves for impact, because the attacker opportunity with IoT is virtually endless, and building thingbots is now popular. We expect the IoT attacks we are watching to be building new thingbots and growing the size of thingbots already discovered. Organizations need to be prepared for thingbot attacks by having security controls in place that can detect the bot and scale to the rate at which thingbots can attack. Having bot defense at your application perimeter is crucial, as well as having a scalable DDoS solution.
Attackers will eventually figure out what systems they are infecting, and then build purposeful bots. It’s important to keep in mind that, for the most part, attackers looking to build sizeable bots to launch attacks don’t know what types of systems they have taken over, or who owns them. It’s a numbers game—“who” and “what” is irrelevant to them. They are casting the widest net possible, to catch as many systems as possible, to make the most powerful bot possible. Sierra Wireless, the largest manufacturer of cellular IoT devices issued a Mirai alert, warned customers to reset their default admin credentials. One would assume they issued that alert because their devices were getting infected. Imagine attackers (operating any one of the 10 Mirai spinoff bots that we are aware of) purposely and consciously using their access to a police car to launch physically disruptive attacks instead of unknowingly using equipment in police cars to launch DDoS attacks? Attackers are smart, and the good ones love to automate. We expect them to fingerprint device types and customize their reconnaissance missions and scans to build purpose-built attack bots optimized by the types of devices they infect and what attacks those devices are best at. In the future, we expect:
- Crypto-jacking to rise on IoT systems that are good at processing data like SOHO routers, gaming consoles, and others.
- Ransomware attacks to grow against IoT systems controlling a critical function where the owner is more likely to pay the ransom (industrial control systems, airports, hospitals, casinos, ATMs, etc.).
- More targeting of IoT systems that are network back doors like cellular gateways (especially in fleet vehicles), HVAC systems, thermostats, IP cameras, vending machines, coffee makers—all the “things” you never think might have Internet access. Compromised devices are then used to spy and steal data and intellectual property (IP).
- Spyware targeting industrial control systems (could be foreign adversarial or friendly data gathering).
- Targeted warfare attacks against critical industrial control systems by nation-states, including physical attacks and spying.
It’s going to take material loss of revenue for IoT device manufacturers, or significant costs incurred by organizations who implement these devices before any meaningful IoT security is achieved. If and when the world wakes up and starts to demand stringent security for IoT devices, the availability of IoT systems to infect will decrease and make the attacker market more competitive. At that point, the attack-bot-for-hire cybercrime economy will mature where bots are valued based on the IoT device types in the bot and what attacks they are good for, similar to the way the stolen PII market matured when certain card types or IDs in certain countries were worth more than others.
For now, every company needs to prepare themselves for thingbot attacks, every business and government entity with IoT devices deployed should be securing them, and every person should be securing their home. The recommendations on what to do have been the same since we started this report series. Refer to the checklist in the conclusion of The Hunt for IoT: The Growth and Evolution of Thingbots (volume 4) for a comprehensive list.